
#PCAP or it didn't happen!
🌉 bridged from ⁂ https://infosec.exchange/@netresec, follow @ap.brid.gy to interact
https://www.europol.europa.eu/media-press/newsroom/news/end-of-game-for-cybercrime-infrastructure-1025-servers-taken-down

https://www.europol.europa.eu/media-press/newsroom/news/end-of-game-for-cybercrime-infrastructure-1025-servers-taken-down
📆 Include "last seen" date when publishing IOCs
❌ Prune old IOCs
📜 Prioritize long lived IOCs over short lived ones
https://netresec.com/?b=25Be9dd
#threatintel

📆 Include "last seen" date when publishing IOCs
❌ Prune old IOCs
📜 Prioritize long lived IOCs over short lived ones
https://netresec.com/?b=25Be9dd
#threatintel
📅 February 23-26, 2026
⏲️ 13:00 to 17:00 CET (7am to 11am EDT)
🌍 Live online
https://netresec.com/?b=25A2e4f
#dfir #training

📅 February 23-26, 2026
⏲️ 13:00 to 17:00 CET (7am to 11am EDT)
🌍 Live online
https://netresec.com/?b=25A2e4f
#dfir #training

🔥 172.245.52[.]169:80
🔥 c.mid[.]al:80
https://tria.ge/251009-j26bgacj7s
https://app.any.run/tasks/952bf595-caf6-4445-b302-513295214e76
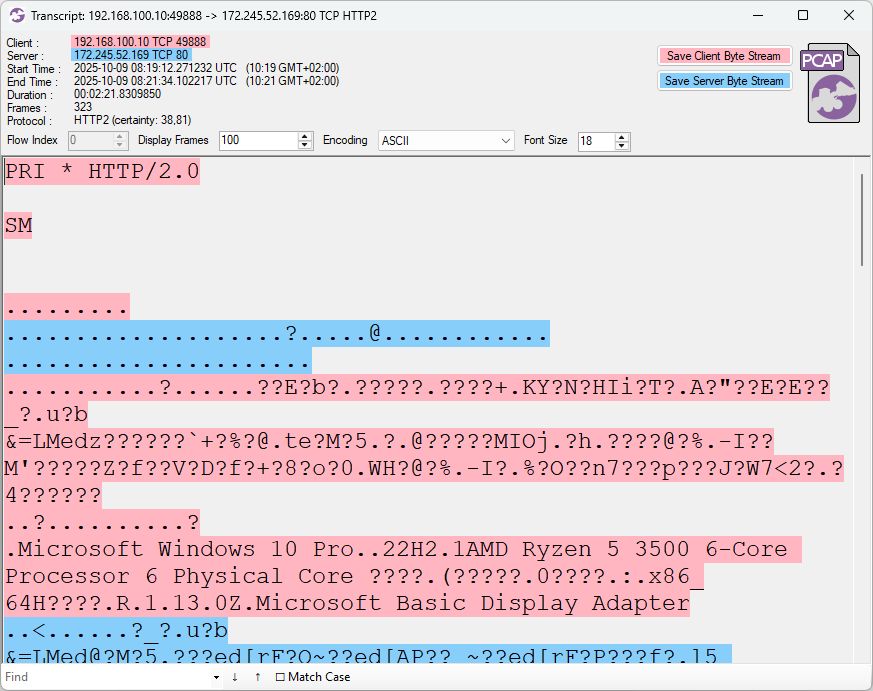
🔥 172.245.52[.]169:80
🔥 c.mid[.]al:80
https://tria.ge/251009-j26bgacj7s
https://app.any.run/tasks/952bf595-caf6-4445-b302-513295214e76
https://netresec.com/?b=259a5af

https://netresec.com/?b=259a5af
eca96bd74fb6b22848751e254b6dc9b8e2721f96
Here’s an @anyrun_app execution, of AdobePlugins.exe on May 19, which runs CANONSTAGER as well as SOGU.SEC […]
[Original post on infosec.exchange]

