Interested? Register here: www.meetup.com/kql-cafe/eve...
📅 When: April 29 18:00 - 19:30 (CET)
🖥️ Where: Online
💰 Cost: Free of charge

Interested? Register here: www.meetup.com/kql-cafe/eve...
📅 When: April 29 18:00 - 19:30 (CET)
🖥️ Where: Online
💰 Cost: Free of charge
The queries help you to identify high-permissive, unused and external apps.
github.com/Bert-JanP/Hu...
The queries help you to identify high-permissive, unused and external apps.
github.com/Bert-JanP/Hu...
Day 100 - CScript.exe, WScript.exe or MSHTA.exe Executed from Web Browser Process
IT'S FINALLY OVER! I had another query in store for today, but I feel like this challenge wouldn't be complete without that one.
(cont)
t.co/lwO1hmrqUk
Day 100 - CScript.exe, WScript.exe or MSHTA.exe Executed from Web Browser Process
IT'S FINALLY OVER! I had another query in store for today, but I feel like this challenge wouldn't be complete without that one.
(cont)
t.co/lwO1hmrqUk
github.com/Bert-JanP/Hu...
github.com/Bert-JanP/Hu...
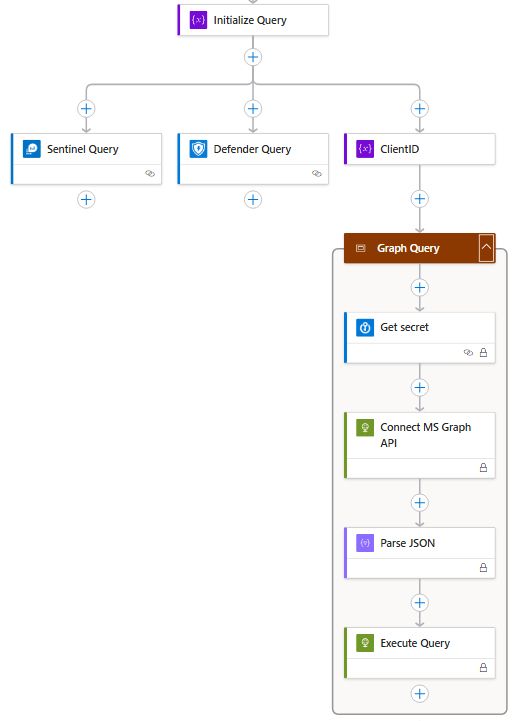
@kqlcafe.bsky.social . I will discuss #KQL, Logic Apps and hunting through the available APIs.
The session is on April 29th and is completely free to attend online.
🗓️Event registration & details: www.meetup.com/kql-cafe/
@kqlcafe.bsky.social . I will discuss #KQL, Logic Apps and hunting through the available APIs.
The session is on April 29th and is completely free to attend online.
🗓️Event registration & details: www.meetup.com/kql-cafe/
New features include:
- Granular response capabilities for Acquisition, Analysis, and Containment
- Expanded support beyond Windows, enabling Cloud response activities via Graph API
github.com/Bert-JanP/In...
New features include:
- Granular response capabilities for Acquisition, Analysis, and Containment
- Expanded support beyond Windows, enabling Cloud response activities via Graph API
github.com/Bert-JanP/In...
Query is available for AADSignInEventsBeta and SigninLogs. Less known is the AADSignInEventsBeta filter for device code:
| where EndpointCall == "Cmsi:Cmsi"
🏹Query: github.com/Bert-JanP/Hu...
