
linktr.ee/hackwithintigriti
Yet, these seamless DOM-based bugs can sometimes even lead to account takeovers 👀
In our comprehensive article, we explore how you can identify and exploit this XSS type.

Yet, these seamless DOM-based bugs can sometimes even lead to account takeovers 👀
In our comprehensive article, we explore how you can identify and exploit this XSS type.
Yet, when present, they can allow for account takeovers, SQL injections and in-app privilege escalations 🤠
In our latest article, we break down every common JWT attack vector with practical exploitation techniques.

Yet, when present, they can allow for account takeovers, SQL injections and in-app privilege escalations 🤠
In our latest article, we break down every common JWT attack vector with practical exploitation techniques.
This month's issue is as usual packed with bug bounty tips:
✅ Cool trick to find disclosed secrets in internal web extensions
✅ A repository full of WAF bypasses
✅ Hacking Intercom misconfigurations
✅ Wayback Machine for hackers
+ monthly hacking challenge & much more!

This month's issue is as usual packed with bug bounty tips:
✅ Cool trick to find disclosed secrets in internal web extensions
✅ A repository full of WAF bypasses
✅ Hacking Intercom misconfigurations
✅ Wayback Machine for hackers
+ monthly hacking challenge & much more!
This developer has just completed this new MFA implementation, which provides an added layer of security to protect against credential stuffing attacks! 🤠
Can you craft a working payload to evade this MFA implementation? 😎
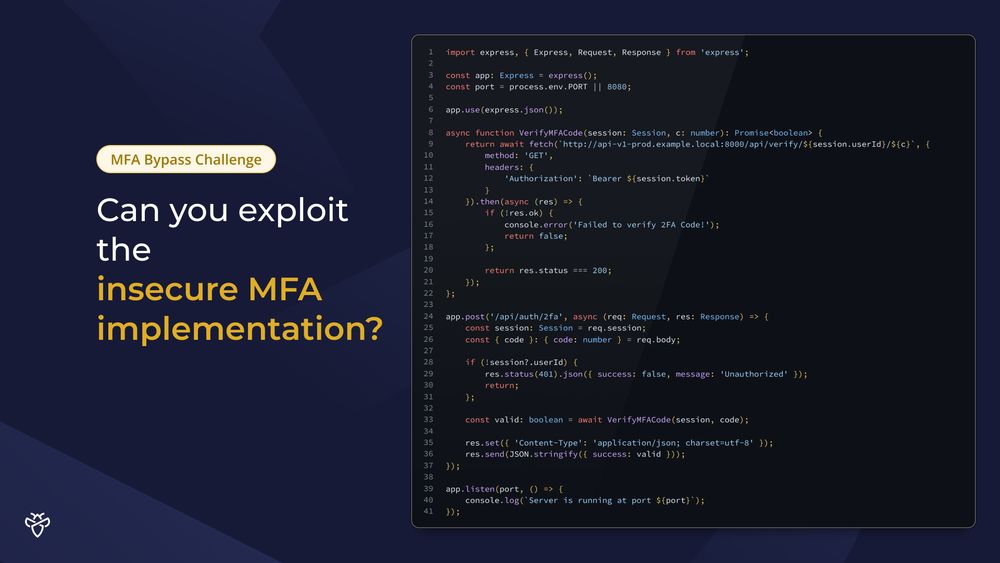
This developer has just completed this new MFA implementation, which provides an added layer of security to protect against credential stuffing attacks! 🤠
Can you craft a working payload to evade this MFA implementation? 😎
And they're all over the place... sometimes hiding in plain sight! 👀
In our most recent article, we shared a practical and beginner-friendly methodology for testing for reflected & stored XSS vulnerabilities in any target!

And they're all over the place... sometimes hiding in plain sight! 👀
In our most recent article, we shared a practical and beginner-friendly methodology for testing for reflected & stored XSS vulnerabilities in any target!
But you have to know where to look for them... 🔍
In our article, we explore several methods to search for leaked secrets, such as credential pairs, API keys, and other hard-coded tokens that can expand your initial attack surfaces

