
Surfing the information super highway one keystroke at a time.
https://haxrob.net
(1/21)
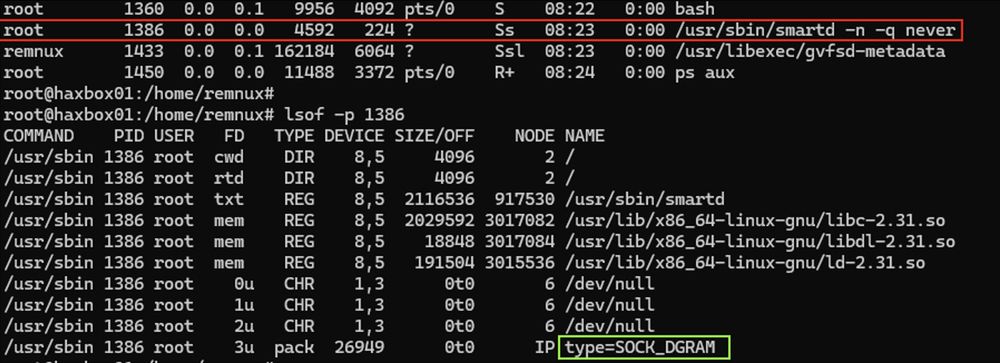
(1/21)



✅ Tailored process name masquerading
✅ Port knocking
✅ Self destruct capability
✅ Overwrites disk artefacts with /dev/urandom
✅ Found on compromised gov infrastructure
✅ Linux / #golang
❌ IoCs but no samples anywhere to be found 😭
✅ Tailored process name masquerading
✅ Port knocking
✅ Self destruct capability
✅ Overwrites disk artefacts with /dev/urandom
✅ Found on compromised gov infrastructure
✅ Linux / #golang
❌ IoCs but no samples anywhere to be found 😭


