
Hans-Martin Münch
@h0ng10.bsky.social
CEO at MOGWAI LABS, part time CTF player and bboy
Reposted by Hans-Martin Münch
New security advisory: Generex RCCMDTray Remote OS Command Execution. mogwailabs.de/en/advisorie...

Generex RCCMDTray Remote OS Command Execution
mogwailabs.de
August 4, 2025 at 12:36 PM
New security advisory: Generex RCCMDTray Remote OS Command Execution. mogwailabs.de/en/advisorie...
Reposted by Hans-Martin Münch
Ever thought your kitchen appliance could harbor a persistent threat?
We reverse-engineered the Thermomix TM5 and uncovered vulnerabilities allowing arbitrary code execution, persistence, and secure boot bypass.
Discover our step-by-step breakdown!
www.synacktiv.com/en/publicati...
We reverse-engineered the Thermomix TM5 and uncovered vulnerabilities allowing arbitrary code execution, persistence, and secure boot bypass.
Discover our step-by-step breakdown!
www.synacktiv.com/en/publicati...

Let Me Cook You a Vulnerability: Exploiting the Thermomix TM5
Hardware Analysis The Thermomix TM5 is a multifunctional kitchen appliance composed of two key electronic boards: the power board, which handles the motor and heating functions, and the main board, w
www.synacktiv.com
July 11, 2025 at 8:44 AM
Ever thought your kitchen appliance could harbor a persistent threat?
We reverse-engineered the Thermomix TM5 and uncovered vulnerabilities allowing arbitrary code execution, persistence, and secure boot bypass.
Discover our step-by-step breakdown!
www.synacktiv.com/en/publicati...
We reverse-engineered the Thermomix TM5 and uncovered vulnerabilities allowing arbitrary code execution, persistence, and secure boot bypass.
Discover our step-by-step breakdown!
www.synacktiv.com/en/publicati...
Reposted by Hans-Martin Münch
Beacon Object Files... Five Years On
aff-wg.org/2025/06/26/b...
I released BOFs with Cobalt Strike 4.1 five years ago. This is some history on the feature and what led to it. My thinking at the time. A few thoughts on current discourse.
aff-wg.org/2025/06/26/b...
I released BOFs with Cobalt Strike 4.1 five years ago. This is some history on the feature and what led to it. My thinking at the time. A few thoughts on current discourse.
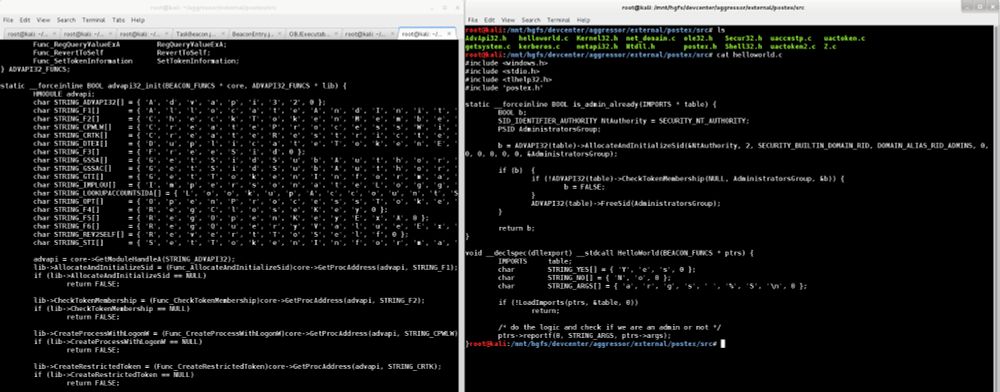
Beacon Object Files – Five Years On…
When I was active in the red teaming space, one of my stated goals was to act on problems with solutions that would have utility 5-10 years from the time of their release. This long-term thinking w…
aff-wg.org
June 26, 2025 at 6:48 PM
Beacon Object Files... Five Years On
aff-wg.org/2025/06/26/b...
I released BOFs with Cobalt Strike 4.1 five years ago. This is some history on the feature and what led to it. My thinking at the time. A few thoughts on current discourse.
aff-wg.org/2025/06/26/b...
I released BOFs with Cobalt Strike 4.1 five years ago. This is some history on the feature and what led to it. My thinking at the time. A few thoughts on current discourse.
Reposted by Hans-Martin Münch
We just added a new vulnerability to our "bug parade" page. If you are using 4D based applications, please ensure that you are on the latest patch level to avoid potential security risks.
mogwailabs.de/en/advisorie...
mogwailabs.de/en/advisorie...

