
Read more: censys.com/blog/ics-ira...

Read more: censys.com/blog/ics-ira...
----
June 21 marked lowest visibility—but signs of recovery.
📉 Some networks (e.g., DATAK, HAMYAR-AS) remain unstable.
📈 Others (e.g., RESPINA-AS, MOBINNET-AS) are bouncing back strong.
View at #Censys: censys.com/blog/irans-i...

----
June 21 marked lowest visibility—but signs of recovery.
📉 Some networks (e.g., DATAK, HAMYAR-AS) remain unstable.
📈 Others (e.g., RESPINA-AS, MOBINNET-AS) are bouncing back strong.
View at #Censys: censys.com/blog/irans-i...
👀 censys.com/blog/poking-...

👀 censys.com/blog/poking-...

We also show how to use this information to create a set of IOCs for defensive measures: censys.com/blog/unmaski...

We also show how to use this information to create a set of IOCs for defensive measures: censys.com/blog/unmaski...
www.censys.com/blog/interne...
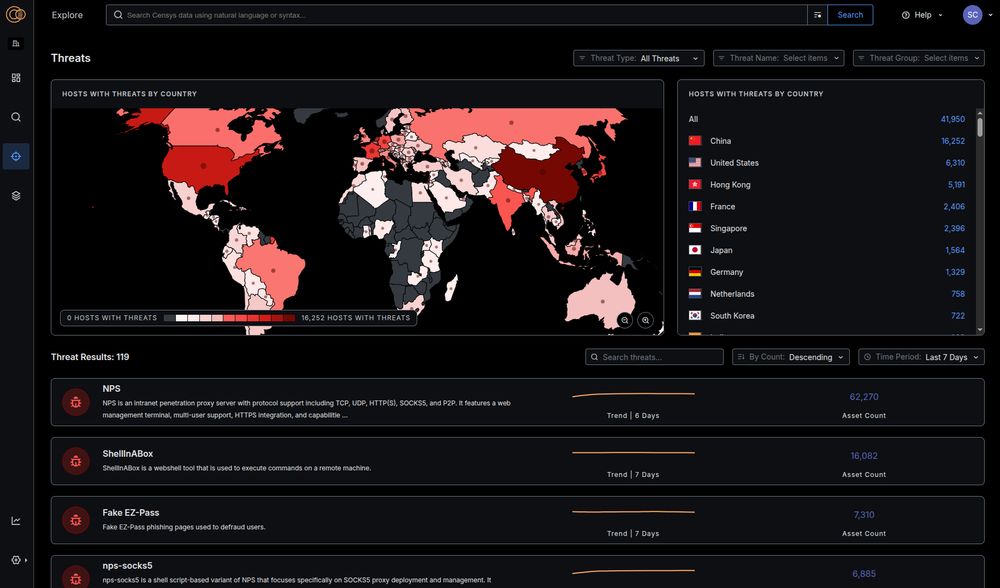
www.censys.com/blog/interne...
https://censys.com/blog/turning-off-the-information-flow-working-with-the-epa-to-secure-hundreds-of-exposed-water-hmis
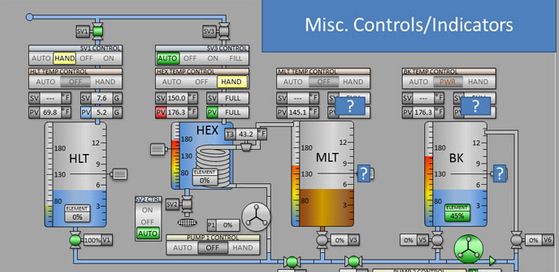



censys.com/blog/the-imp...

censys.com/blog/the-imp...
youtu.be/vK4iYy_A130?...

youtu.be/vK4iYy_A130?...
youtu.be/vK4iYy_A130?...

youtu.be/vK4iYy_A130?...
The Censys Threat Module:
⏱️ Speeds up investigations
🌐 Surfaces enriched threat context
📈 Enables real-time pivoting
Act faster. Hunt smarter. See how: censys.com/blog/speedin...

The Censys Threat Module:
⏱️ Speeds up investigations
🌐 Surfaces enriched threat context
📈 Enables real-time pivoting
Act faster. Hunt smarter. See how: censys.com/blog/speedin...


youtu.be/OcUcBcizXas?...

censys.com/blog/google-...

censys.com/blog/google-...
censys.com/blog/google-...

censys.com/blog/google-...


censys.com/blog/scoutin...

censys.com/blog/scoutin...



