They proudly secured third place overall 👏
Next stop: Tokyo for the upcoming edition 🇯🇵 👀
More details on the targets and participants here ℹ️
www.zerodayinitiative.com/blog/2025/20...

They proudly secured third place overall 👏
Next stop: Tokyo for the upcoming edition 🇯🇵 👀
More details on the targets and participants here ℹ️
www.zerodayinitiative.com/blog/2025/20...
www.synacktiv.com/en/publicati...

www.synacktiv.com/en/publicati...






Let’s keep pushing 💪
#P2OIreland #Synacktiv

Let’s keep pushing 💪
#P2OIreland #Synacktiv
@mtalbi.bsky.social and Matthieu just pulled off an exploit on the Philips Hue Bridge without laying a finger on the device!
Great demonstration of Synacktiv’s offensive expertise 👏
Come on 🔥

@mtalbi.bsky.social and Matthieu just pulled off an exploit on the Philips Hue Bridge without laying a finger on the device!
Great demonstration of Synacktiv’s offensive expertise 👏
Come on 🔥

Exploiting the Undefined: PWNing Firefox by Settling its Promises by Tao Yan & Edouard Bochin

Exploiting the Undefined: PWNing Firefox by Settling its Promises by Tao Yan & Edouard Bochin

➡️ Details & benefits: www.hexacon.fr/conference/c...
Also, conference tickets will be on sale today at 4PM (UTC+2)
➡️ Details & benefits: www.hexacon.fr/conference/c...
Also, conference tickets will be on sale today at 4PM (UTC+2)
www.synacktiv.com/en/publicati...

www.synacktiv.com/en/publicati...
We are releasing the Phrack 71 PDF for you today!
Don't forget this year is Phrack's 40th anniversary release! Send in your contribution and be part of this historical issue!
The CFP is still open, you can find it and the PDF link at phrack.org
We are releasing the Phrack 71 PDF for you today!
Don't forget this year is Phrack's 40th anniversary release! Send in your contribution and be part of this historical issue!
The CFP is still open, you can find it and the PDF link at phrack.org
fahrplan.events.ccc.de/congress/202...
From Convenience to Contagion: The Libarchive Vulnerabilities Lurking in Windows 11
fahrplan.events.ccc.de/congress/202...

fahrplan.events.ccc.de/congress/202...
From Convenience to Contagion: The Libarchive Vulnerabilities Lurking in Windows 11
fahrplan.events.ccc.de/congress/202...
phrack.org
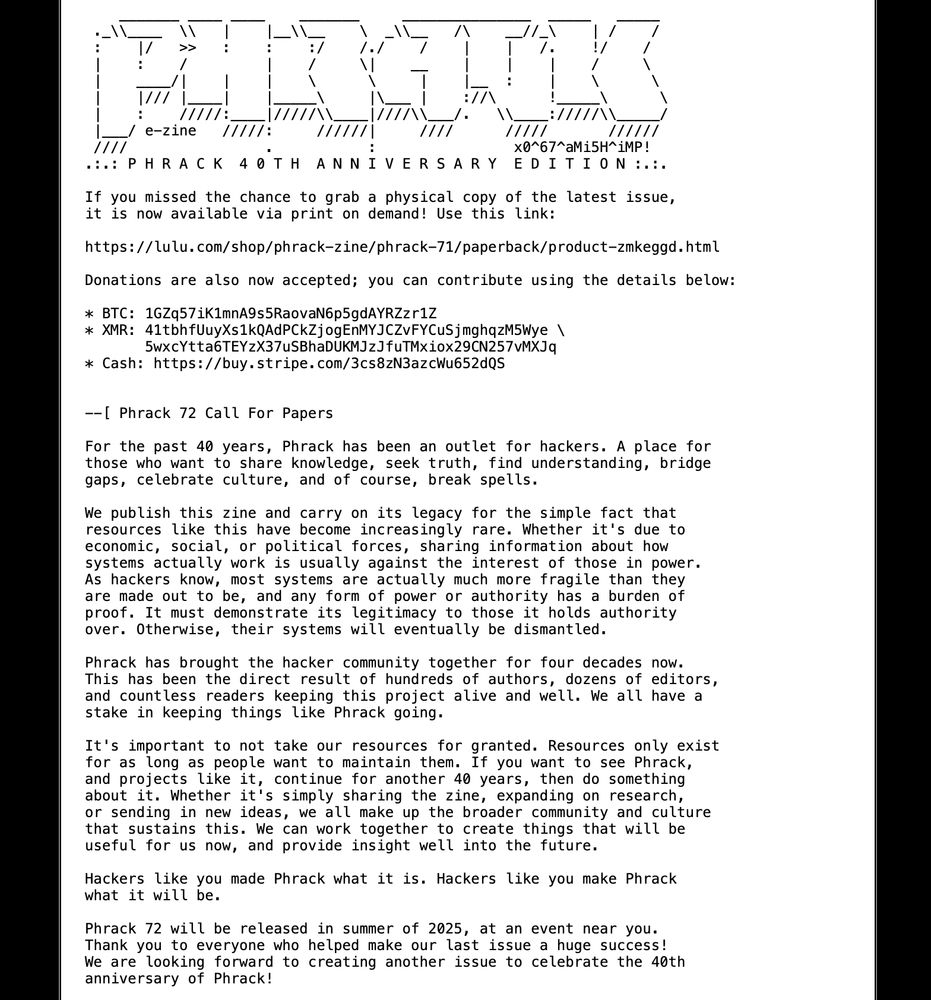
phrack.org


