
But they aren't removing the underlying WMI framework, so threat actors will have to use PowerShell to access WMI.
🔗 techcommunity.microsoft.com/blog/windows...
#IncidentResponse #ThreatDetection #ThreatIntel #CSIRT #CERT

But they aren't removing the underlying WMI framework, so threat actors will have to use PowerShell to access WMI.
🔗 techcommunity.microsoft.com/blog/windows...
#IncidentResponse #ThreatDetection #ThreatIntel #CSIRT #CERT
You think they might also let the victim use it for responding to the compromise as well? 😂
news.sophos.com/en-us/2025/0...
#DFIR #IncidentResponse #ThreatDetection #ThreatIntel

You think they might also let the victim use it for responding to the compromise as well? 😂
news.sophos.com/en-us/2025/0...
#DFIR #IncidentResponse #ThreatDetection #ThreatIntel
Datadog's Security Labs identified an abuse of Office 365 Exchange Online service principal (SP) allowing escalation to Global Admin. MSRC considers it "expected misconfiguration" so don't expect a fix.
🔗 securitylabs.datadoghq.com/articles/i-s...
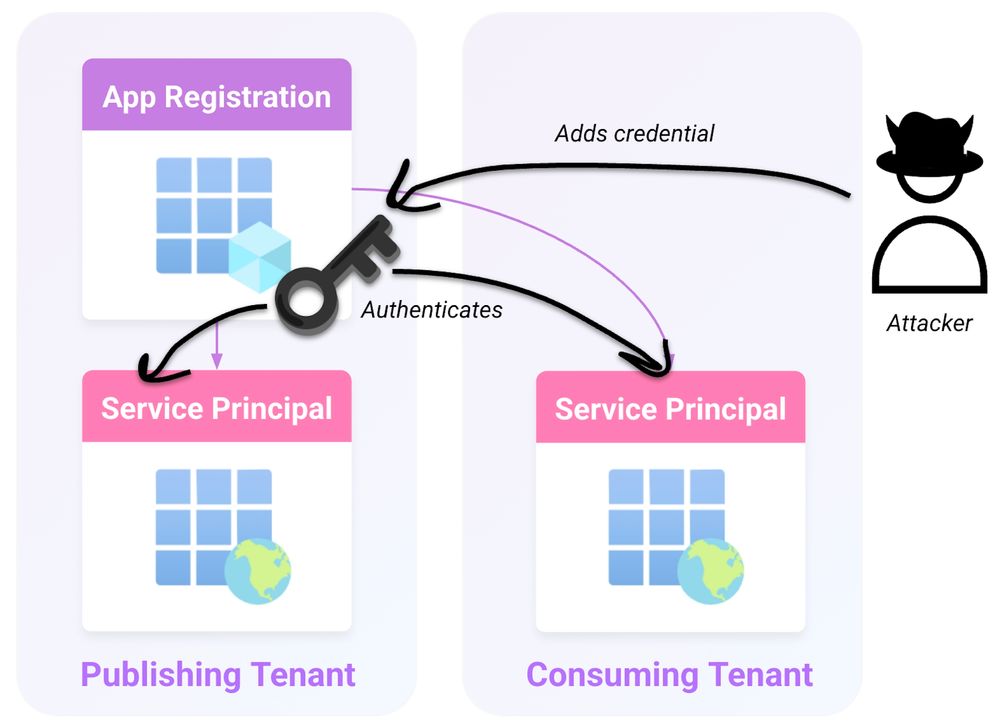
Datadog's Security Labs identified an abuse of Office 365 Exchange Online service principal (SP) allowing escalation to Global Admin. MSRC considers it "expected misconfiguration" so don't expect a fix.
🔗 securitylabs.datadoghq.com/articles/i-s...
www.bleepingcomputer.com/news/securit...
#IncidentReponse #DataBreach #CSIRT

