
👉 Deploy a SIEM and detect on it– Catch brute force attempts before successful access.
👉 Enable MFA on VPN – Stop compromised credentials from granting access.
👉 Deploy a SIEM and detect on it– Catch brute force attempts before successful access.
👉 Enable MFA on VPN – Stop compromised credentials from granting access.
👉 SIEM Would Have Stopped This Early – brute force detections are only in the SIEM, not the EDR.
👉 EDR Detected the threat actor on their Windows-based attack phase – The 18 -minute gap gave attackers time to act.
👉 SIEM Would Have Stopped This Early – brute force detections are only in the SIEM, not the EDR.
👉 EDR Detected the threat actor on their Windows-based attack phase – The 18 -minute gap gave attackers time to act.
➡️ reg save hklm\system system
➡️ C:\Users\<redacted>\AppData\Local\Temp\lazagne.exe all
🕐 01:11:10 UTC – Huntress neutralises the intrusion
➡️ reg save hklm\system system
➡️ C:\Users\<redacted>\AppData\Local\Temp\lazagne.exe all
🕐 01:11:10 UTC – Huntress neutralises the intrusion
🕛 00:45:43 UTC – VPN Compromise
➡️ A brute-force attack led to initial access. This was discovered through retrospective forensic analysis
➡️ Huntress' SIEM would have caught this had it of been deployed in the network

🕛 00:45:43 UTC – VPN Compromise
➡️ A brute-force attack led to initial access. This was discovered through retrospective forensic analysis
➡️ Huntress' SIEM would have caught this had it of been deployed in the network
We have observed these tactics in previous incidents and were able to catch and neutralize the threat to this IT org before it could wreak havoc.
We have observed these tactics in previous incidents and were able to catch and neutralize the threat to this IT org before it could wreak havoc.
If you see renamed remote access binaries or odd PsExec usage, you may be facing more than a nuisance script kiddie.
If you see renamed remote access binaries or odd PsExec usage, you may be facing more than a nuisance script kiddie.
🚀 Lateral Movement & Persistence: Deployed a renamed Mesh Agent via PsExec.
🔍 Attempted to disguise their remote access tool as a benign binary (wvspbind.exe).

🚀 Lateral Movement & Persistence: Deployed a renamed Mesh Agent via PsExec.
🔍 Attempted to disguise their remote access tool as a benign binary (wvspbind.exe).
🎯 Always place exposed RDP behind a VPN and enable MFA
🎯 Enforce strong passwords across all user accounts
🎯 Disable unused accounts that haven’t been touched for 30+ days
🎯 Always place exposed RDP behind a VPN and enable MFA
🎯 Enforce strong passwords across all user accounts
🎯 Disable unused accounts that haven’t been touched for 30+ days
Moving quickly, they pivoted to deleting shadow copies to prevent recovery after encryption.

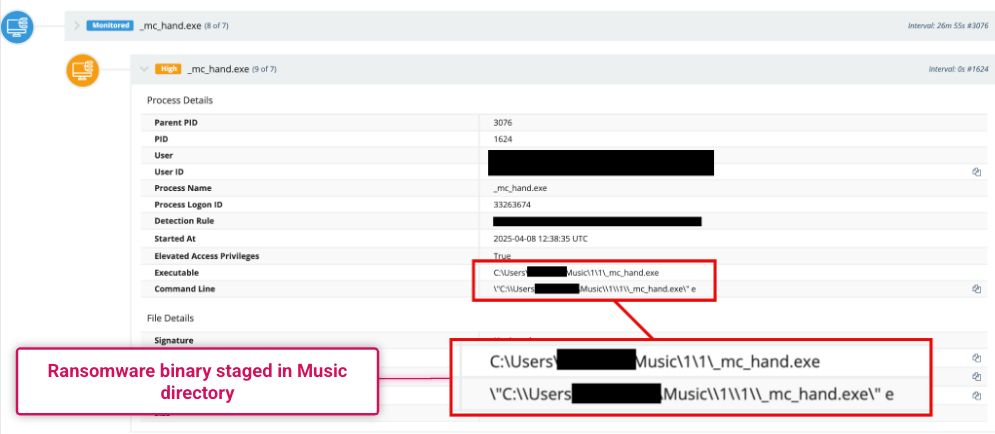
Moving quickly, they pivoted to deleting shadow copies to prevent recovery after encryption.
Wanna use Celestial Stealer to hack a business protected by Huntress? You're a daisy if you do.
Wanna use Celestial Stealer to hack a business protected by Huntress? You're a daisy if you do.
➡️ Enable MFA on all VPN logins (no exceptions).
➡️ Use IP restrictions to block unused locations.
➡️ Monitor and centralize VPN telemetry.
➡️ Commit to strong password policies.
➡️ Enable MFA on all VPN logins (no exceptions).
➡️ Use IP restrictions to block unused locations.
➡️ Monitor and centralize VPN telemetry.
➡️ Commit to strong password policies.
By combining Active Directory and VPN telemetry, we tracked the compromised account and launched network-wide isolation, shutting down lateral movement and blocking potential ransomware.
By combining Active Directory and VPN telemetry, we tracked the compromised account and launched network-wide isolation, shutting down lateral movement and blocking potential ransomware.
✅ Explored the network, hid findings in a shady folder, & dug through browser cookies for auth info.
✅ Files were staged on the network file server, ready for exfiltration or encryption.




✅ Explored the network, hid findings in a shady folder, & dug through browser cookies for auth info.
✅ Files were staged on the network file server, ready for exfiltration or encryption.
➕We observed several organizations targeted on April 21 in attacks that used several overlapping ping commands
We’ll continue giving updates on this exploit as we gather more details: www.huntress.com/blog/cve-202...

➕We observed several organizations targeted on April 21 in attacks that used several overlapping ping commands
We’ll continue giving updates on this exploit as we gather more details: www.huntress.com/blog/cve-202...
Don’t slack on security hygiene:
➡️ Enable MFA for all externally facing services
➡️ Require strong passwords and enforce time-of-day restrictions—all it takes is one compromised account to gain access
Don’t slack on security hygiene:
➡️ Enable MFA for all externally facing services
➡️ Require strong passwords and enforce time-of-day restrictions—all it takes is one compromised account to gain access

