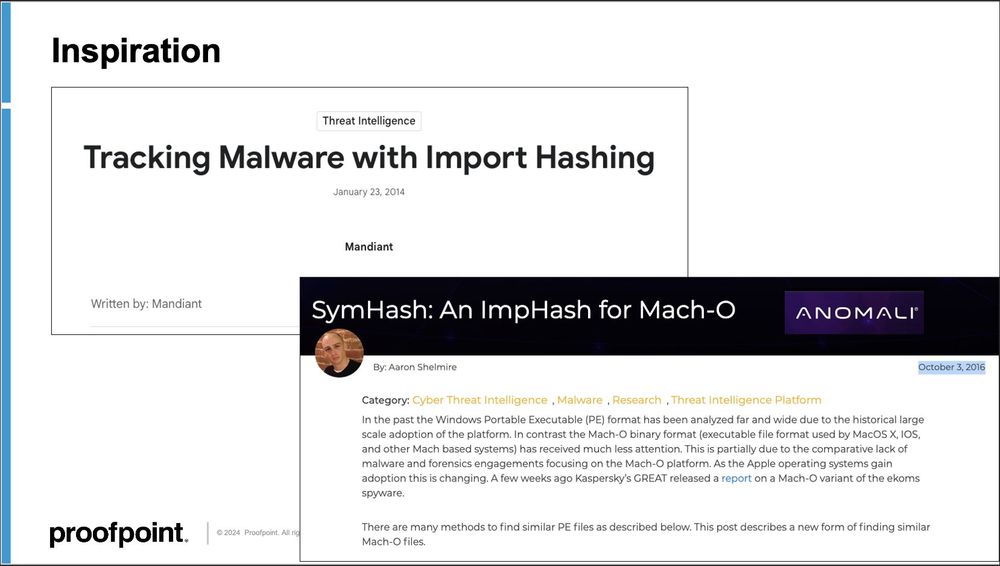
alden
@re.wtf
650 followers
410 following
13 posts
sr detection engineer @ huntress • malware enjoyer • macOS security
https://alden.io
Posts
Media
Videos
Starter Packs
Reposted by alden
Jamie Levy 🦉
@gleeda.bsky.social
· Apr 8
CrushFTP CVE-2025-31161 Auth Bypass and Post-Exploitation | Huntress
Huntress observed in-the-wild exploitation of CVE-2025-31161, an authentication bypass vulnerability in versions of CrushFTP and further post-exploitation leveraging MeshCentral and other malware.
www.huntress.com
Reposted by alden
Selena Larson
@selenalarson.bsky.social
· Mar 11

Remote Monitoring and Management (RMM) Tooling Increasingly an Attacker’s First Choice | Proofpoint US
Key findings More threat actors are using legitimate remote monitoring and management (RMM) tools as a first-stage payload in email campaigns. RMMs can be used for
www.proofpoint.com
Reposted by alden
Reposted by alden
Reposted by alden
Sean
@whatthefuzzvr.bsky.social
· Dec 27

Trying Out Binary Ninja's new WARP Signatures with IPSW Diff'ing
Binary diff'ing is pretty complex, but being able to apply markup from one binary to another is quite powerful. Binary Ninja's new WARP extends previous efforts, using SigKit, to quickly identify libr...
www.seandeaton.com
Reposted by alden
Reposted by alden
Reposted by alden
Reposted by alden
Reposted by alden