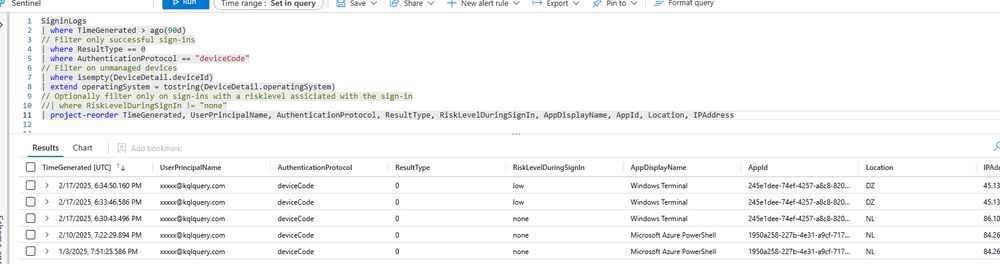
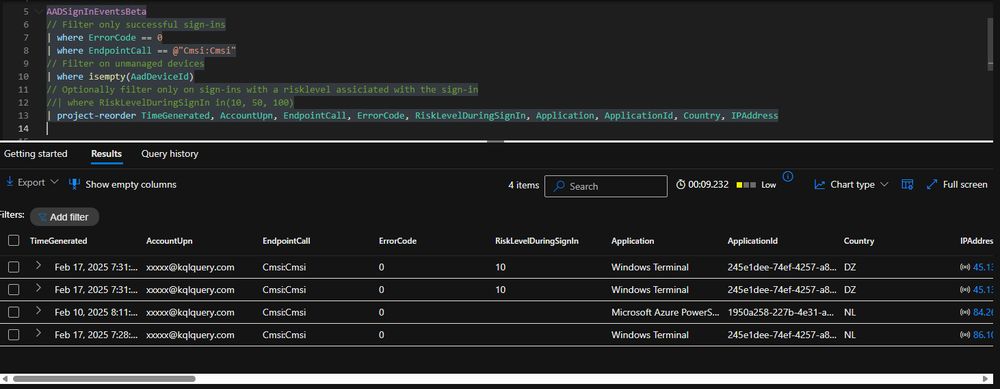
Query is available for AADSignInEventsBeta and SigninLogs. Less known is the AADSignInEventsBeta filter for device code:
| where EndpointCall == "Cmsi:Cmsi"
🏹Query: github.com/Bert-JanP/Hu...
The report includes KQL, SPL and Powershell code to perform incident response.
www.cisa.gov/resources-to...
The report includes KQL, SPL and Powershell code to perform incident response.
www.cisa.gov/resources-to...
I will probably write a small blog about the topic soon.
Deployment: github.com/Bert-JanP/Se...
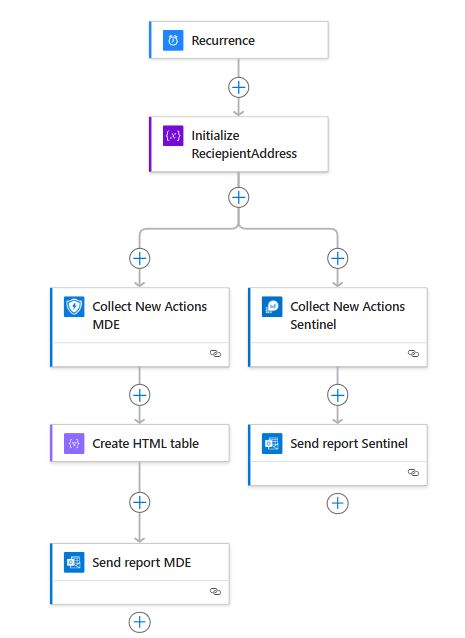
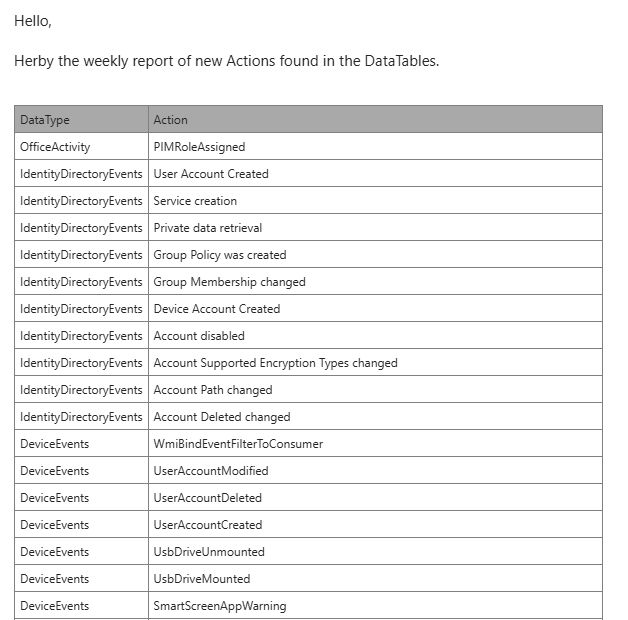
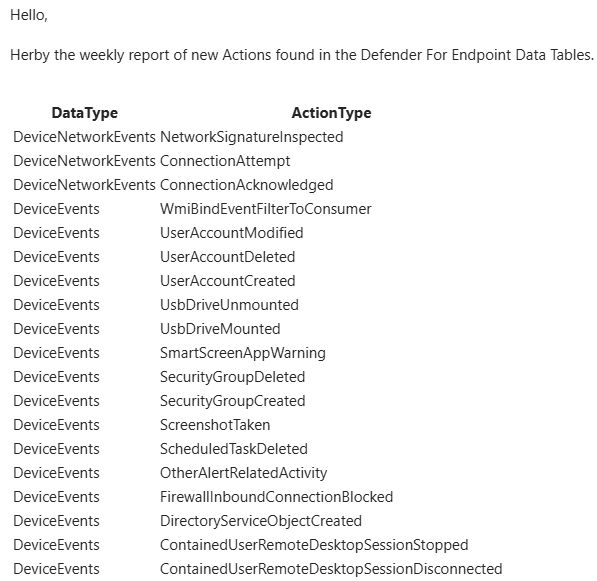
I will probably write a small blog about the topic soon.
