
We’re Bishop Fox, leaders in offensive security for nearly 20 years. From pentesting to attack surface management with Cosmos, we help organizations stay ahead of attackers.
Follow us for insights, research, and cybersecurity updates!
#cybersecurity #offensivesecurity #pentesting
Pixelation ≠ redaction.
Unredacter proves it.
Play with the tool → bishopfox.com/tools/unreda...

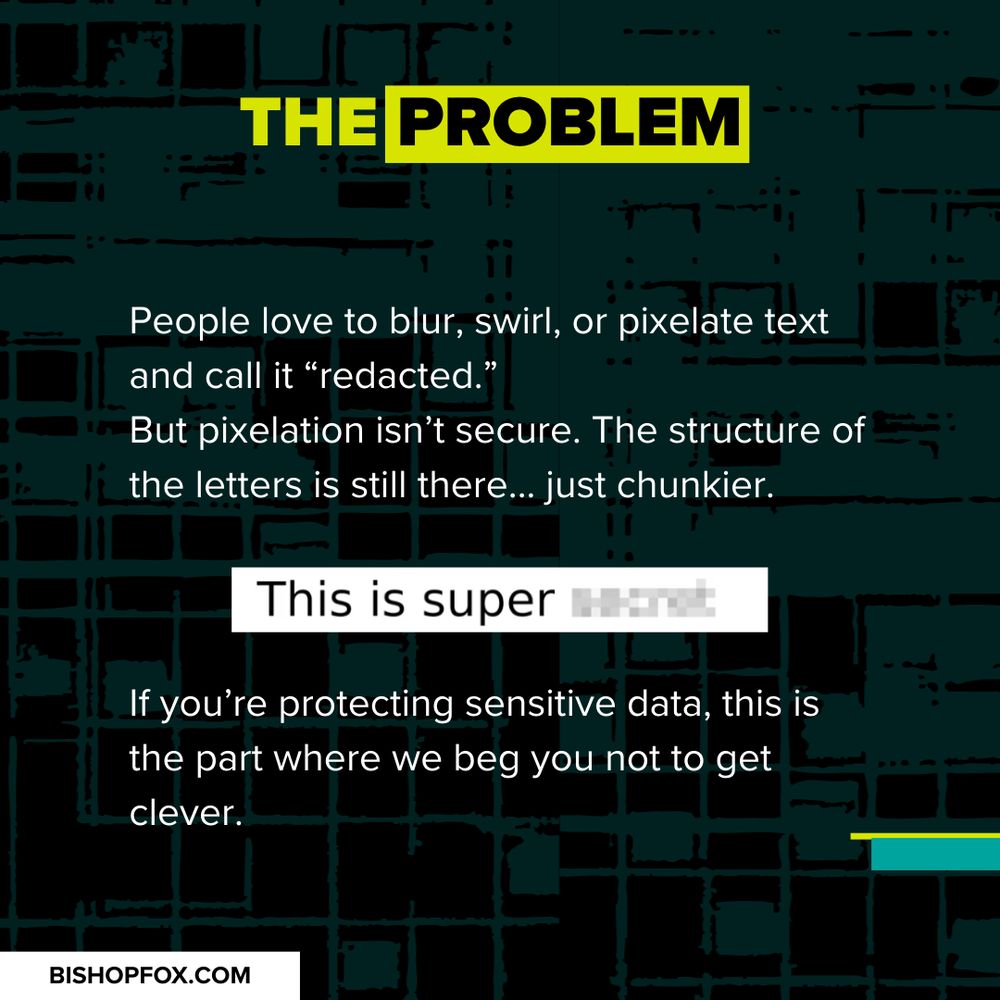


Pixelation ≠ redaction.
Unredacter proves it.
Play with the tool → bishopfox.com/tools/unreda...
Join Trevin Edgeworth tomorrow to hear how we’re evolving our Red Teaming to keep up: bishopfox.com/resources/re...

Join Trevin Edgeworth tomorrow to hear how we’re evolving our Red Teaming to keep up: bishopfox.com/resources/re...
Sliver Workshop Part 3: Building Better Encoders is starting now.
Join us to learn how Sliver handles traffic encoding and how to build custom WebAssembly-based encoders: bishopfox.com/resources/sl...

Sliver Workshop Part 3: Building Better Encoders is starting now.
Join us to learn how Sliver handles traffic encoding and how to build custom WebAssembly-based encoders: bishopfox.com/resources/sl...
Full guide here: bishopfox.com/resources/ap...

Full guide here: bishopfox.com/resources/ap...
Sliver Workshop: Building Better Encoders
2 p.m. ET / 7 p.m. GMT
Join via Discord or our site.
Tim Makram Ghatas will cover Sliver’s encoding defaults, WebAssembly, and how to design/test custom encoders.

Sliver Workshop: Building Better Encoders
2 p.m. ET / 7 p.m. GMT
Join via Discord or our site.
Tim Makram Ghatas will cover Sliver’s encoding defaults, WebAssembly, and how to design/test custom encoders.
Quickly scan GitHub for exposed secrets using flexible filtering and fuzzy matching.
Built to make large search results easier to work through.




