Still works on Pixels and Ubuntus (but the bug is fixed in stable kernels).
github.com/xairy/kernel...


kernelCTF entry for a race condition in the network scheduler subsystem.
Most notably, shows a technique of putting controlled data into unmapped sections of vmlinux.
github.com/n132/securit...

kernelCTF entry for a race condition in the network scheduler subsystem.
Most notably, shows a technique of putting controlled data into unmapped sections of vmlinux.
github.com/n132/securit...
Article by Seth Jenkins about a few problems with physical memory KASLR on arm64 devices.
googleprojectzero.blogspot.com/2025/11/defe...

Article by Seth Jenkins about a few problems with physical memory KASLR on arm64 devices.
googleprojectzero.blogspot.com/2025/11/defe...

Article by Robin Bastide about exploiting a NULL-pointer-dereference that led to a UAF access to the kernel stack in the NVIDIA GPU driver.
blog.quarkslab.com/nvidia_gpu_k...

Article by Robin Bastide about exploiting a NULL-pointer-dereference that led to a UAF access to the kernel stack in the NVIDIA GPU driver.
blog.quarkslab.com/nvidia_gpu_k...
Opt-in for now, but planned to replace the per-CPU partial slab layer for all caches in the future.
Gonna have to revise the slab shaping strategies once this happens.

Opt-in for now, but planned to replace the per-CPU partial slab layer for all caches in the future.
Gonna have to revise the slab shaping strategies once this happens.
All materials are public, so can go through the workshop on your own if you're interested.
github.com/xairy/raw-ga...
All materials are public, so can go through the workshop on your own if you're interested.
github.com/xairy/raw-ga...
github.com/google/syzka...
github.com/google/syzka...
Still works on Pixels and Ubuntus (but the bug is fixed in stable kernels).
github.com/xairy/kernel...


Still works on Pixels and Ubuntus (but the bug is fixed in stable kernels).
github.com/xairy/kernel...
If you wish to attend, you must bring Raspberry Pi 5 along with a few other things, see the workshop description.
github.com/xairy/raw-ga...

If you wish to attend, you must bring Raspberry Pi 5 along with a few other things, see the workshop description.
github.com/xairy/raw-ga...

Including getting kernel log over UART via USB-Cereal, building/flashing custom kernel, breaking into KGDB via /proc/sysrq-trigger or by sending SysRq-G over serial, dealing with watchdogs, etc.
xairy.io/articles/pix...
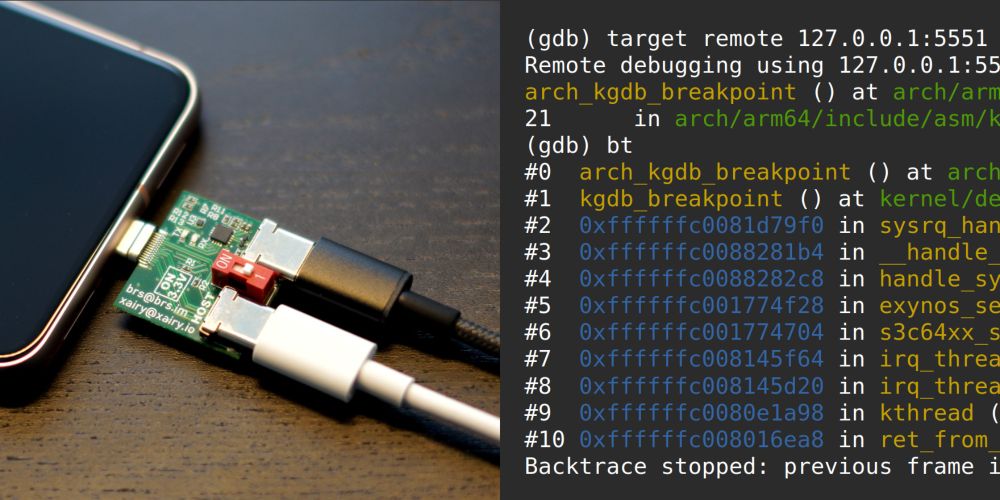
Including getting kernel log over UART via USB-Cereal, building/flashing custom kernel, breaking into KGDB via /proc/sysrq-trigger or by sending SysRq-G over serial, dealing with watchdogs, etc.
xairy.io/articles/pix...
Talk by Kees Cook about the relevance of various Linux kernel vulnerability classes and the mitigations that address them.
Video: www.youtube.com/watch?v=c_Nx...
Slides: static.sched.com/hosted_files...
Talk by Kees Cook about the relevance of various Linux kernel vulnerability classes and the mitigations that address them.
Video: www.youtube.com/watch?v=c_Nx...
Slides: static.sched.com/hosted_files...
Xuan Xing & Eugene Rodionov gave a talk about fuzzing the Linux kernel interfaces fully in user space using LKL (Linux Kernel Library).
Video: www.youtube.com/watch?v=Wxmi...
Slides: static.sched.com/hosted_files...

