(it simply scrapes recent isogeny papers from ePrint, and formats these nicely)

asiacrypt.iacr.org/2025/program...

asiacrypt.iacr.org/2025/program...
Be sure to join us again next Tuesday at the usual time :) isogeny.club

Be sure to join us again next Tuesday at the usual time :) isogeny.club
menezesfest.info
If you're coming to Medellín, consider attending!
menezesfest.info
If you're coming to Medellín, consider attending!
A curated list of the seven foremost unsolved problems in isogeny-based cryptography. Solving one of these profound questions would mark a monumental advance, and as a resolver you'd get eternal honor and epic rewards!
Full list: isogeni.es/problems
A curated list of the seven foremost unsolved problems in isogeny-based cryptography. Solving one of these profound questions would mark a monumental advance, and as a resolver you'd get eternal honor and epic rewards!
Full list: isogeni.es/problems


#PQCSA #PQC #postquantum #eudigital

#PQCSA #PQC #postquantum #eudigital

“KLPT²: Algebraic Pathfinding in Dimension Two and Applications” received the Best Paper Award. 🏆
Co-authored by COSIC’s Wouter Castryck & Thomas Decru (presenter).
Read it here: eprint.iacr.org/2025/372

“KLPT²: Algebraic Pathfinding in Dimension Two and Applications” received the Best Paper Award. 🏆
Co-authored by COSIC’s Wouter Castryck & Thomas Decru (presenter).
Read it here: eprint.iacr.org/2025/372
#ISOCRYPT #ISOCRYPTproject
#ISOCRYPT #ISOCRYPTproject
(from @jonathan.isogeny.club's talk at ARCTICCRYPT 2025!)


(from @jonathan.isogeny.club's talk at ARCTICCRYPT 2025!)
github.com/martisak/vsc...
Simply directly searches dblp from VS Code and copy-pastes the bib-entry into the bib file

github.com/martisak/vsc...
Simply directly searches dblp from VS Code and copy-pastes the bib-entry into the bib file
@craiggidney.bsky.social 's new paper: arxiv.org/abs/2505.15917.
A startling jump (20x) in how easy quantum factoring can be!
Also: much improved web design!
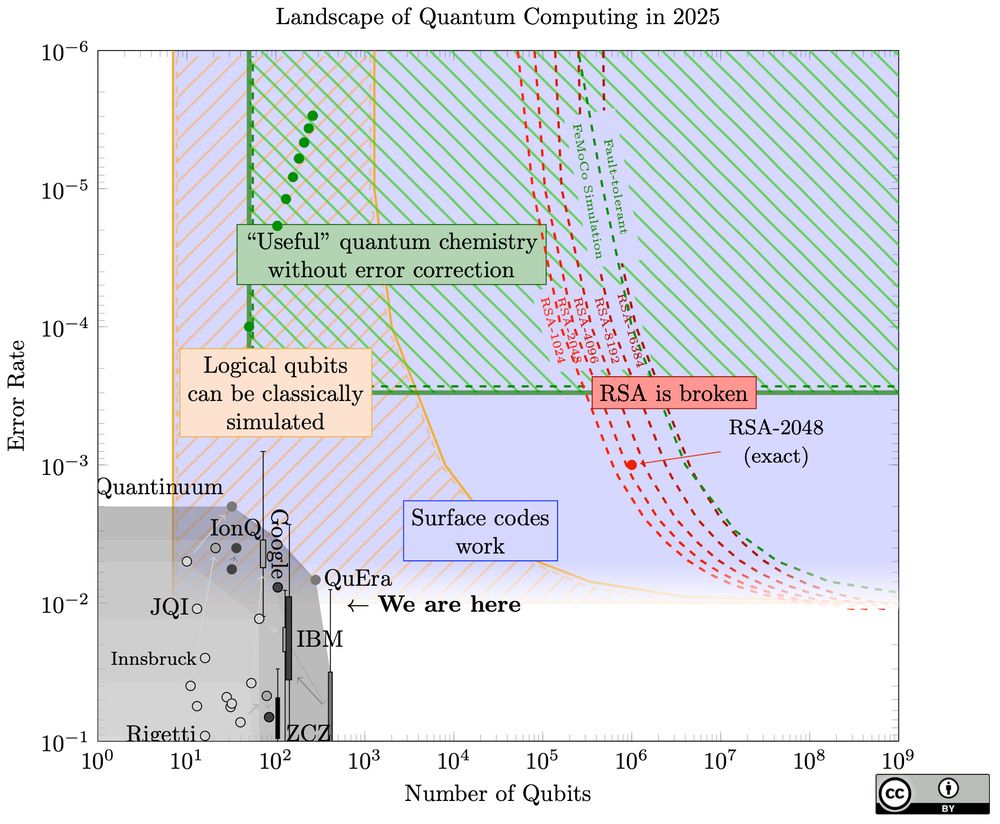
@craiggidney.bsky.social 's new paper: arxiv.org/abs/2505.15917.
A startling jump (20x) in how easy quantum factoring can be!
Also: much improved web design!