eca96bd74fb6b22848751e254b6dc9b8e2721f96
Here’s an @anyrun_app execution, of AdobePlugins.exe on May 19, which runs CANONSTAGER as well as SOGU.SEC […]
[Original post on infosec.exchange]
eca96bd74fb6b22848751e254b6dc9b8e2721f96
Here’s a sandbox execution, of AdobePlugins.exe on May 19, which runs CANONSTAGER as well as SOGU.SEC […]
[Original post on infosec.exchange]

eca96bd74fb6b22848751e254b6dc9b8e2721f96
Here’s a sandbox execution, of AdobePlugins.exe on May 19, which runs CANONSTAGER as well as SOGU.SEC […]
[Original post on infosec.exchange]
🔥 e0b465d3bd1ec5e95aee016951d55640
🔥 5ab23ac79ede02166d6f5013d89738f9
📡 Huy1612-24727.portmap[.]io:24727
📡 193.161.193.99:24727
📡 147.185.221.30:54661
https://netresec.com/?b=258f641

🔥 e0b465d3bd1ec5e95aee016951d55640
🔥 5ab23ac79ede02166d6f5013d89738f9
📡 Huy1612-24727.portmap[.]io:24727
📡 193.161.193.99:24727
📡 147.185.221.30:54661
https://netresec.com/?b=258f641
IOCs:
👾 193.26.115.125:8883
👾 purebase.ddns[.]net:8883
👾 45.74.10.38:56001
👾 139.99.83.25:56001
https://netresec.com/?b=2589522

IOCs:
👾 193.26.115.125:8883
👾 purebase.ddns[.]net:8883
👾 45.74.10.38:56001
👾 139.99.83.25:56001
https://netresec.com/?b=2589522
> We bring together a community of practitioners, researchers, public sector leaders, and industry experts who understand that security is not an afterthought—it’s a prerequisite. . And without trust and security the AI adoption […]
> We bring together a community of practitioners, researchers, public sector leaders, and industry experts who understand that security is not an afterthought—it’s a prerequisite. . And without trust and security the AI adoption […]
🔥 MD5: b2647b263c14226c62fe743dbff5c70a
🔥 C2: 147.124.219.201:65535
https://netresec.com/?b=257eead
🔥 MD5: b2647b263c14226c62fe743dbff5c70a
🔥 C2: 147.124.219.201:65535
https://netresec.com/?b=257eead
C2 servers:
🔥 45.141.233.100:7708
🔥 144.172.91.74:7709
🔥 62.60.235.100:9100
🔥 65.108.24.103:62050
🔥 91.92.120.102:62050
🔥 192.30.240.242:62520
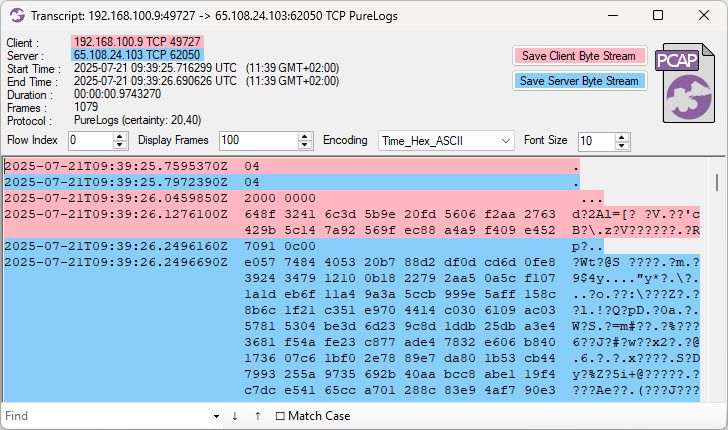
C2 servers:
🔥 45.141.233.100:7708
🔥 144.172.91.74:7709
🔥 62.60.235.100:9100
🔥 65.108.24.103:62050
🔥 91.92.120.102:62050
🔥 192.30.240.242:62520
https://netresec.com/?b=257eead

