
1. "Nonce CSP bypass using Disk Cache" on my blog
2 "Stopping Redirects" with @ctbbpodcast.bsky.social
Go vote!
portswigger.net/polls/top-10...

1. "Nonce CSP bypass using Disk Cache" on my blog
2 "Stopping Redirects" with @ctbbpodcast.bsky.social
Go vote!
portswigger.net/polls/top-10...
It featured a cool combination of JavaScript injections to escape our context and fix the remaining syntax. Check it out:
jorianwoltjer.com/blog/p/ctf/h...

It featured a cool combination of JavaScript injections to escape our context and fix the remaining syntax. Check it out:
jorianwoltjer.com/blog/p/ctf/h...
One of the most fun ones I've ever played. Loved the unique format by @renwax23.bsky.social!
jorianwoltjer.com/blog/p/ctf/i...

One of the most fun ones I've ever played. Loved the unique format by @renwax23.bsky.social!
jorianwoltjer.com/blog/p/ctf/i...
Enjoy!
lab.ctbb.show/research/sto...

Enjoy!
lab.ctbb.show/research/sto...
this one talks about a new web vulnerability class i discovered that allows for complex interactive cross-origin attacks and data exfiltration
and i've already used it to get a google docs bounty ^^
have fun <3
lyra.horse/blog/2025/12...
this one talks about a new web vulnerability class i discovered that allows for complex interactive cross-origin attacks and data exfiltration
and i've already used it to get a google docs bounty ^^
have fun <3
lyra.horse/blog/2025/12...
I feel like it might be useful as impact in Request Tunneling👀

I feel like it might be useful as impact in Request Tunneling👀
I found several interesting techniques that can help tricky situations, such as using the Connection Pool to make Client-Side Race Conditions easier!
Read the whole thing on my blog:
jorianwoltjer.com/blog/p/ctf/o...
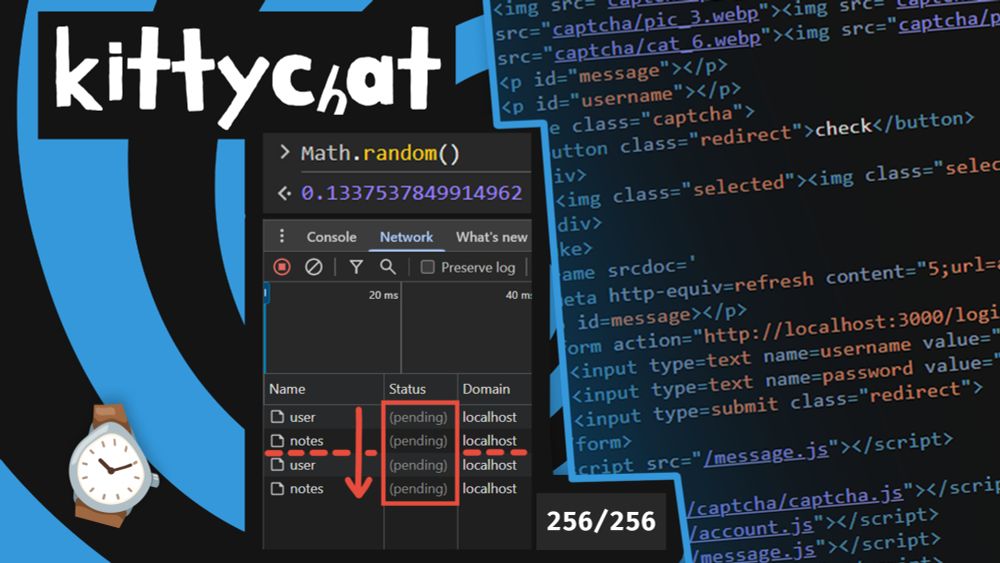
I found several interesting techniques that can help tricky situations, such as using the Connection Pool to make Client-Side Race Conditions easier!
Read the whole thing on my blog:
jorianwoltjer.com/blog/p/ctf/o...

