youtu.be/VgWSUKVUUfU
youtu.be/VgWSUKVUUfU

youtu.be/VgWSUKVUUfU



I highly recommend it!
#osint #cyb3rint3l #cybersecurity #osintseries #digitalfootprint #infosec #spiderfoot #reconnaissance #shodan #virustotal




I highly recommend it!
#osint #cyb3rint3l #cybersecurity #osintseries #digitalfootprint #infosec #spiderfoot #reconnaissance #shodan #virustotal
https://deadstack.net/cluster/11364
🔗🔥 Stories follow in replies.
#tech #opensource #infosec #government #cybersecurity
https://deadstack.net/cluster/11364
🔗🔥 Stories follow in replies.
#tech #opensource #infosec #government #cybersecurity
❌ You haven't trained your users
❌ You save RDP credentials on the client
❌ Force UNC paths to remember login details
❌ You lack a Patch Management strategy
❌ You are not incorporating Monitoring
❌ You assume you are too small to be hit
❌ You haven't trained your users
❌ You save RDP credentials on the client
❌ Force UNC paths to remember login details
❌ You lack a Patch Management strategy
❌ You are not incorporating Monitoring
❌ You assume you are too small to be hit
Join me in the 1st part of this three-part Threat Hunting series, where I delve into Process Explorer, showing how we can further expand our DFIR arsenal by fine-tuning this Sysinternals tool.


Join me in the 1st part of this three-part Threat Hunting series, where I delve into Process Explorer, showing how we can further expand our DFIR arsenal by fine-tuning this Sysinternals tool.
socradar.io/reflections-...

socradar.io/reflections-...
Windows Millennium Edition, or ME, arrived in 2000, aiming to bring multimedia & home computing together.
It brought System Restore, digital media support, faster boot times, but also bugs &headaches.
Often criticised as one of MS's weakest releases, ME became (1/2)

Windows Millennium Edition, or ME, arrived in 2000, aiming to bring multimedia & home computing together.
It brought System Restore, digital media support, faster boot times, but also bugs &headaches.
Often criticised as one of MS's weakest releases, ME became (1/2)
Released in 1998, Windows 98 refined the Win 95 experience with better hardware support, the Quick Launch bar & the Active Desktop.
It was the OS where the early web took off, with IE embedded.
But it was also the golden age for viruses (1/2)

Released in 1998, Windows 98 refined the Win 95 experience with better hardware support, the Quick Launch bar & the Active Desktop.
It was the OS where the early web took off, with IE embedded.
But it was also the golden age for viruses (1/2)
Building on the foundation set by Windows 3.1, which introduced many to GUIs, Windows 95 launched in 1995 and took digital innovation to new heights.
With the iconic Start button and Plug-and-Play simplicity, Windows 95 opened the gateway to the (1/2)

Building on the foundation set by Windows 3.1, which introduced many to GUIs, Windows 95 launched in 1995 and took digital innovation to new heights.
With the iconic Start button and Plug-and-Play simplicity, Windows 95 opened the gateway to the (1/2)
Arriving in 1992, Windows 3.1 introduced millions to the world of GUIs with its polished look, iconic Program Manager, TrueType fonts and... Minesweeper!💣
It made computing colourful, structured, and... fun.
But it also saw early vulnerabilities emerge as (1/2)

Arriving in 1992, Windows 3.1 introduced millions to the world of GUIs with its polished look, iconic Program Manager, TrueType fonts and... Minesweeper!💣
It made computing colourful, structured, and... fun.
But it also saw early vulnerabilities emerge as (1/2)
Released in 1987, Windows 2.0 introduced overlapping windows, desktop icons & better graphics support, making the interface more dynamic.
It powered early business applications & famously introduced keyboard shortcuts still used today. For many, it was their 1st time (1/2)

Released in 1987, Windows 2.0 introduced overlapping windows, desktop icons & better graphics support, making the interface more dynamic.
It powered early business applications & famously introduced keyboard shortcuts still used today. For many, it was their 1st time (1/2)
Launched in 1985, Windows 1.0 was Microsoft's 1st step into the GUI world, layering windows on top of MS-DOS.
It planted the seed for personal computing with tiled windows, mouse support & basic multitasking, including (1/2)

