
#PCAP or it didn't happen!
🌉 bridged from ⁂ https://infosec.exchange/@netresec, follow @ap.brid.gy to interact

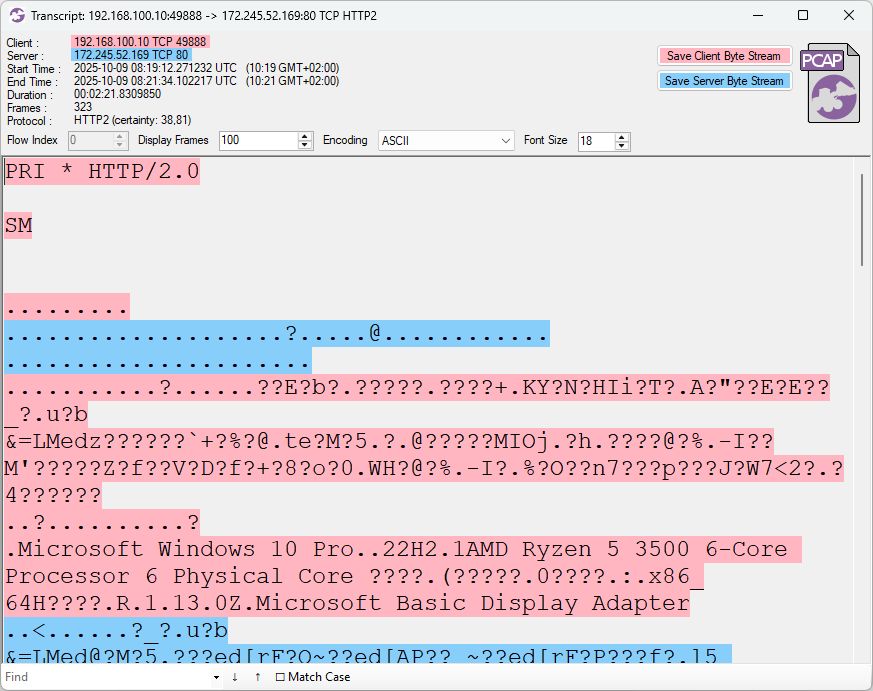
![HTTP/2 headers extracted from PCAP with NetworkMiner.
:method :method POST 1554 192.168.100.10 [DESKTOP-JGLLJLD]
:scheme :scheme http 1554 192.168.100.10 [DESKTOP-JGLLJLD]
:path :path /proto.NezhaService/ReportSystemInfo2 1554 192.168.100.10 [DESKTOP-JGLLJLD]
:authority :authority c.mid.al:80 1554 192.168.100.10 [DESKTOP-JGLLJLD]
content-type content-type application/grpc 1554 192.168.100.10 [DESKTOP-JGLLJLD]
user-agent user-agent grpc-go/1.72.2 1554 192.168.100.10 [DESKTOP-JGLLJLD]
te te trailers 1554 192.168.100.10 [DESKTOP-JGLLJLD]
grpc-timeout grpc-timeout 4033579u 1554 192.168.100.10 [DESKTOP-JGLLJLD]
client_uuid client_uuid f6e7314f-5c7e-f2cb-5be7-68b95a0cf7c3 1554 192.168.100.10 [DESKTOP-JGLLJLD]
client_secret client_secret GuH9TipzAZxzcnUpgYFfh0kwNSOyU8am 1554 192.168.100.10 [DESKTOP-JGLLJLD]
:status :status 200 1558 172.245.52.169 [c.mid.al]
content-type content-type application/grpc 1558 172.245.52.169 [c.mid.al]
trailer trailer Grpc-Status,Grpc-Message,Grpc-Status-Details-Bin 1558 172.245.52.169 [c.mid.al]
grpc-status grpc-status 0 1560 172.245.52.169 [c.mid.al]](https://cdn.bsky.app/img/feed_thumbnail/plain/did:plc:vbkuf6l52tkey3ntlxn4ju26/bafkreif6gcwjwx5jicdx2sgekdim47a3oi4datb6hvbsiavqudirlt4dba@jpeg)
🔥 172.245.52[.]169:80
🔥 c.mid[.]al:80
https://tria.ge/251009-j26bgacj7s
https://app.any.run/tasks/952bf595-caf6-4445-b302-513295214e76
🔥 172.245.52[.]169:80
🔥 c.mid[.]al:80
https://tria.ge/251009-j26bgacj7s
https://app.any.run/tasks/952bf595-caf6-4445-b302-513295214e76

eca96bd74fb6b22848751e254b6dc9b8e2721f96
Here’s an @anyrun_app execution, of AdobePlugins.exe on May 19, which runs CANONSTAGER as well as SOGU.SEC […]
[Original post on infosec.exchange]

eca96bd74fb6b22848751e254b6dc9b8e2721f96
Here’s an @anyrun_app execution, of AdobePlugins.exe on May 19, which runs CANONSTAGER as well as SOGU.SEC […]
[Original post on infosec.exchange]
eca96bd74fb6b22848751e254b6dc9b8e2721f96
Here’s a sandbox execution, of AdobePlugins.exe on May 19, which runs CANONSTAGER as well as SOGU.SEC […]
[Original post on infosec.exchange]