I found several interesting techniques that can help tricky situations, such as using the Connection Pool to make Client-Side Race Conditions easier!
Read the whole thing on my blog:
jorianwoltjer.com/blog/p/ctf/o...
* Nonce CSS leak in MathML: lab.ctbb.show/research/lea...
* HTML fun facts: lab.ctbb.show/research/htm...
* Nonce CSS leak in MathML: lab.ctbb.show/research/lea...
* HTML fun facts: lab.ctbb.show/research/htm...
Super excited to be part of this team, can't wait to see what crazy research is gonna come from this!
lab.ctbb.show/research/Exp...
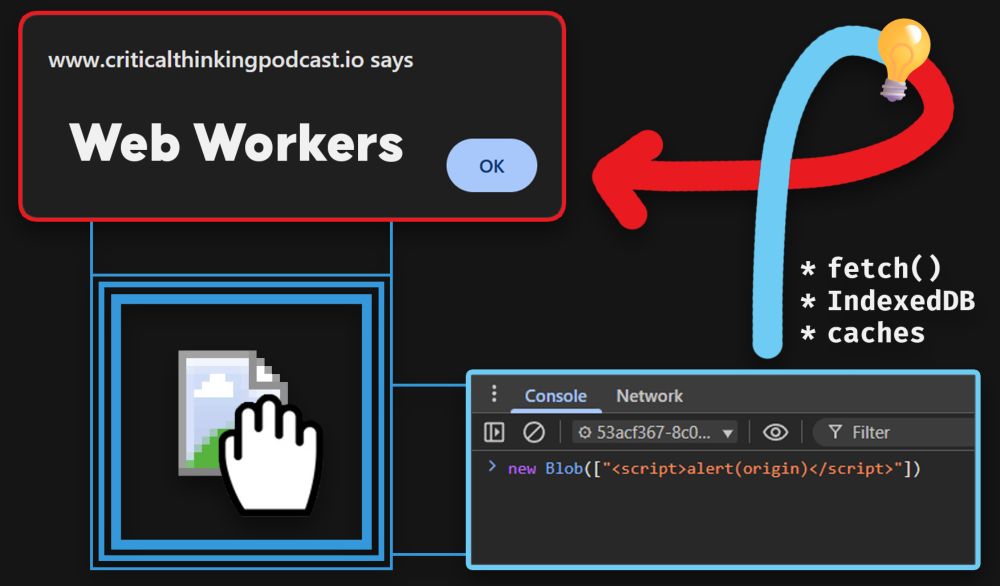
Super excited to be part of this team, can't wait to see what crazy research is gonna come from this!
lab.ctbb.show/research/Exp...
Check out this crazy impact labeled as "working as intended":
blog.babelo.xyz/posts/cross-...

Check out this crazy impact labeled as "working as intended":
blog.babelo.xyz/posts/cross-...
All you need is an <iframe>, <object> or <embed> set to about:blank, with a dangling name= attribute. This vulnerable page should be iframable.

All you need is an <iframe>, <object> or <embed> set to about:blank, with a dangling name= attribute. This vulnerable page should be iframable.
I'm a bit late, but worth trying if you haven't already :D
Otherwise, my solution is below, it's a really fun technique that makes me re-evaluate all the .source checks I've seen before...

I'm a bit late, but worth trying if you haven't already :D
Otherwise, my solution is below, it's a really fun technique that makes me re-evaluate all the .source checks I've seen before...
Check out my writeup below:
jorianwoltjer.com/blog/p/ctf/i...

Check out my writeup below:
jorianwoltjer.com/blog/p/ctf/i...
But, it involves some very interesting Mutation XSS & DOM Clobbering fun combined with a CSP Bypass using the powerful SocketIO gadget.
Everything's explained in my writeup below!
jorianwoltjer.com/blog/p/ctf/i...
But, it involves some very interesting Mutation XSS & DOM Clobbering fun combined with a CSP Bypass using the powerful SocketIO gadget.
Everything's explained in my writeup below!
jorianwoltjer.com/blog/p/ctf/i...
Don't let that HTML-injection of yours wait!
jorianwoltjer.com/blog/p/resea...
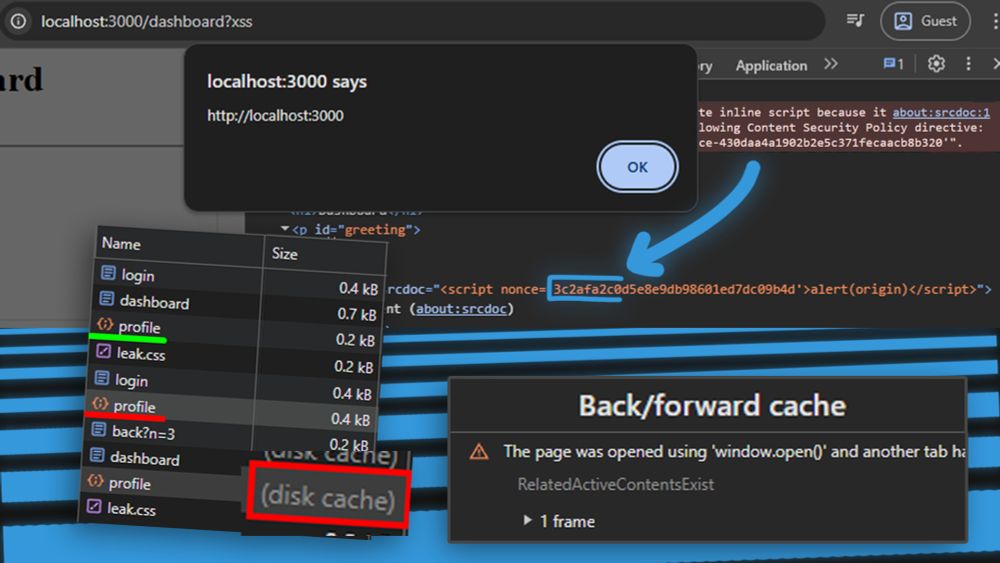
Don't let that HTML-injection of yours wait!
jorianwoltjer.com/blog/p/resea...
Source JS:
gist.github.com/JorianWoltje...
URL:
greeting-chall.jorianwoltjer.com
Found a solution? Please DM to avoid spoilers, thanks!