Quickly scan GitHub for exposed secrets using flexible filtering and fuzzy matching.
Built to make large search results easier to work through.
More AI. More connected systems. More attacker automation.
Our leadership team breaks down the forces that will reshape pen testing, CISO priorities, hardware security, and Red Team specialization next year.




More AI. More connected systems. More attacker automation.
Our leadership team breaks down the forces that will reshape pen testing, CISO priorities, hardware security, and Red Team specialization next year.
On Dec 11, Trevin Edgeworth discusses how Red Teaming helps validate resilience against AI-driven threats.
2 p.m. ET
Save your seat: bishopfox.com/resources/re...

On Dec 11, Trevin Edgeworth discusses how Red Teaming helps validate resilience against AI-driven threats.
2 p.m. ET
Save your seat: bishopfox.com/resources/re...
This session covers building better encoders, how Sliver handles traffic encoding, and how to extend it with custom Wasm-based techniques.
Hosted by Senior Security Consultant Tim Makram Ghatas.

This session covers building better encoders, how Sliver handles traffic encoding, and how to extend it with custom Wasm-based techniques.
Hosted by Senior Security Consultant Tim Makram Ghatas.
2 p.m. ET / 7 p.m. GMT

2 p.m. ET / 7 p.m. GMT
If you’re exploring LLM security or Red Teaming, Broken Hill is worth a look. It automates GCG-style jailbreak testing so you can safely probe model weaknesses without heavy hardware.
Open-source here: github.com/BishopFox/Br...




If you’re exploring LLM security or Red Teaming, Broken Hill is worth a look. It automates GCG-style jailbreak testing so you can safely probe model weaknesses without heavy hardware.
Open-source here: github.com/BishopFox/Br...
Training kicks off today with Samanta, Axel, and Juan and we’ll be at the booth all conference long.
If you’re in CDMX, come stop by. We’d love to meet you.
¡Bienvenidos a BugCon 2025!
bishopfox.com/events/bugco...

Training kicks off today with Samanta, Axel, and Juan and we’ll be at the booth all conference long.
If you’re in CDMX, come stop by. We’d love to meet you.
¡Bienvenidos a BugCon 2025!
bishopfox.com/events/bugco...
Nick Cerne is demoing how researchers uncover 0-days hidden inside everyday IoT devices from firmware to hardware to mobile apps.
Jump in here ⬇️
bishopfox.com/resources/pe...

Nick Cerne is demoing how researchers uncover 0-days hidden inside everyday IoT devices from firmware to hardware to mobile apps.
Jump in here ⬇️
bishopfox.com/resources/pe...
Come say hi at the Bishop Fox booth, meet the team, and talk all things offensive security.
KSU Center – Kennesaw, GA

Come say hi at the Bishop Fox booth, meet the team, and talk all things offensive security.
KSU Center – Kennesaw, GA
Our latest blog breaks down the best Capture the Flag challenges for testing and defending large language models.
Full list: bishopfox.com/blog/ready-t...




Our latest blog breaks down the best Capture the Flag challenges for testing and defending large language models.
Full list: bishopfox.com/blog/ready-t...

Senior Security Consultant Nick Cerne will present “Peeling Back the Plastic: Finding 0-Days in IoT Devices.”
And join us Friday night at Flight Club for drinks, darts, and good times!
Nov. 6-7 | Washington, D.C.
RSVP: partiful.com/e/otaKEF0mqB...

Senior Security Consultant Nick Cerne will present “Peeling Back the Plastic: Finding 0-Days in IoT Devices.”
And join us Friday night at Flight Club for drinks, darts, and good times!
Nov. 6-7 | Washington, D.C.
RSVP: partiful.com/e/otaKEF0mqB...
Define once. Reuse everywhere. No more manual token edits!
bishopfox.com/blog/burp-va...




Define once. Reuse everywhere. No more manual token edits!
bishopfox.com/blog/burp-va...
Real-world tactics for testing & defending 5G networks.
Save your seat: bishopfox.com/resources/5g...

Real-world tactics for testing & defending 5G networks.
Save your seat: bishopfox.com/resources/5g...
Bishop Fox’s FAQ guide breaks down Threat-Led Pen Testing from planning to reporting.
bishopfox.com/resources/gu...
#DORA #TLPT

Bishop Fox’s FAQ guide breaks down Threat-Led Pen Testing from planning to reporting.
bishopfox.com/resources/gu...
#DORA #TLPT
Bishop Fox’s Nick Cerne found some new vulnerabilities that could literally open your front door.
Read his story → bishopfox.com/blog/how-a-2...
#IoTSecurity




Bishop Fox’s Nick Cerne found some new vulnerabilities that could literally open your front door.
Read his story → bishopfox.com/blog/how-a-2...
#IoTSecurity
Attackers could:
• Remotely control devices
• Intercept traffic
• Hijack sessions
Details: bishopfox.com/blog/yosmart...

Attackers could:
• Remotely control devices
• Intercept traffic
• Hijack sessions
Details: bishopfox.com/blog/yosmart...

