"Offline Extraction of Symantec Account Connectivity Credentials (ACCs)"
Following my previous post on the subject, here is how to extract ACCs purely offline.
👉 itm4n.github.io/offline-extr...
#redteam #pentesting
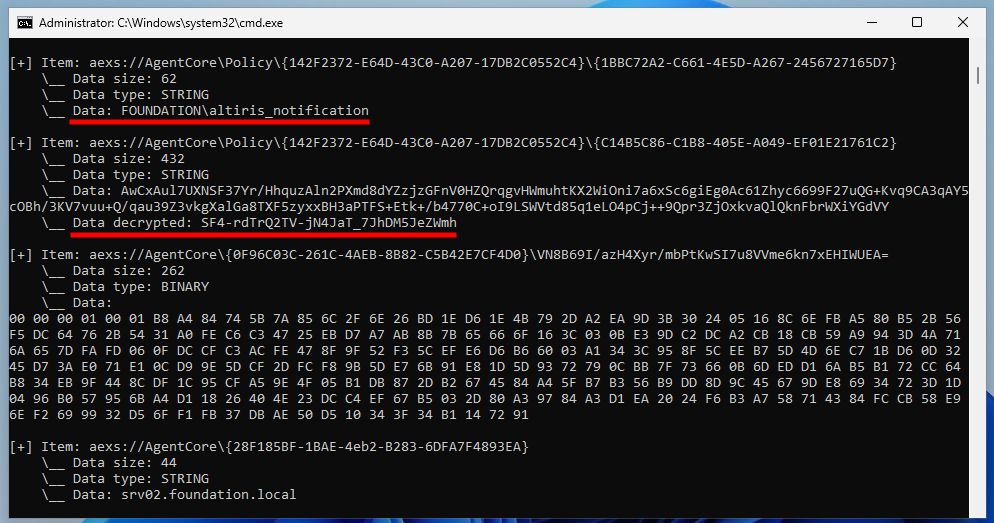
"Offline Extraction of Symantec Account Connectivity Credentials (ACCs)"
Following my previous post on the subject, here is how to extract ACCs purely offline.
👉 itm4n.github.io/offline-extr...
#redteam #pentesting
"Checking for Symantec Account Connectivity Credentials (ACCs) with PrivescCheck"
This blog post is not so much about PrivescCheck, but rather brings additional insight to the original article published by MDSec on the subject.
👉 itm4n.github.io/checking-sym...
#redteam
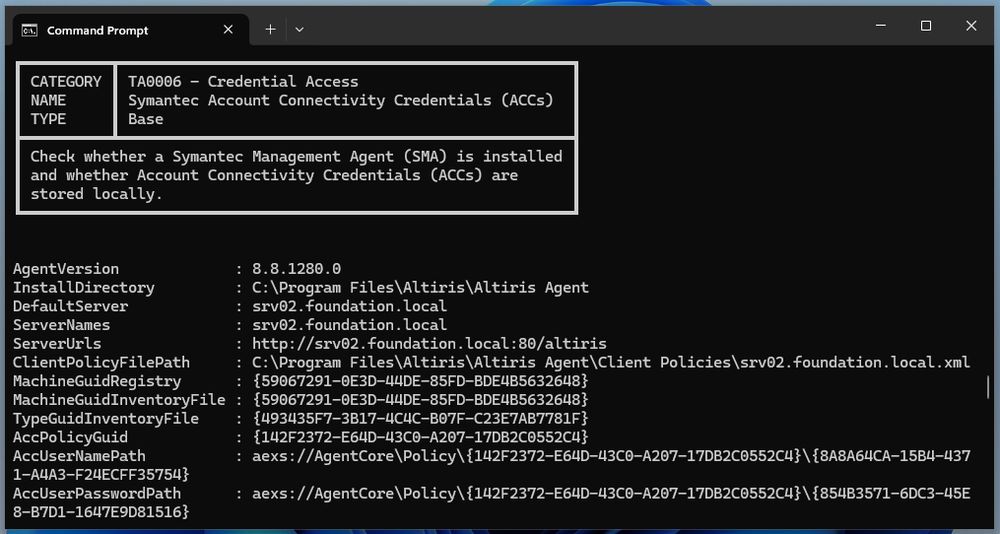
"Checking for Symantec Account Connectivity Credentials (ACCs) with PrivescCheck"
This blog post is not so much about PrivescCheck, but rather brings additional insight to the original article published by MDSec on the subject.