www.bleepingcomputer.com/news/securit...
#IncidentReponse #DataBreach #CSIRT
🔗 www.darktrace.com/blog/obfusca...
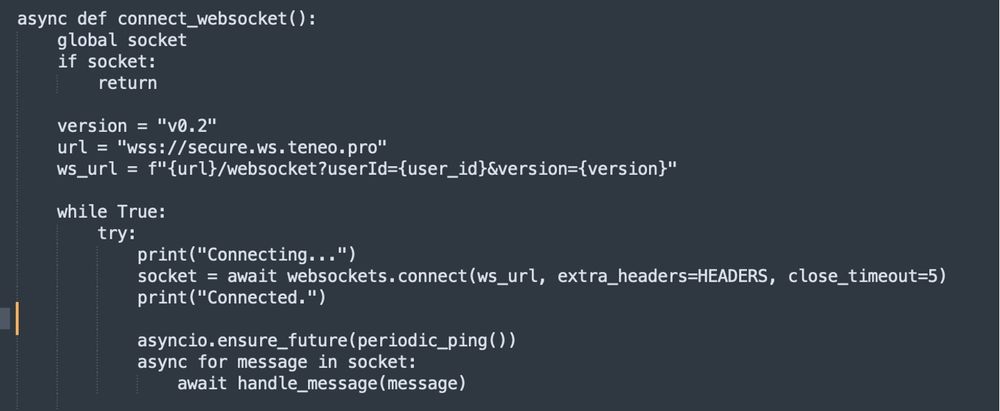
🔗 www.darktrace.com/blog/obfusca...
tl;dr - it was an individual that was able to download +9k documents over two months, it doesn't appear they were leaked anywhere publicly.
www.theguardian.com/australia-ne...

