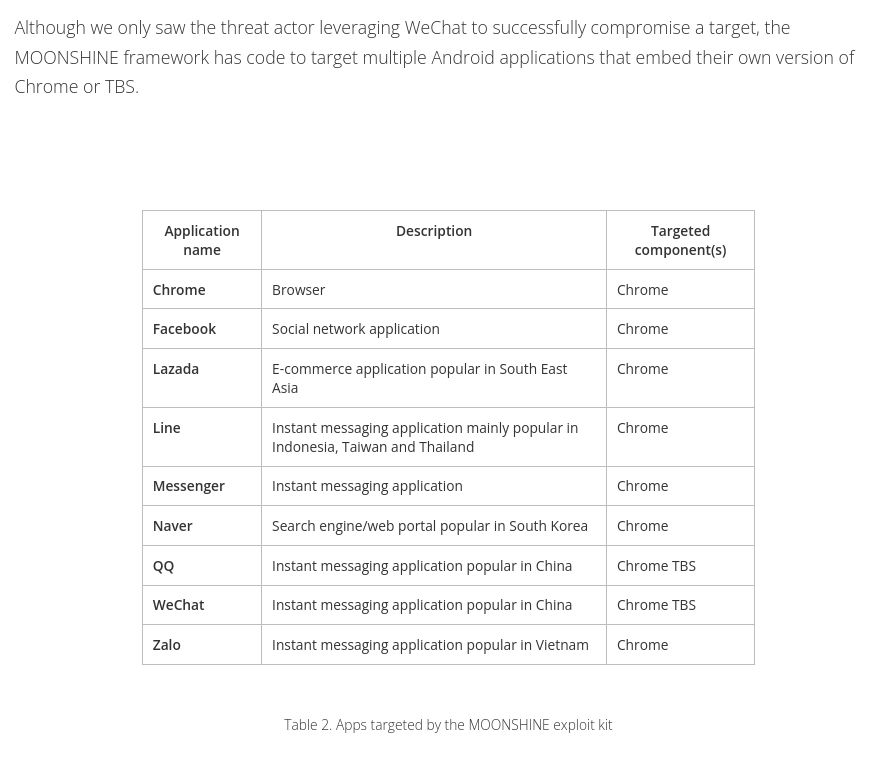
Daniel Lunghi
@thehellu.bsky.social
150 followers
83 following
7 posts
Threat researcher at Trend Micro mostly focused on APT
Posts
Media
Videos
Starter Packs
Pinned
Daniel Lunghi
@thehellu.bsky.social
· Jan 29

China : Chinese firm behind hacking operations against Uyghurs and Tibetans unveiled
Intelligence Online has established a link between a Chinese public security ministry contractor and recent IT hacking operations carried out in China and abroad against the two minorities, reviled
www.intelligenceonline.com
Reposted by Daniel Lunghi