📅 10–12 Sept 2025 @ KU Leuven
Morning: research talks
Afternoon: brainstorming sessions
More info: www.esat.kuleuven.be/cosic/projec...
#isogeny #isocrypt #erc #postquantum

![Abstract. In this paper we study supersingular elliptic curves primitively oriented by an imaginary quadratic order, where the orientation is determined by an endomorphism that factors through the Frobenius isogeny. In this way, we partly recycle one of the main features of CSIDH, namely the fact that the Frobenius orientation can be represented for free. This leads to the most efficient family of ideal-class group actions in a range where the discriminant is significantly larger than the field characteristic p. Moreover, if we orient with a non-maximal order $\mathcal{O} \subset \mathbb{Q}(\sqrt{-p})$ and we assume that it is feasible to compute the ideal-class group of the maximal order, then also the ideal-class group of 𝒪 is known and we recover the central feature of SCALLOP-like constructions.
We propose two variants of our scheme. In the first one, the orientation is by a suborder of the form $\mathbb{Z}[f\sqrt{-p}]$ for some f coprime to p, so this is similar to SCALLOP. In the second one, inspired by the work of Chenu and Smith, the orientation is by an order of the form $\mathbb{Z}[\sqrt{-dp}]$ where d is square-free and not a multiple of p. We give practical ways of generating parameters, together with a proof-of-concept SageMath implementation of both variants, which shows the effectiveness of our construction.](https://cdn.bsky.app/img/feed_thumbnail/plain/did:plc:fwa55bujvdrwlwlwgqmmxmuf/bafkreibqnnsbrycfnj6lxmqemiovkeexw3n3kfjoj7vw2oybinwvn4xeym@jpeg)

The course will be both in-person and online: if you're interested, you can tune in Monday morning at 10:30 at unitn.zoom.us/j/88902079708
(details and full schedule in the image below)

Very happy to share that I successfully defended my thesis "Isogenies & Isometries" yesterday! A thrilling experience, would recommend, 10/10

Very happy to share that I successfully defended my thesis "Isogenies & Isometries" yesterday! A thrilling experience, would recommend, 10/10
We prepared an exciting program for you with a balanced mix of talks, coding sprints, skillshares and other activities!
www.cig.udl.cat/SQIparty2025...
See you in Lleida!
Join us for a 3-day workshop on isogeny-based cryptography in Lleida, Catalonia, April 28-30
www.cig.udl.cat/icrypto2025_...
Brought to you by ULleida's Cryptography+Graphs group, the SQIsign team and friends!
Registration and program coming soon
Registration is free!

We prepared an exciting program for you with a balanced mix of talks, coding sprints, skillshares and other activities!
www.cig.udl.cat/SQIparty2025...
See you in Lleida!


Curious about the mystery guest? Well, what are you waiting for, sign up and find out next weekend!

Curious about the mystery guest? Well, what are you waiting for, sign up and find out next weekend!