https://netresec.com/?b=257eead
💧 Dropper connects to legitimate website
📄 A fake PDF is downloaded over HTTPS
💾 The fake PDF is decrypted to a #purelogs DLL
⚙️ InstallUtil.exe or RegAsm.exe is started.
💉 PureLogs DLL is injected into the running process
👾 PureLogs connects to C2 server
IOC List
🔥 91.92.120 […]
💧 Dropper connects to legitimate website
📄 A fake PDF is downloaded over HTTPS
💾 The fake PDF is decrypted to a #purelogs DLL
⚙️ InstallUtil.exe or RegAsm.exe is started.
💉 PureLogs DLL is injected into the running process
👾 PureLogs connects to C2 server
IOC List
🔥 91.92.120 […]
⚠️ IP lookup alert
🔎 Better protocol identification
🐛 Bug fixes
https://netresec.com/?b=2571527

⚠️ IP lookup alert
🔎 Better protocol identification
🐛 Bug fixes
https://netresec.com/?b=2571527
https://www.bleepingcomputer.com/news/security/hackers-turn-screenconnect-into-malware-using-authenticode-stuffing/

https://www.bleepingcomputer.com/news/security/hackers-turn-screenconnect-into-malware-using-authenticode-stuffing/
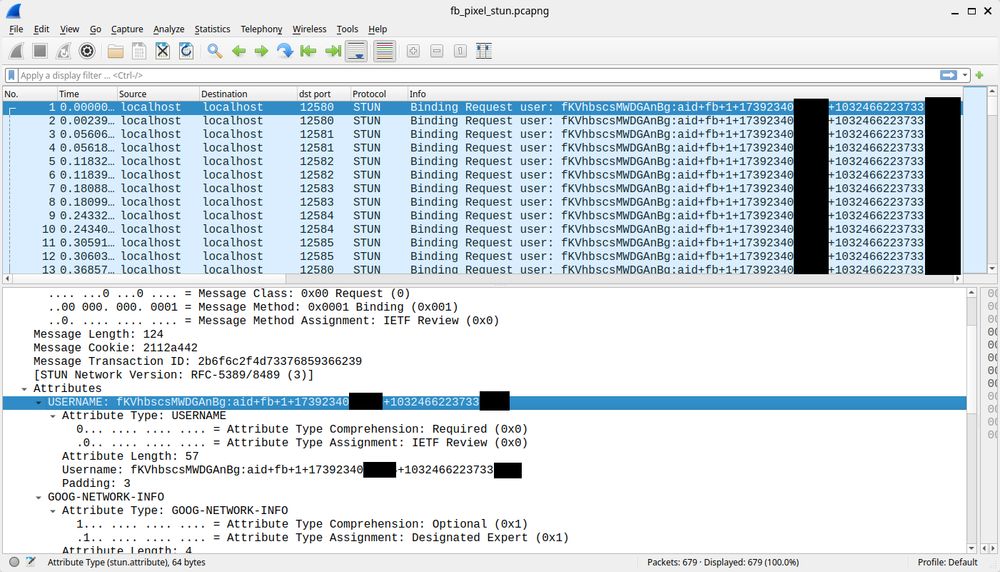
> The […]
[Original post on infosec.exchange]
> The […]
[Original post on infosec.exchange]
https://www.heise.de/en/news/BKA-names-identity-of-the-suspected-boss-of-the-Trickbot-gang-10421313.html?utm_source=flipboard&utm_medium=activitypub
Posted into heise online in English @heise-online-in-english-heiseonline

https://www.heise.de/en/news/BKA-names-identity-of-the-suspected-boss-of-the-Trickbot-gang-10421313.html?utm_source=flipboard&utm_medium=activitypub
Posted into heise online in English @heise-online-in-english-heiseonline
🔎 Identifies over 250 protocols in #pcap
🎨 Define protocols from example traffic
🇶 Extracts JA3, JA4 and SNI from QUIC
💻 10x faster user interface
https://netresec.com/?b=256dbbc

