www.vxcon.hk

www.vxcon.hk
Thank you so much to every co-authors including Ken Wong, Dongwei Xiao, Dr. Daoyuan Wu Dr. Shuai Wang and Yiteng Peng.
What a good evening!

Thank you so much to every co-authors including Ken Wong, Dongwei Xiao, Dr. Daoyuan Wu Dr. Shuai Wang and Yiteng Peng.
What a good evening!
@rwx.page

@rwx.page
cloud.google.com/blog/topics/...

cloud.google.com/blog/topics/...

Getting money from Google is mission impossible.

Getting money from Google is mission impossible.
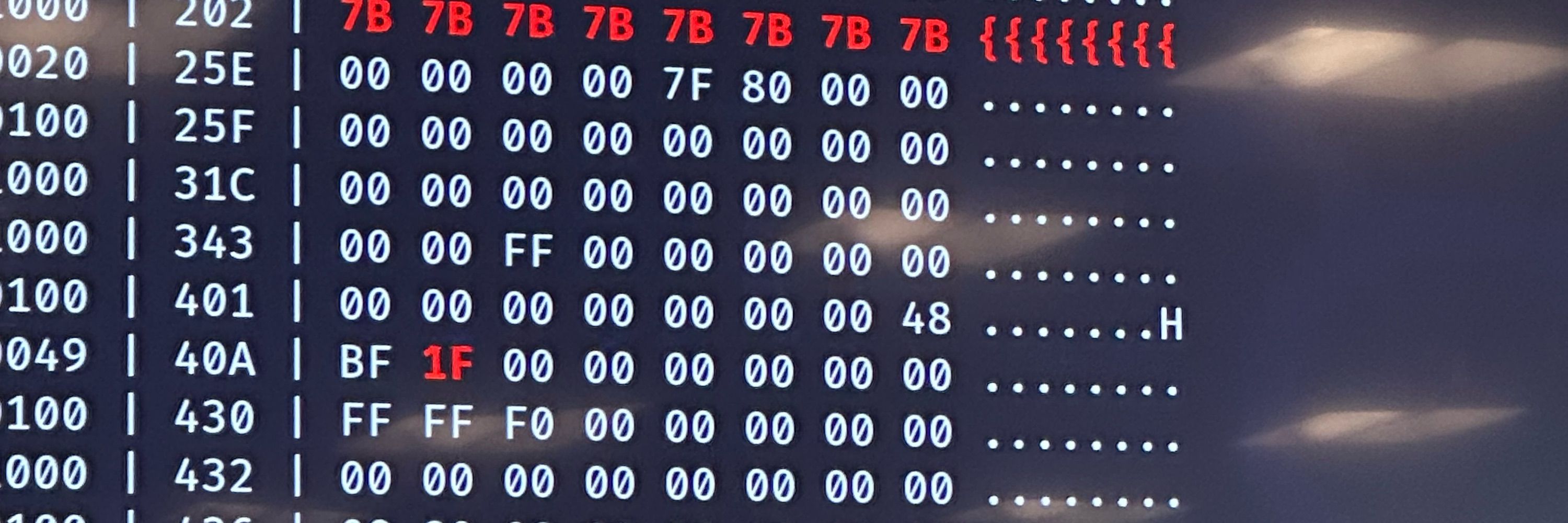
This should be one of the last pieces of infrastructure required for the sandbox.
This should be one of the last pieces of infrastructure required for the sandbox.
The V8 Heap Sandbox: saelo.github.io/presentation...
Fantastic conference, as usual! :)
The V8 Heap Sandbox: saelo.github.io/presentation...
Fantastic conference, as usual! :)
* No longer limited to d8
* Rewards for controlled writes increased to $20k
* Any memory corruption outside the sandbox is now in scope
bughunters.google.com/about/rules/...
Happy hacking!

* No longer limited to d8
* Rewards for controlled writes increased to $20k
* Any memory corruption outside the sandbox is now in scope
bughunters.google.com/about/rules/...
Happy hacking!