👉 itm4n.github.io/checking-sym...
#redteam
'Hijacking the Windows "MareBackup" Scheduled Task for Privilege Escalation'
👉 blog.scrt.ch/2025/05/20/h...
#pentest #pentesting #redteam #windows #privilegeescalation
'Hijacking the Windows "MareBackup" Scheduled Task for Privilege Escalation'
👉 blog.scrt.ch/2025/05/20/h...
#pentest #pentesting #redteam #windows #privilegeescalation
www.incendium.rocks/posts/Automa...
The writing quality is also excellent. 📝
#windows #research
www.incendium.rocks/posts/Automa...
The writing quality is also excellent. 📝
#windows #research
blog.compass-security.com/2025/04/3-mi...
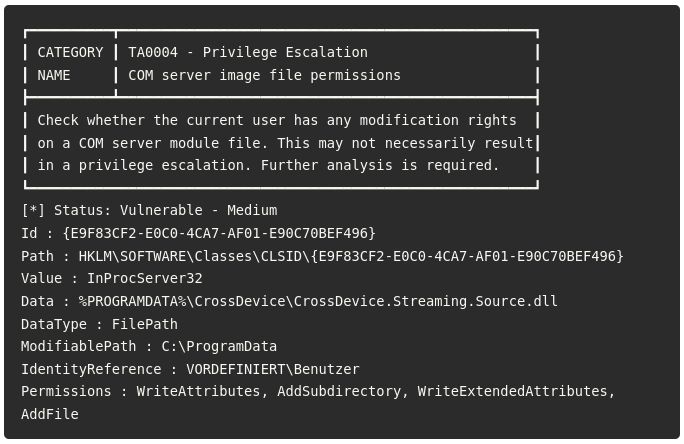
blog.compass-security.com/2025/04/3-mi...
👉 blog.scrt.ch/2025/02/18/r...
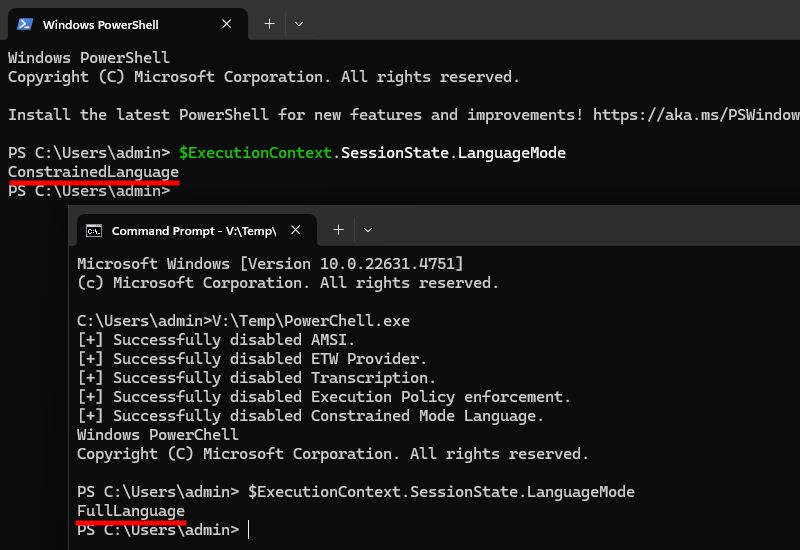
👉 blog.scrt.ch/2025/02/18/r...

"Windows BitLocker -- Screwed without a Screwdriver"
👉 neodyme.io/en/blog/bitl...
👉 media.ccc.de/v/38c3-windo...

"Windows BitLocker -- Screwed without a Screwdriver"
👉 neodyme.io/en/blog/bitl...
👉 media.ccc.de/v/38c3-windo...