🔎 Identifies over 250 protocols in #pcap
🎨 Define protocols from example traffic
🇶 Extracts JA3, JA4 and SNI from QUIC
💻 10x faster user interface
https://netresec.com/?b=256dbbc
#threathunting #threatintel
![Many organizations may not need to allow outgoing traffic to hosting and API mocking
services, which are frequently used by GRU unit 26165. Organizations should consider
alerting on or blocking the following services, with exceptions allowlisted for legitimate
activity [D3-DNSDL].
*.000[.]pe
*.1cooldns[.]com
*.42web[.]io
*.4cloud[.]click
*.accesscan[.]org
*.bumbleshrimp[.]com
*.camdvr[.]org
*.casacam[.]net
*.ddnsfree[.]com
*.ddnsgeek[.]com
*.ddnsguru[.]com
*.dynuddns[.]com
*.dynuddns[.]net
*.free[.]nf
*.freeddns[.]org
*.frge[.]io
*.glize[.]com
*.great-site[.]net
*.infinityfreeapp[.]com
*.kesug[.]com
*.loseyourip[.]com
*.lovestoblog[.]com
*.mockbin[.]io
*.mockbin[.]org
*.mocky[.]io
*.mybiolink[.]io
*.mysynology[.]net
*.mywire[.]org
*.ngrok[.]io
*.ooguy[.]com
*.pipedream[.]net
*.rf[.]gd
*.urlbae[.]com
*.webhook[.]site
*.webhookapp[.]com
*.webredirect[.]org
*.wuaze[.]com
Heuristic detections for web requests to new subdomains, including of the above
providers, may uncover malicious phishing activity [D3-DNRA]. Logging the requests for
each sub-domain requested by users on a network, such as in DNS or firewall logs,
may enable system administrators to identify new targeting and victims](https://cdn.bsky.app/img/feed_thumbnail/plain/did:plc:vbkuf6l52tkey3ntlxn4ju26/bafkreid64jpxnqwmyek7rxf3lgh3uihydqyh7hempn62ignqvcfyv3fqxy@jpeg)
#threathunting #threatintel
https://www.theregister.com/2025/05/10/router_botnet_crashed/
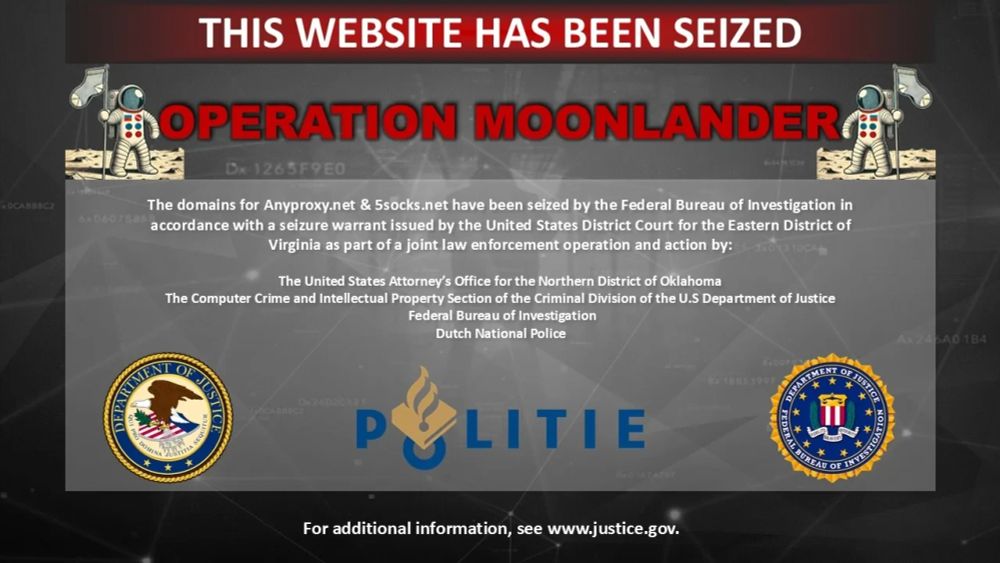
https://www.theregister.com/2025/05/10/router_botnet_crashed/
https://www.bleepingcomputer.com/news/security/germany-takes-down-exch-cryptocurrency-exchange-seizes-servers/

https://www.bleepingcomputer.com/news/security/germany-takes-down-exch-cryptocurrency-exchange-seizes-servers/