eca96bd74fb6b22848751e254b6dc9b8e2721f96
Here’s a sandbox execution, of AdobePlugins.exe on May 19, which runs CANONSTAGER as well as SOGU.SEC […]
[Original post on infosec.exchange]
🔥 MD5: b2647b263c14226c62fe743dbff5c70a
🔥 C2: 147.124.219.201:65535
https://netresec.com/?b=257eead
🔥 MD5: b2647b263c14226c62fe743dbff5c70a
🔥 C2: 147.124.219.201:65535
https://netresec.com/?b=257eead
C2 servers:
🔥 45.141.233.100:7708
🔥 144.172.91.74:7709
🔥 62.60.235.100:9100
🔥 65.108.24.103:62050
🔥 91.92.120.102:62050
🔥 192.30.240.242:62520
C2 servers:
🔥 45.141.233.100:7708
🔥 144.172.91.74:7709
🔥 62.60.235.100:9100
🔥 65.108.24.103:62050
🔥 91.92.120.102:62050
🔥 192.30.240.242:62520
![curl -s https://www.vastkupan.com/wp-admin/js/Cxqyoub.dat | xxd | head
00000000: 796b a434 3234 3431 3034 3134 cbce 3434 yk.424410414..44
00000010: 8934 3431 3434 3134 7431 3434 3134 3431 .4414414t1441441
00000020: 3434 3134 3431 3434 3134 3431 3434 3134 4414414414414414
00000030: 3431 3434 3134 3431 3434 3134 b431 3434 414414414414.144
00000040: 3f2b 8e3f 3480 38f9 1589 3578 fc15 6059 ?+.?4.8...5x..`Y
00000050: 5d47 1144 465e 5346 5059 1452 555a 5f5b ]G.DF^SFPY.RUZ_[
00000060: 4011 5651 1146 415f 145d 5f14 707e 6714 @.VQ.FA_.]_.p~g.
00000070: 5c5b 5054 1a39 3c3e 1031 3434 3134 3431 \[PT.9<>.1441441
00000080: 6471 3134 7830 3734 60a1 4059 3434 3134 dq14x074`.@Y4414
00000090: 3431 3434 d134 3a10 3f35 0134 3419 0134 4144.4:.?5.44..4](https://cdn.bsky.app/img/feed_thumbnail/plain/did:plc:vbkuf6l52tkey3ntlxn4ju26/bafkreiaf6zazee62egjxhkrwizeisvnumx26mmradb3r7ywugbm47cjvku@jpeg)
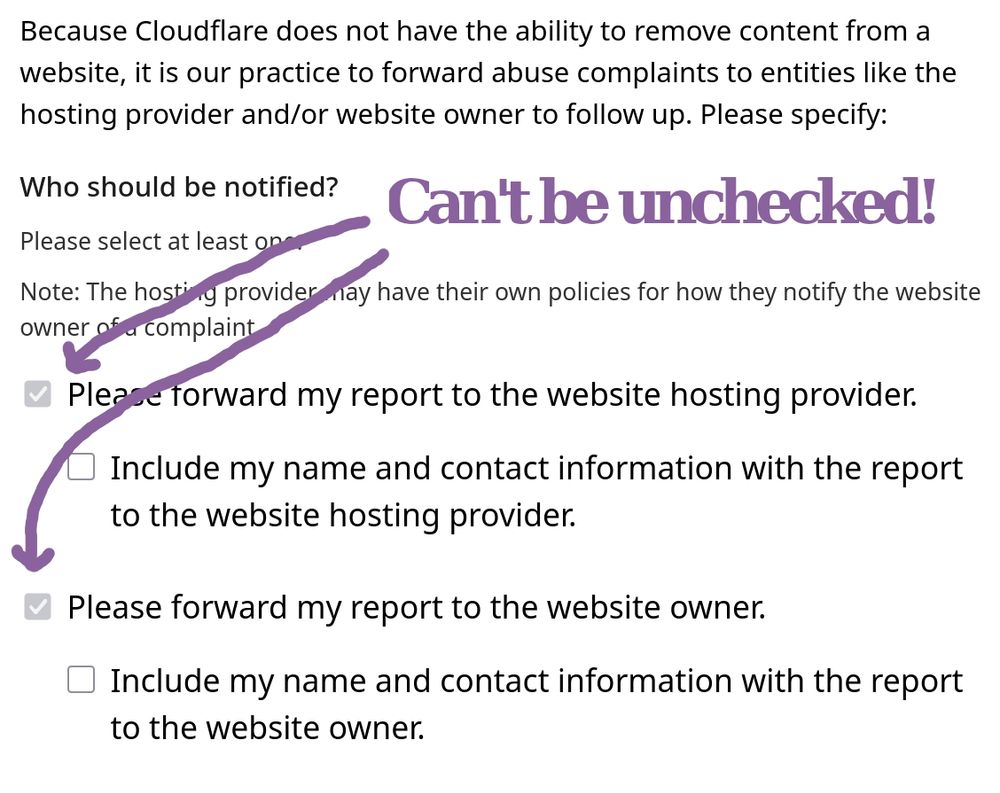
> The […]
[Original post on infosec.exchange]
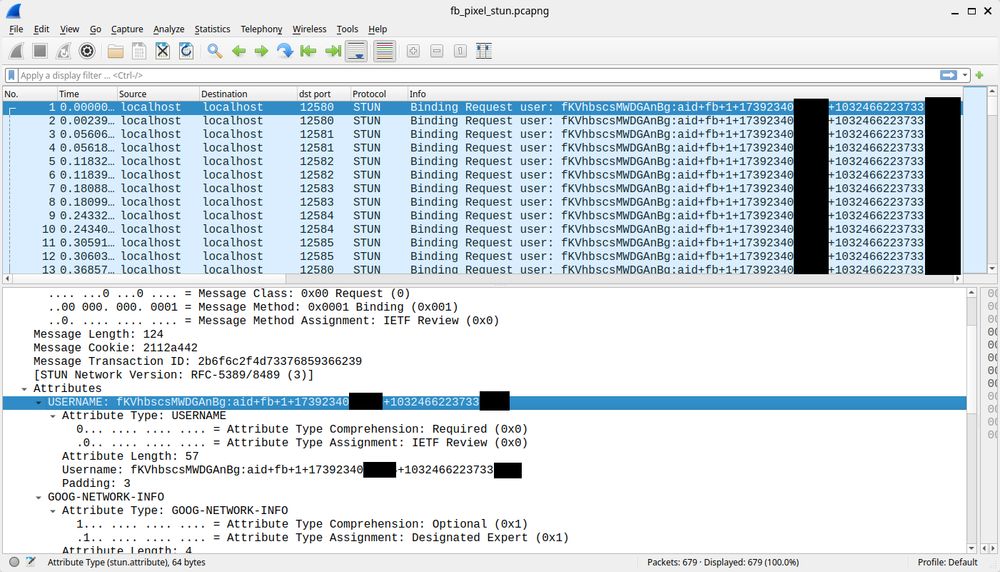
> The […]
[Original post on infosec.exchange]
#threathunting #threatintel
![Many organizations may not need to allow outgoing traffic to hosting and API mocking
services, which are frequently used by GRU unit 26165. Organizations should consider
