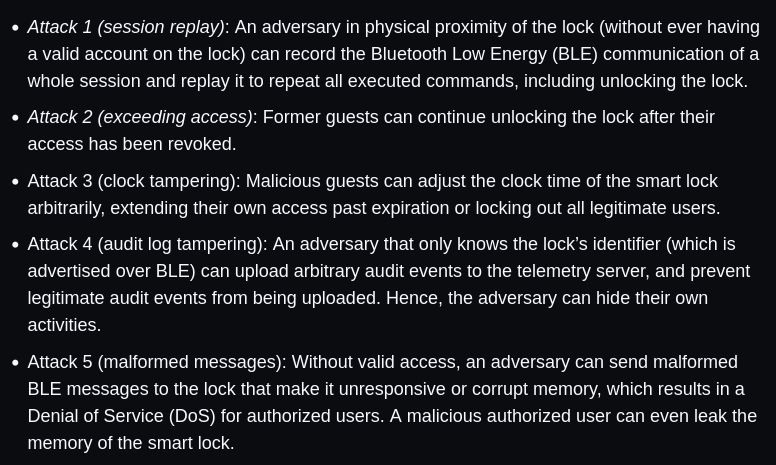
Giacomo Fenzi
@giacomofenzi.bsky.social
480 followers
96 following
48 posts
PhD student @EPFL, previously @ETH
Interested in cryptography at large, post quantum and interactive proofs in particular.
Interista alla Prisco.
Posts
Media
Videos
Starter Packs
Giacomo Fenzi
@giacomofenzi.bsky.social
· Aug 14
Giacomo Fenzi
@giacomofenzi.bsky.social
· Aug 12
Giacomo Fenzi
@giacomofenzi.bsky.social
· Aug 12
Giacomo Fenzi
@giacomofenzi.bsky.social
· Aug 12
Reposted by Giacomo Fenzi
Giacomo Fenzi
@giacomofenzi.bsky.social
· Jul 23
Giacomo Fenzi
@giacomofenzi.bsky.social
· Jul 22
Giacomo Fenzi
@giacomofenzi.bsky.social
· Jul 22
Giacomo Fenzi
@giacomofenzi.bsky.social
· Jul 22
Giacomo Fenzi
@giacomofenzi.bsky.social
· Jul 22
Giacomo Fenzi
@giacomofenzi.bsky.social
· Jul 22

Hash-Based Multi-Signatures for Post-Quantum Ethereum
With the threat posed by quantum computers on the horizon, systems like Ethereum must transition to cryptographic primitives resistant to quantum attacks. One of the most critical of these primitives ...
ia.cr
Giacomo Fenzi
@giacomofenzi.bsky.social
· Jul 22
Giacomo Fenzi
@giacomofenzi.bsky.social
· Jul 22
Giacomo Fenzi
@giacomofenzi.bsky.social
· May 28
Reposted by Giacomo Fenzi
Giacomo Fenzi
@giacomofenzi.bsky.social
· May 15