4D Unauthenticated File Disclosure
mogwailabs.de
June 25, 2025 at 9:07 AM
We just added a new vulnerability to our "bug parade" page. If you are using 4D based applications, please ensure that you are on the latest patch level to avoid potential security risks.
mogwailabs.de/en/advisorie...
mogwailabs.de/en/advisorie...
Reposted by Hans-Martin Münch
A quick-and-dirty late night blog post on discovering an nday variant in Zyxel NWA50AX Pro devices
frycos.github.io/vulns4free/2...
frycos.github.io/vulns4free/2...
Zyxel NWA50AX Pro - Discovery of an Nday Variant
Today was an eventful day thanks to many interesting blog posts, e.g. from my friends at watchTowr. So I thought, why not publish a small quick-and-dirty blog post myself about a story from last week?...
frycos.github.io
June 17, 2025 at 9:12 PM
A quick-and-dirty late night blog post on discovering an nday variant in Zyxel NWA50AX Pro devices
frycos.github.io/vulns4free/2...
frycos.github.io/vulns4free/2...
Reposted by Hans-Martin Münch
Reposted by Hans-Martin Münch
Reposted by Hans-Martin Münch
OffensiveCon 25 videos are out. Thank you @offensivecon www.youtube.com/watch?v=goEb...

OffensiveCon25 - Cedric Halbronn and Jael Koh
YouTube video by OffensiveCon
www.youtube.com
May 20, 2025 at 8:54 AM
OffensiveCon 25 videos are out. Thank you @offensivecon www.youtube.com/watch?v=goEb...
Reposted by Hans-Martin Münch
Yes, we're beating a dead horse. But that horse still runs in corporate networks - and quietly gives attackers the keys to the kingdom. We're publishing what’s long been exploitable. Time to talk about it. #DSM #Ivanti code-white.com/blog/ivanti-...
CODE WHITE | Analyzing the Attack Surface of Ivanti's DSM
Ivanti's Desktop & Server Management (DSM) product is an old acquaintance that we have encountered in numerous red team and
internal assessments. The main purpose of the product is the centralized dis...
code-white.com
May 13, 2025 at 6:45 AM
Yes, we're beating a dead horse. But that horse still runs in corporate networks - and quietly gives attackers the keys to the kingdom. We're publishing what’s long been exploitable. Time to talk about it. #DSM #Ivanti code-white.com/blog/ivanti-...
Reposted by Hans-Martin Münch
Reposted by Hans-Martin Münch
From iframes and file reads to full RCE. 🔥
We found an HTML-to-PDF API allowing file reads and SSRF - then chained it into remote code execution via a Chromium 62 WebView exploit.
👉 Read the full write-up here: neodyme.io/en/blog/html...
We found an HTML-to-PDF API allowing file reads and SSRF - then chained it into remote code execution via a Chromium 62 WebView exploit.
👉 Read the full write-up here: neodyme.io/en/blog/html...
HTML to PDF Renderer: A tale of local file access and shellcode execution
In a recent engagement, we found an HTML to PDF converter API endpoint that allowed us to list local directories and files on a remote server. One of the PDF files we created, revealed that the conver...
neodyme.io
May 2, 2025 at 11:03 AM
From iframes and file reads to full RCE. 🔥
We found an HTML-to-PDF API allowing file reads and SSRF - then chained it into remote code execution via a Chromium 62 WebView exploit.
👉 Read the full write-up here: neodyme.io/en/blog/html...
We found an HTML-to-PDF API allowing file reads and SSRF - then chained it into remote code execution via a Chromium 62 WebView exploit.
👉 Read the full write-up here: neodyme.io/en/blog/html...
AppSec Ezine Edition #584
pathonproject.com/zb/?39a1a5b0...
pathonproject.com/zb/?39a1a5b0...
AppSec Ezine
pathonproject.com
April 25, 2025 at 1:17 PM
AppSec Ezine Edition #584
pathonproject.com/zb/?39a1a5b0...
pathonproject.com/zb/?39a1a5b0...
Reposted by Hans-Martin Münch
A few quick notes on the Erlang OTP SSHd RCE (CVE-2025-32433) [1/3]
1. Cisco confirmed that their ConfD and NSO products are affected. The ConfD patch is planned for May. These often run on ports 830, 2022, and 2024 versus 22.
sec.cloudapps.cisco.com/security/cen...
1. Cisco confirmed that their ConfD and NSO products are affected. The ConfD patch is planned for May. These often run on ports 830, 2022, and 2024 versus 22.
sec.cloudapps.cisco.com/security/cen...
Cisco Security Advisory: Multiple Cisco Products Unauthenticated Remote Code Execution in Erlang/OTP SSH Server: April 2025
On April 16, 2025, a critical vulnerability in the Erlang/OTP SSH server was disclosed. This vulnerability could allow an unauthenticated, remote attacker to perform remote code execution (RCE) on an…
sec.cloudapps.cisco.com
April 24, 2025 at 4:50 AM
A few quick notes on the Erlang OTP SSHd RCE (CVE-2025-32433) [1/3]
1. Cisco confirmed that their ConfD and NSO products are affected. The ConfD patch is planned for May. These often run on ports 830, 2022, and 2024 versus 22.
sec.cloudapps.cisco.com/security/cen...
1. Cisco confirmed that their ConfD and NSO products are affected. The ConfD patch is planned for May. These often run on ports 830, 2022, and 2024 versus 22.
sec.cloudapps.cisco.com/security/cen...
Reposted by Hans-Martin Münch
The profile you need to create has been documented by the PortSwigger's support team 🔍
Scroll down to the end of the following thread and simply copy the provided config to /etc/apparmor.d/burpbrowser 💪
forum.portswigger.net/thread/burp-...
Scroll down to the end of the following thread and simply copy the provided config to /etc/apparmor.d/burpbrowser 💪
forum.portswigger.net/thread/burp-...
April 15, 2025 at 8:20 AM
The profile you need to create has been documented by the PortSwigger's support team 🔍
Scroll down to the end of the following thread and simply copy the provided config to /etc/apparmor.d/burpbrowser 💪
forum.portswigger.net/thread/burp-...
Scroll down to the end of the following thread and simply copy the provided config to /etc/apparmor.d/burpbrowser 💪
forum.portswigger.net/thread/burp-...
Good analysis of CVE-2025-30065 (Java Deserialization Vulnerability in Apache Parket). I would that (depending on the Java version) it possible to use a gadget that causes an outgoing JNDI call. attackerkb.com/topics/jAhVR...