Hopefully, this should provide a better understanding of the whole "PrintNightmare" situation to both defenders and red teamers. 🤞
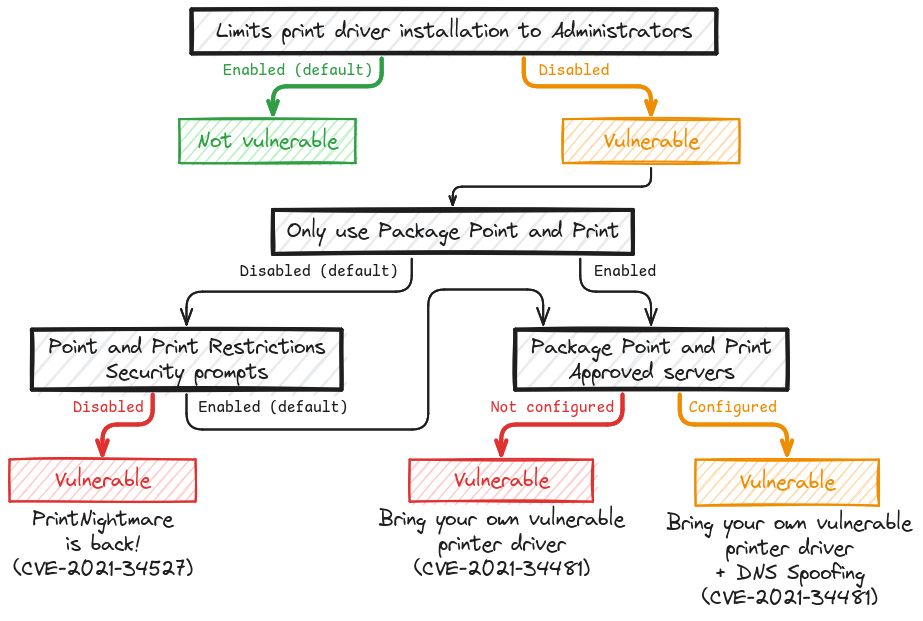
Hopefully, this should provide a better understanding of the whole "PrintNightmare" situation to both defenders and red teamers. 🤞
This change completely remediates the "Airstrike" attack as well. 🤯
support.microsoft.com/en-us/topic/...
This change completely remediates the "Airstrike" attack as well. 🤯
support.microsoft.com/en-us/topic/...
A Kerberos relay & forwarder for MiTM attacks!
>Relays Kerberos AP-REQ tickets
>Manages multiple SMB consoles
>Works on Win& Linux with .NET 8.0
>...
GitHub: github.com/decoder-it/K...

A Kerberos relay & forwarder for MiTM attacks!
>Relays Kerberos AP-REQ tickets
>Manages multiple SMB consoles
>Works on Win& Linux with .NET 8.0
>...
GitHub: github.com/decoder-it/K...
In my latest mini research project, I've been working with my teammate @PMa1n (X) on extending the work of @floesen_ (X) on the KsecDD driver. I'm thrilled to finally share the results.
👉 blog.scrt.ch/2024/11/11/e...
In my latest mini research project, I've been working with my teammate @PMa1n (X) on extending the work of @floesen_ (X) on the KsecDD driver. I'm thrilled to finally share the results.
👉 blog.scrt.ch/2024/11/11/e...
Write-up about the discovery and exploitation of a UAF vulnerability in the Windows Telephony service + CFG bypass leading to local privilege escalation. 🔥🔥🔥
whereisk0shl.top/post/a-trick...
Write-up about the discovery and exploitation of a UAF vulnerability in the Windows Telephony service + CFG bypass leading to local privilege escalation. 🔥🔥🔥
whereisk0shl.top/post/a-trick...
ℹ️ The script can now enumerate dangerous default file extension associations, such as '.bat' or '.wsh'.
⚠️ A manual review of the result is always recommended, but for the most part, it should be fine.
github.com/itm4n/Prives...
ℹ️ The script can now enumerate dangerous default file extension associations, such as '.bat' or '.wsh'.
⚠️ A manual review of the result is always recommended, but for the most part, it should be fine.
github.com/itm4n/Prives...
ℹ️ Nothing new under the sun, you might think?! Well, think twice, because this seemingly trivial task took an unexpected turn.
👉 itm4n.github.io/peap-credent...

ℹ️ Nothing new under the sun, you might think?! Well, think twice, because this seemingly trivial task took an unexpected turn.
👉 itm4n.github.io/peap-credent...