Deployment: github.com/Bert-JanP/Se...
🗓 December update is available now kustoinsights.substack.com/p/kusto-insi...
#KustoInsights #KustoQuery #KustoQueryLanguage #KQL #MicrosoftSecurity
🗓 December update is available now kustoinsights.substack.com/p/kusto-insi...
#KustoInsights #KustoQuery #KustoQueryLanguage #KQL #MicrosoftSecurity
github.com/Bert-JanP/Hu...
github.com/Bert-JanP/Hu...
Happy hunting this year! 🏹
kqlquery.com/posts/kql-so...
Happy hunting this year! 🏹
kqlquery.com/posts/kql-so...
Az.SecurityInsights.internal\New-AzSentinelAlertRule : The maximum number of enabled Scheduled analytics rules (512)
learn.microsoft.com/en-us/azure/...
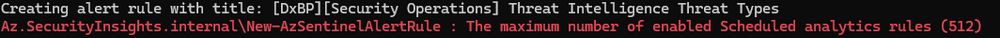
Az.SecurityInsights.internal\New-AzSentinelAlertRule : The maximum number of enabled Scheduled analytics rules (512)
learn.microsoft.com/en-us/azure/...
IOC hunting at scale using externaldata().
The blog includes queries for:
- Suspicious NamedPipes
- Tor connections
- Active CISA KEV vulnerabilities
- MISP Feeds
kqlquery.com/posts/extern...
IOC hunting at scale using externaldata().
The blog includes queries for:
- Suspicious NamedPipes
- Tor connections
- Active CISA KEV vulnerabilities
- MISP Feeds
kqlquery.com/posts/extern...
1, Supisicous Named Piped Event
2. CISA Known Exploited Vulnerabilities Visualization
3. Large Number of Analytics Rules Deleted
4. Inbound Authentication From Public IP
Individual links in 🧵
github.com/Bert-JanP/Hu...
1, Supisicous Named Piped Event
2. CISA Known Exploited Vulnerabilities Visualization
3. Large Number of Analytics Rules Deleted
4. Inbound Authentication From Public IP
Individual links in 🧵
github.com/Bert-JanP/Hu...
Source: techcommunity.microsoft.com/blog/microso...
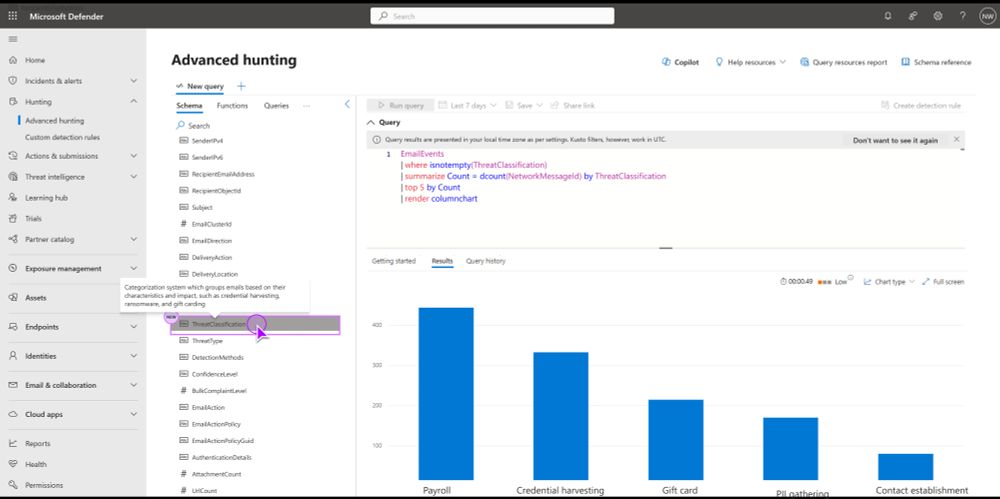
Source: techcommunity.microsoft.com/blog/microso...

If you have High-Risk users and axios useragents in the results please revoke some sessions.
🏹 github.com/Bert-JanP/Hu...
Query is available for both SigninLogs and AADSignInEventsBeta.
If you have High-Risk users and axios useragents in the results please revoke some sessions.
🏹 github.com/Bert-JanP/Hu...
Query is available for both SigninLogs and AADSignInEventsBeta.