Source JS:
gist.github.com/JorianWoltje...
URL:
greeting-chall.jorianwoltjer.com
Found a solution? Please DM to avoid spoilers, thanks!
*XSS on any localhost origin makes RCE possible on selenium!*
jorianwoltjer.com/blog/p/ctf/i...

*XSS on any localhost origin makes RCE possible on selenium!*
jorianwoltjer.com/blog/p/ctf/i...

jorianwoltjer.com/blog/p/ctf/i...
t.co/hox8lncSEN
t.co/hox8lncSEN
debug(DOMParser.prototype.parseFromString)

debug(DOMParser.prototype.parseFromString)
This one's about an tricky file write vulnerability on Windows in OBS. By crafting an image with very specific pixels, we can plant a backdoor on your PC all from an attacker's site by misconfiguring:
jorianwoltjer.com/blog/p/resea...
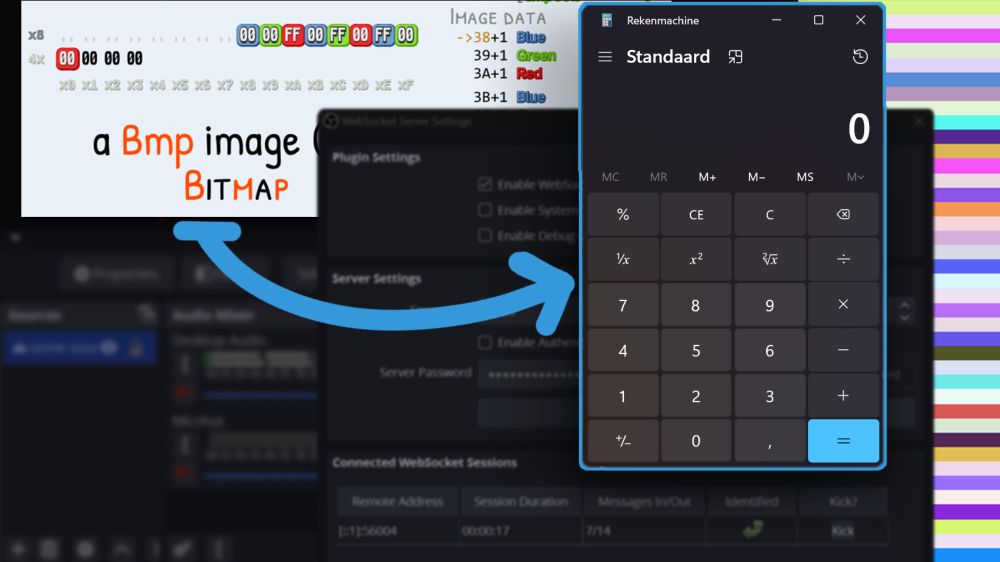
This one's about an tricky file write vulnerability on Windows in OBS. By crafting an image with very specific pixels, we can plant a backdoor on your PC all from an attacker's site by misconfiguring:
jorianwoltjer.com/blog/p/resea...
t=(S,...V)=>(e=$=>$?._?$:$?.map?$.map(e).join``:($+'').replace(/[&"'<>]/g,c=>`&#${c.charCodeAt()};`),(o=Object(S.reduce((a,p,i)=>a+e(V[i-1])+p)))._=1,o);
t=(S,...V)=>(e=$=>$?._?$:$?.map?$.map(e).join``:($+'').replace(/[&"'<>]/g,c=>`&#${c.charCodeAt()};`),(o=Object(S.reduce((a,p,i)=>a+e(V[i-1])+p)))._=1,o);