CVE-2025-30065 | AttackerKB
Schema parsing in the parquet-avro module of Apache Parquet 1.15.0 and previous versions allows bad actors to execute arbitrary code Users are recommended to u…
attackerkb.com
April 11, 2025 at 7:59 AM
Good analysis of CVE-2025-30065 (Java Deserialization Vulnerability in Apache Parket). I would that (depending on the Java version) it possible to use a gadget that causes an outgoing JNDI call. attackerkb.com/topics/jAhVR...
Reposted by Hans-Martin Münch
Our crew members @mwulftange.bsky.social & @frycos.bsky.social discovered & responsibly disclosed several new RCE gadgets that bypass #Veeam 's blacklist for CVE-2024-40711 & CVE-2025-23120 + further entry points after @sinsinology.bsky.social & @chudypb.bsky.social 's blog. Replace BinaryFormatter!
March 28, 2025 at 4:35 PM
Our crew members @mwulftange.bsky.social & @frycos.bsky.social discovered & responsibly disclosed several new RCE gadgets that bypass #Veeam 's blacklist for CVE-2024-40711 & CVE-2025-23120 + further entry points after @sinsinology.bsky.social & @chudypb.bsky.social 's blog. Replace BinaryFormatter!
Private Key reuse for requesting https certificates is the new "outdated JavaScript libraries" for penetration testers.
- Large number of services affected
- Easy to find / verify
- Hard to actually exploit
Still nice research from the Truffle Security Team.
www.youtube.com/watch?v=gyyt...
- Large number of services affected
- Easy to find / verify
- Hard to actually exploit
Still nice research from the Truffle Security Team.
www.youtube.com/watch?v=gyyt...

Millions Of Public Certificates Are Reusing Old Private Keys - Dylan Ayrey, Joseph Leon
YouTube video by OWASP Foundation
www.youtube.com
March 28, 2025 at 11:52 AM
Private Key reuse for requesting https certificates is the new "outdated JavaScript libraries" for penetration testers.
- Large number of services affected
- Easy to find / verify
- Hard to actually exploit
Still nice research from the Truffle Security Team.
www.youtube.com/watch?v=gyyt...
- Large number of services affected
- Easy to find / verify
- Hard to actually exploit
Still nice research from the Truffle Security Team.
www.youtube.com/watch?v=gyyt...
Reposted by Hans-Martin Münch
Happy to share my slides from BOOTSTRAP25. Unfortunately the bug discussed is still not patched in Linux 6.14.0 despite it being reported explicitly. Slides are in markdown but there's a PDF in "releases" too github.com/jduck/bs25-s...
GitHub - jduck/bs25-slides: Slides from "Musing from Decades of Linux Kernel Security Research" at BOOTSTRAP25
Slides from "Musing from Decades of Linux Kernel Security Research" at BOOTSTRAP25 - jduck/bs25-slides
github.com
March 25, 2025 at 7:26 PM
Happy to share my slides from BOOTSTRAP25. Unfortunately the bug discussed is still not patched in Linux 6.14.0 despite it being reported explicitly. Slides are in markdown but there's a PDF in "releases" too github.com/jduck/bs25-s...
Reposted by Hans-Martin Münch
Today, Wiz (Woogle?) released an advisory detailing an attack chain they’ve dubbed IngressNightmare, which, if left exposed and unpatched, can be exploited to achieve remote code execution by unauthenticated attackers. Read more at www.runzero.com/blog/ingress...

March 25, 2025 at 12:23 AM
Today, Wiz (Woogle?) released an advisory detailing an attack chain they’ve dubbed IngressNightmare, which, if left exposed and unpatched, can be exploited to achieve remote code execution by unauthenticated attackers. Read more at www.runzero.com/blog/ingress...