But you have to know where to look for them... 🔍
In our article, we explore several methods to search for leaked secrets, such as credential pairs, API keys, and other hard-coded tokens that can expand your initial attack surfaces
This developer has just finished writing his new input sanitizer function and is certain that it catches all malicious XSS payloads! 🤠
Can you craft a working payload proving him otherwise? 😎
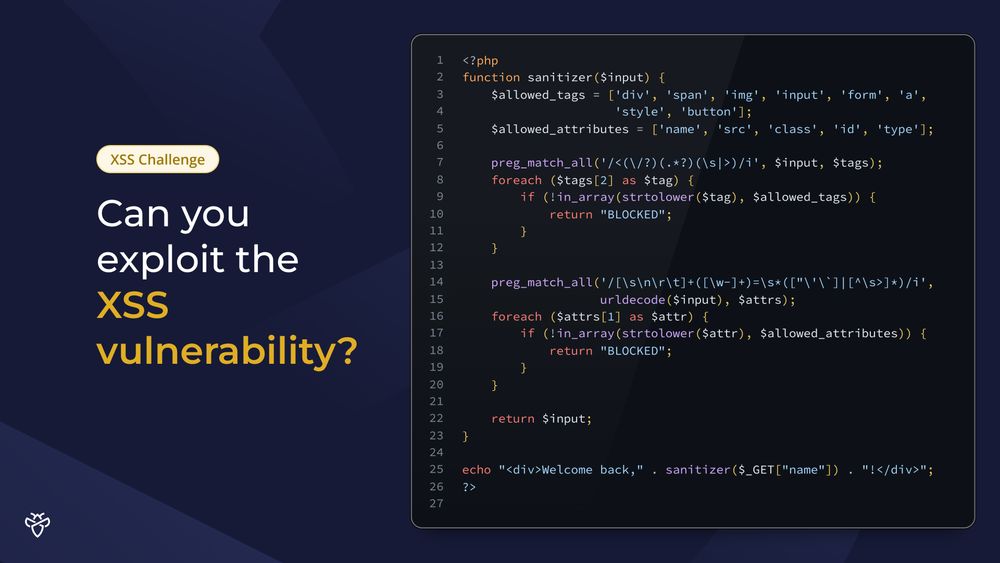
This developer has just finished writing his new input sanitizer function and is certain that it catches all malicious XSS payloads! 🤠
Can you craft a working payload proving him otherwise? 😎
But its extensive functionality introduces multiple attack surfaces for security vulnerabilities to arise... 😬
In our recent article, we documented 3 ways to exploit SSRF vulnerabilities in NextJS targets!
Link in next post 👇

But its extensive functionality introduces multiple attack surfaces for security vulnerabilities to arise... 😬
In our recent article, we documented 3 ways to exploit SSRF vulnerabilities in NextJS targets!
Link in next post 👇
Make sure you check your 'Updates' or 'Promotions' tab in Gmail and consider adding us to your contact lists so you never miss out on future Bug Bytes publications! 🐛

Make sure you check your 'Updates' or 'Promotions' tab in Gmail and consider adding us to your contact lists so you never miss out on future Bug Bytes publications! 🐛
This month's issue is as usual packed with bug bounty tips:
✅ A common (yet unknown) SSRF attack vector in Next.js Middleware
✅ Exploiting PDF processors by generating and uploading malicious PDF payload files
✅ A full recon breakdown on how to approach any target

This month's issue is as usual packed with bug bounty tips:
✅ A common (yet unknown) SSRF attack vector in Next.js Middleware
✅ Exploiting PDF processors by generating and uploading malicious PDF payload files
✅ A full recon breakdown on how to approach any target
But they also open up a new attack surface for us to explore... 👀
In our latest article, we've lined up frequent security risks to test for when you approach your next target

But they also open up a new attack surface for us to explore... 👀
In our latest article, we've lined up frequent security risks to test for when you approach your next target
www.intigriti.com/researchers/...

www.intigriti.com/researchers/...
The latest release has introduced profile customization, including uploading your profile picture! 🤠
Can you craft a payload that enables remote code execution? The web server (Apache) is configured to execute any PHP files in the upload directory! 😎
The latest release has introduced profile customization, including uploading your profile picture! 🤠
Can you craft a payload that enables remote code execution? The web server (Apache) is configured to execute any PHP files in the upload directory! 😎
Our latest community challenge featured a unique SSRF pattern in NextJS Middleware that many developers (& security researchers) don't know about 👀

Our latest community challenge featured a unique SSRF pattern in NextJS Middleware that many developers (& security researchers) don't know about 👀
Make sure you check your 'Updates' or 'Promotions' tab in Gmail and consider adding us to your contact lists so you never miss out on future Bug Bytes publications! 🐛

Make sure you check your 'Updates' or 'Promotions' tab in Gmail and consider adding us to your contact lists so you never miss out on future Bug Bytes publications! 🐛
This month's issue is as usual packed with bug bounty tips:
✅ Evading WAFs like Cloudflare,Akamai & AWS Cloudfront
✅ Creating your complete bug bounty automation system
✅ A powerful, targeted backup file scanner
✅ Bypassing CSP to achieve XSS via a cool trick with PDFs

This month's issue is as usual packed with bug bounty tips:
✅ Evading WAFs like Cloudflare,Akamai & AWS Cloudfront
✅ Creating your complete bug bounty automation system
✅ A powerful, targeted backup file scanner
✅ Bypassing CSP to achieve XSS via a cool trick with PDFs
Firebase uses custom security rules that are more complex to get right.
In our latest article, we covered several ways to find security misconfigurations in Firebase targets 😎

Firebase uses custom security rules that are more complex to get right.
In our latest article, we covered several ways to find security misconfigurations in Firebase targets 😎
This new text-to-image tool has been added to the collection of conversion tools. It also accepts URLs! 🤠
Can you craft a working proof of concept that is capable of reaching the internal-only AWS metadata endpoint? 😎

This new text-to-image tool has been added to the collection of conversion tools. It also accepts URLs! 🤠
Can you craft a working proof of concept that is capable of reaching the internal-only AWS metadata endpoint? 😎
But WAF is in the way... 😓
What if you could just bypass this WAF and get your payload through? 🤠
In our latest article, we documented several ways to identify the origin IP of your target behind popular CDNs and firewalls!
🔗 www.intigriti.com/researchers/...