alerting on or blocking the following services, with exceptions allowlisted for legitimate
activity [D3-DNSDL].
*.000[.]pe
*.1cooldns[.]com
*.42web[.]io
*.4cloud[.]click
*.accesscan[.]org
*.bumbleshrimp[.]com
*.camdvr[.]org
*.casacam[.]net
*.ddnsfree[.]com
*.ddnsgeek[.]com
*.ddnsguru[.]com
*.dynuddns[.]com
*.dynuddns[.]net
*.free[.]nf
*.freeddns[.]org
*.frge[.]io
*.glize[.]com
*.great-site[.]net
*.infinityfreeapp[.]com
*.kesug[.]com
*.loseyourip[.]com
*.lovestoblog[.]com
*.mockbin[.]io
*.mockbin[.]org
*.mocky[.]io
*.mybiolink[.]io
*.mysynology[.]net
*.mywire[.]org
*.ngrok[.]io
*.ooguy[.]com
*.pipedream[.]net
*.rf[.]gd
*.urlbae[.]com
*.webhook[.]site
*.webhookapp[.]com
*.webredirect[.]org
*.wuaze[.]com
Heuristic detections for web requests to new subdomains, including of the above
providers, may uncover malicious phishing activity [D3-DNRA]. Logging the requests for
each sub-domain requested by users on a network, such as in DNS or firewall logs,
may enable system administrators to identify new targeting and victims](https://cdn.bsky.app/img/feed_thumbnail/plain/did:plc:vbkuf6l52tkey3ntlxn4ju26/bafkreid64jpxnqwmyek7rxf3lgh3uihydqyh7hempn62ignqvcfyv3fqxy@jpeg)
#threathunting #threatintel
https://www.theregister.com/2025/05/10/router_botnet_crashed/
https://www.theregister.com/2025/05/10/router_botnet_crashed/

https://tria.ge/250411-f3d2tszyhy/behavioral1
👾 StealC v2: 62.60.226.114:80
👾 […]
[Original post on infosec.exchange]

https://tria.ge/250411-f3d2tszyhy/behavioral1
👾 StealC v2: 62.60.226.114:80
👾 […]
[Original post on infosec.exchange]
👾 45.227.252.199:7712
👾 46.4.119.125:7712
👾 62.60.226.101:40101
👾 62.60.226.101:40105
👾 62.60.226.114:40101
👾 146.190.108.105:7712
👾 155.138.150.12:7712
👾 198.251.84.107:7712
#aurotunstealer #threatintel

👾 45.227.252.199:7712
👾 46.4.119.125:7712
👾 62.60.226.101:40101
👾 62.60.226.101:40105
👾 62.60.226.114:40101
👾 146.190.108.105:7712
👾 155.138.150.12:7712
👾 198.251.84.107:7712
#aurotunstealer #threatintel

