Brad
@malware-traffic-analysis.net
840 followers
95 following
140 posts
Sharing information on malicious network traffic and malware samples at https://www.malware-traffic-analysis.net/
Posts
Media
Videos
Starter Packs
Brad
@malware-traffic-analysis.net
· Jul 22
Brad
@malware-traffic-analysis.net
· Jul 21
Brad
@malware-traffic-analysis.net
· Jul 21























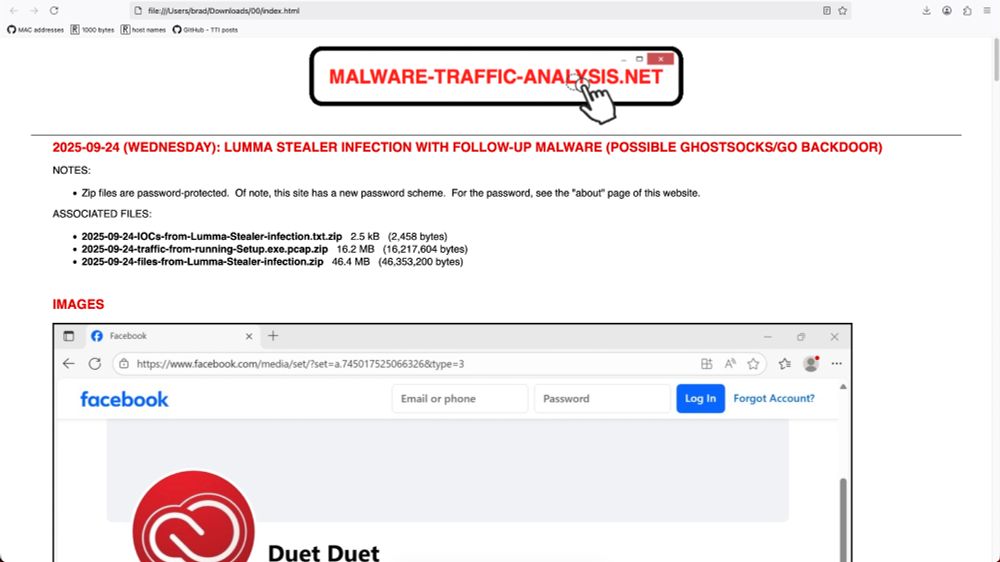















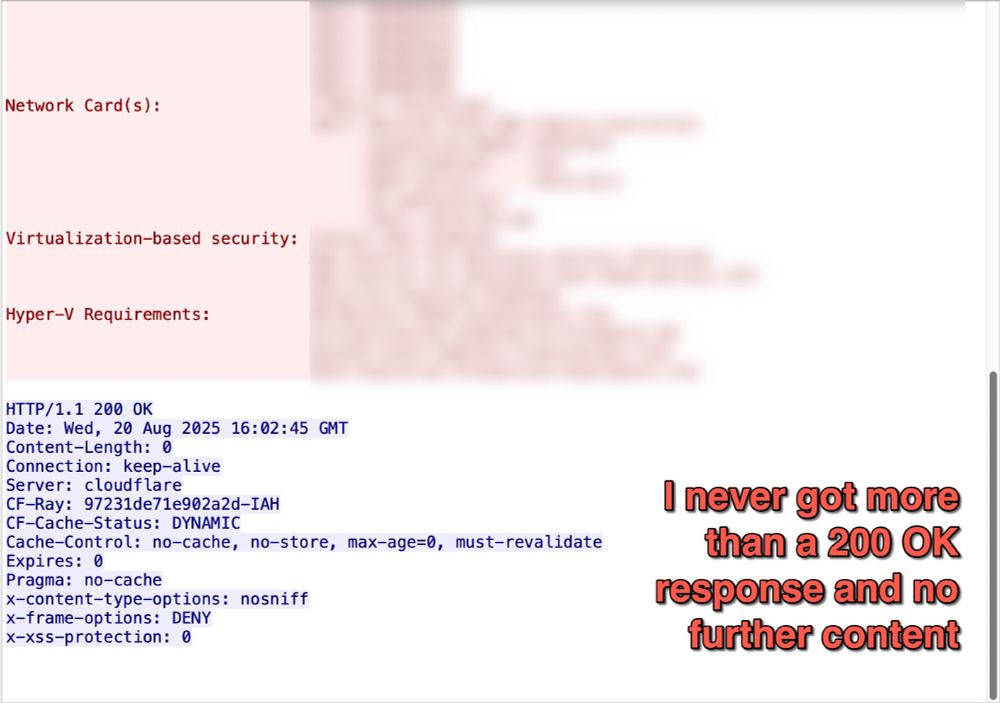


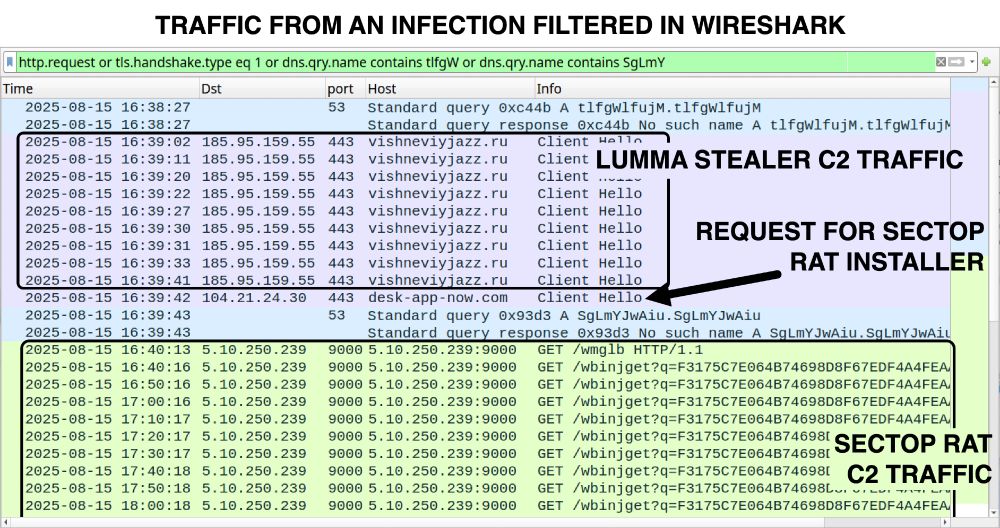