Xuan Xing & Eugene Rodionov gave a talk about fuzzing the Linux kernel interfaces fully in user space using LKL (Linux Kernel Library).
Video: www.youtube.com/watch?v=Wxmi...
Slides: static.sched.com/hosted_files...
youtu.be/YfjHCt4SzQc
Linux Kernel Exploitation For
Beginners
rvasec.com/slides/2025/...

youtu.be/YfjHCt4SzQc
Linux Kernel Exploitation For
Beginners
rvasec.com/slides/2025/...
Talk by Chariton Karamitas about ways to use FUSE for kernel exploitation from unprivileged SELinux contexts on Android.
www.youtube.com/watch?v=DJBG...
Talk by Chariton Karamitas about ways to use FUSE for kernel exploitation from unprivileged SELinux contexts on Android.
www.youtube.com/watch?v=DJBG...
Awesome series of articles by r1ru that outlines many commonly-used modern exploitation techniques.
r1ru.github.io/categories/l...
Awesome series of articles by r1ru that outlines many commonly-used modern exploitation techniques.
r1ru.github.io/categories/l...
sam4k.com/page-table-k...

sam4k.com/page-table-k...
Includes a demonstration of how to rediscover CVE-2024-53104, an out-of-bounds bug in the USB Video Class driver.
Slides: docs.google.com/presentation...

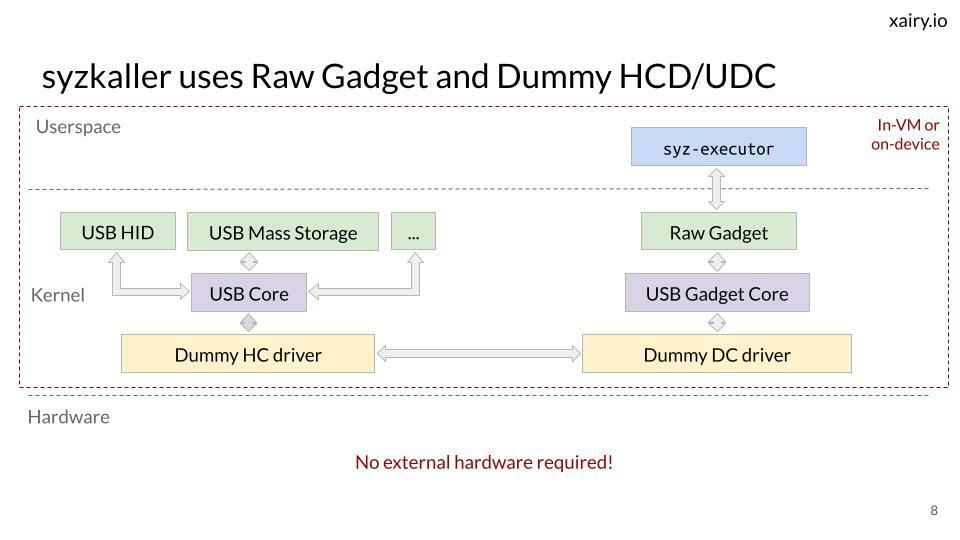
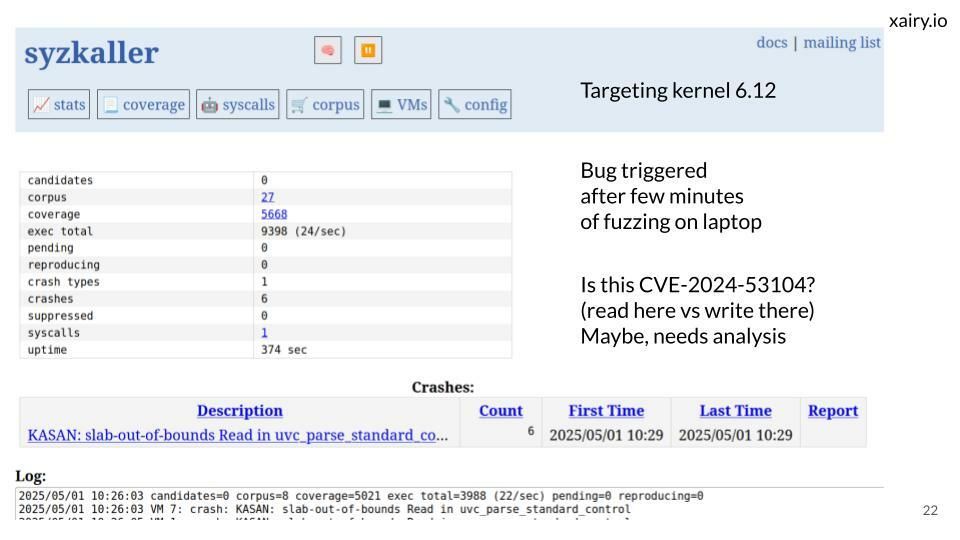
Includes a demonstration of how to rediscover CVE-2024-53104, an out-of-bounds bug in the USB Video Class driver.
Slides: docs.google.com/presentation...