But WAF is in the way... 😓
What if you could just bypass this WAF and get your payload through? 🤠
In our latest article, we documented several ways to identify the origin IP of your target behind popular CDNs and firewalls!
🔗 www.intigriti.com/researchers/...
Make sure you check your 'Updates' or 'Promotions' tab in Gmail and consider adding us to your contact lists so you never miss out on future Bug Bytes publications! 🐛

Make sure you check your 'Updates' or 'Promotions' tab in Gmail and consider adding us to your contact lists so you never miss out on future Bug Bytes publications! 🐛
This month's issue is as usual packed with bug bounty tips:
✅ Exploiting Log4Shell (Log4J) in 2025
✅ Indispensable GH recon tool (not the one you have in mind)
✅ Advanced WAF evasion techniques
✅ One of the most comprehensive guides on finding exposed S3 buckets

This month's issue is as usual packed with bug bounty tips:
✅ Exploiting Log4Shell (Log4J) in 2025
✅ Indispensable GH recon tool (not the one you have in mind)
✅ Advanced WAF evasion techniques
✅ One of the most comprehensive guides on finding exposed S3 buckets
It's the place where developers accidentally commit API keys, database credentials, and internal URLs (almost every single day) 🤠
In our most recent article, we documented how you can use GitHub dorking to find more vulnerabilities!
Read the article now👇

It's the place where developers accidentally commit API keys, database credentials, and internal URLs (almost every single day) 🤠
In our most recent article, we documented how you can use GitHub dorking to find more vulnerabilities!
Read the article now👇
While most moved on, some researchers know this vulnerability is still present today 👀
We just published a comprehensive guide showing exactly how to uncover Log4Shell vulnerabilities! 👇
www.intigriti.com/researchers/...

While most moved on, some researchers know this vulnerability is still present today 👀
We just published a comprehensive guide showing exactly how to uncover Log4Shell vulnerabilities! 👇
www.intigriti.com/researchers/...
Junior dev just finished with a new sandbox security policy to verify that only safe templates are rendered on his Twig 2.0 playground! 🤠
Can you craft a working proof of concept that executes the 'whoami' command? 😎
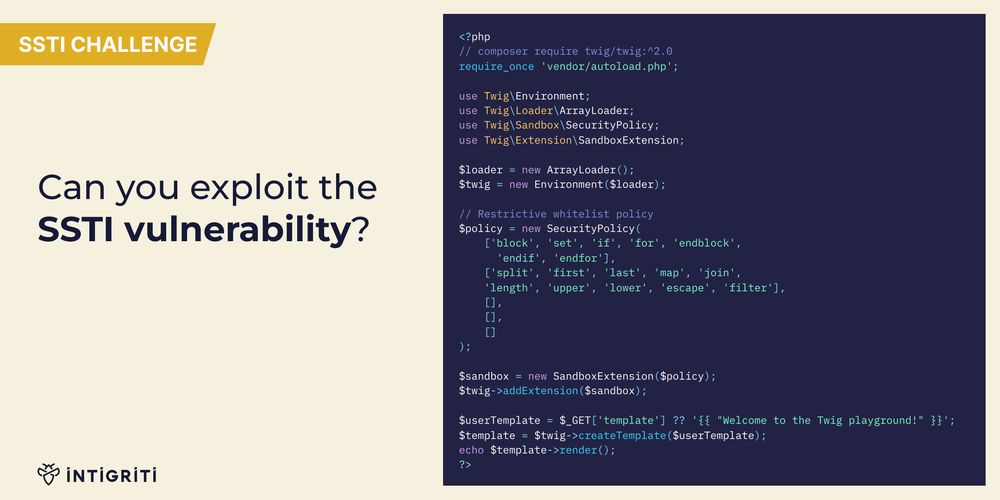
Junior dev just finished with a new sandbox security policy to verify that only safe templates are rendered on his Twig 2.0 playground! 🤠
Can you craft a working proof of concept that executes the 'whoami' command? 😎
But only if you know where to look for them! 🧐
In our latest article, we've outlined several SSTI exploitation techniques, including limited cases where sandboxes prevent functions! 😎
intigriti.com/researchers/...

But only if you know where to look for them! 🧐
In our latest article, we've outlined several SSTI exploitation techniques, including limited cases where sandboxes prevent functions! 😎
intigriti.com/researchers/...