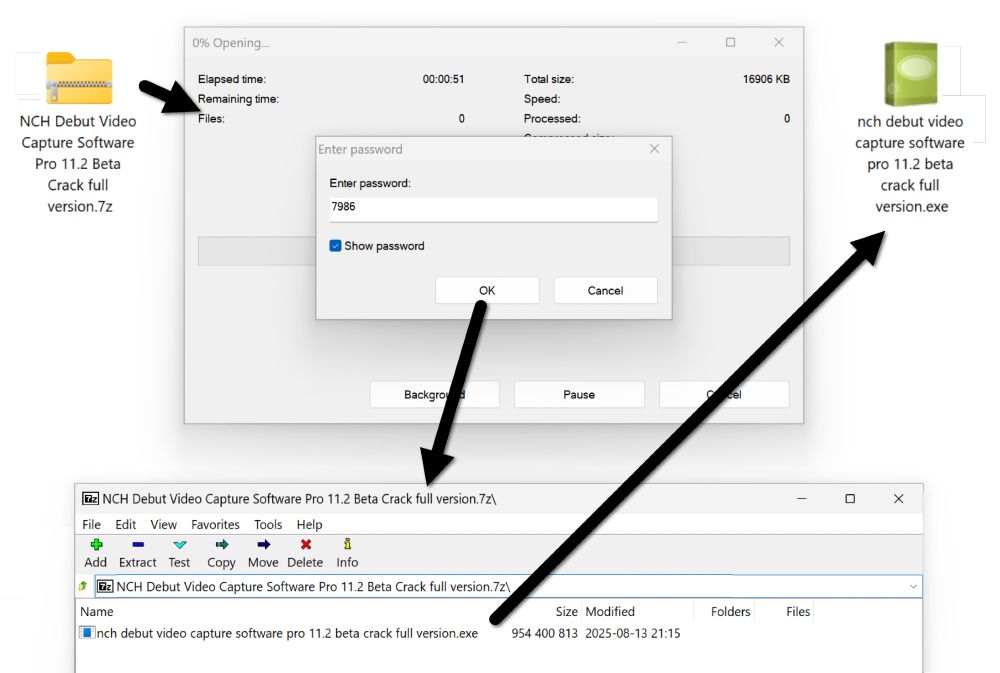
![Traffic from the Lumma Stealer infection after running "NCH Debut Video Capture Software Pro 11.2 Beta Crack full version.exe" on a vulnerable Windows host. Note the unusual DNS query for iUlWkftUnbTjqPSDLGsNPpSG.iUlWkftUnbTjqPSDLGsNPpSG that happened before the HTTPS Lumma Stealer C2 traffic to secrequ[.]top.](https://cdn.bsky.app/img/feed_thumbnail/plain/did:plc:v3kgm6hujff4gbxies5vwbnb/bafkreiatyraputlzakadve2gzcydsdu7fffker5qmif57dzjrr5boxqlya@jpeg)