tl;dr - it was an individual that was able to download +9k documents over two months, it doesn't appear they were leaked anywhere publicly.
www.theguardian.com/australia-ne...
🔎 Of particular note, this attack is aided with a .LNK file pulling in a .HTA via a remote location.
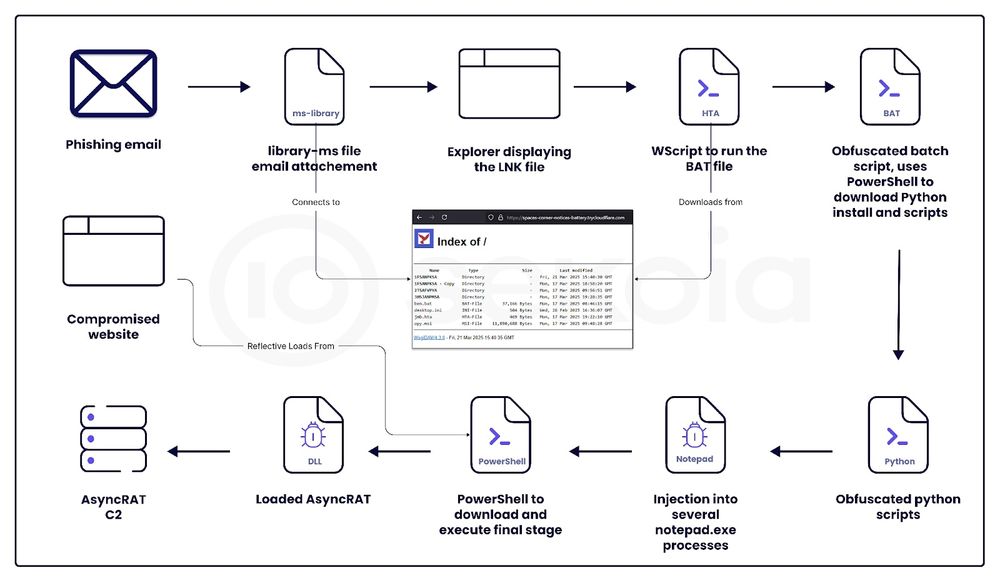
🔎 Of particular note, this attack is aided with a .LNK file pulling in a .HTA via a remote location.
- CVE-2025-32433
- Exploitable without authentication needed
- Exists in Erlang's built-in SSH server
- Commonly found in loT and Teleco gear
- Exploit model now in Metasploit and on GitHub
- CVE-2025-32433
- Exploitable without authentication needed
- Exists in Erlang's built-in SSH server
- Commonly found in loT and Teleco gear
- Exploit model now in Metasploit and on GitHub
🔗 cloud.google.com/blog/topics/...
🔗 cloud.google.com/blog/topics/...
Make sure you're #ThreatHunting for new Vulnerable Drivers!
#IncidentResponse #ransomware #ThreatDetection
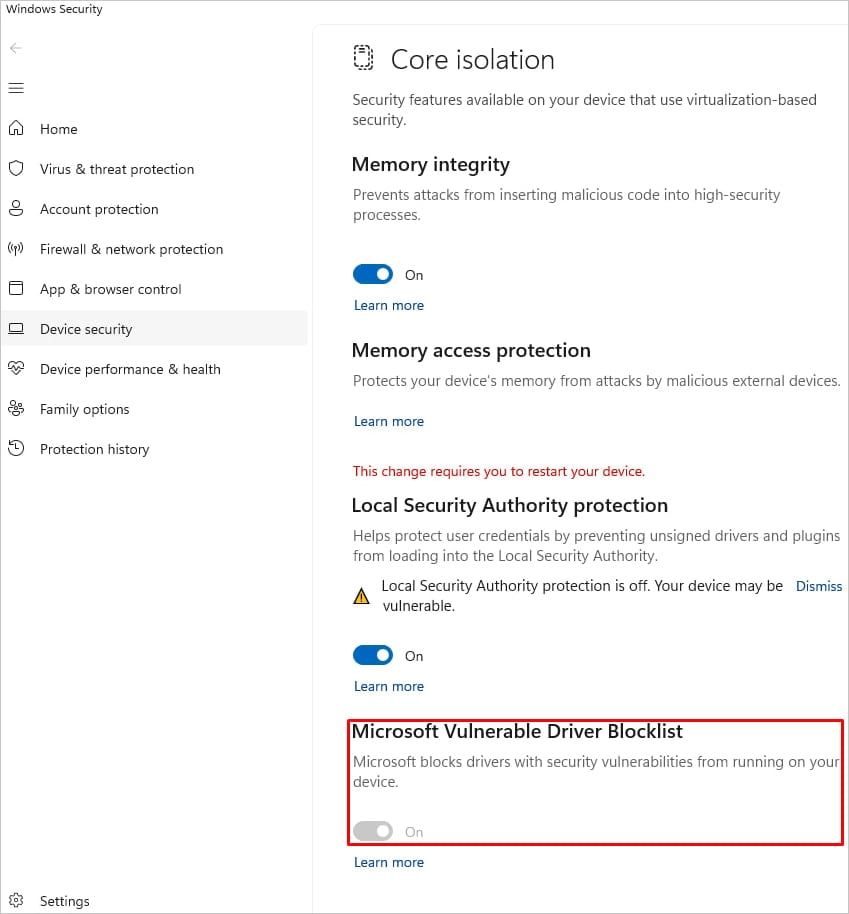
Make sure you're #ThreatHunting for new Vulnerable Drivers!
#IncidentResponse #ransomware #ThreatDetection
📋 Registration
Thurs, 13 Feb 2025
5:30pm – 6pm
🎤 Presentation
6pm – 7pm
Register Here: https://www.sans.org/mlp/community-night-perth-february-2025/
📍The Pan Pacific Perth Hotel, 207 Adelaide Terrace, Perth WA 6000

📋 Registration
Thurs, 13 Feb 2025
5:30pm – 6pm
🎤 Presentation
6pm – 7pm
Register Here: https://www.sans.org/mlp/community-night-perth-february-2025/
📍The Pan Pacific Perth Hotel, 207 Adelaide Terrace, Perth WA 6000
Useful to ID a cred stealer or going #ThreatHunting.
github.com/MalBeacon/wh... #threatintel #infosec #malware #DFIR
Useful to ID a cred stealer or going #ThreatHunting.
github.com/MalBeacon/wh... #threatintel #infosec #malware #DFIR
https://buff.ly/3PBmOpe
#IncidentResponse

https://buff.ly/3PBmOpe
#IncidentResponse
🕵 Monitoring S3 & encryption activity via CloudTrail & GuardDuty.
www.halcyon.ai/blog/abusing...
#CloudForensics #FOR509

🕵 Monitoring S3 & encryption activity via CloudTrail & GuardDuty.
www.halcyon.ai/blog/abusing...
#CloudForensics #FOR509