Launched in 1985, Windows 1.0 was Microsoft's 1st step into the GUI world, layering windows on top of MS-DOS.
It planted the seed for personal computing with tiled windows, mouse support & basic multitasking, including (1/2)
Coinbase (correctly) refused to pay the cybercriminals a $20M ransom. Instead, in a chess-type move, they offered a $20M bounty as a reward for intel provided.
Nevertheless, this further ignites the KYC discussion. #ransomware
Coinbase (correctly) refused to pay the cybercriminals a $20M ransom. Instead, in a chess-type move, they offered a $20M bounty as a reward for intel provided.
Nevertheless, this further ignites the KYC discussion. #ransomware
Here's the PoC and why your once moaning executive will thank you later for keeping trade secrets safe: www.youtube.com/watch?v=_7e_...
#Cybersecurity
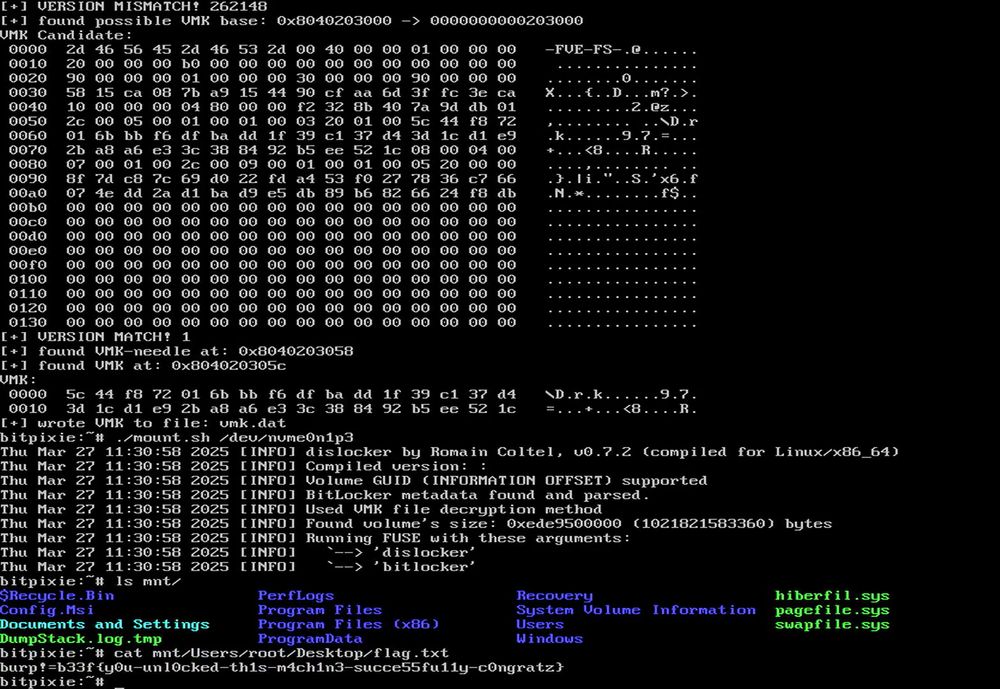
Here's the PoC and why your once moaning executive will thank you later for keeping trade secrets safe: www.youtube.com/watch?v=_7e_...
#Cybersecurity
I've been following Thomas for the last 8 years & I find his commitment & contribution to the IT community outstanding.
Some events in life we should take as warnings. This is one of them.
I've been following Thomas for the last 8 years & I find his commitment & contribution to the IT community outstanding.
Some events in life we should take as warnings. This is one of them.
The EU Vulnerability Database (EUVD) is now live.
The EU is (finally) moving from theory to practice and that’s a win in protecting the critical infrastructure.🔐
✅ Supports NIS2 requirements
✅ Helps with supply chain & vuln mgmt
1/2
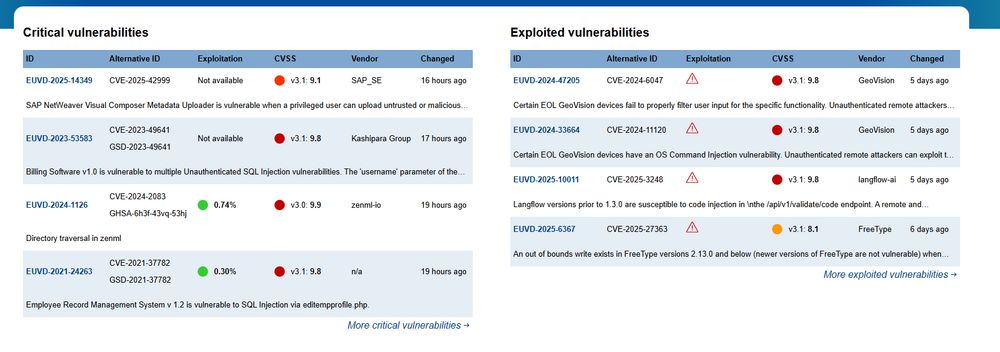
The EU Vulnerability Database (EUVD) is now live.
The EU is (finally) moving from theory to practice and that’s a win in protecting the critical infrastructure.🔐
✅ Supports NIS2 requirements
✅ Helps with supply chain & vuln mgmt
1/2
Often, organisations tend to chase certificates while neglecting their security posture.
Paperwork aside, we need to invest in:
📌Incident response
📌 Continuous monitoring
📌 Threat modelling
📌 Security culture
Often, organisations tend to chase certificates while neglecting their security posture.
Paperwork aside, we need to invest in:
📌Incident response
📌 Continuous monitoring
📌 Threat modelling
📌 Security culture

🚫 Encourages more attacks
🚫 Funds criminal operations
🚫 Provides no guarantee of data restoration or non-disclosure
Instead:
✅Invest in proper IR
✅Test backups
✅Build resilience, not reliance on hope

🚫 Encourages more attacks
🚫 Funds criminal operations
🚫 Provides no guarantee of data restoration or non-disclosure
Instead:
✅Invest in proper IR
✅Test backups
✅Build resilience, not reliance on hope