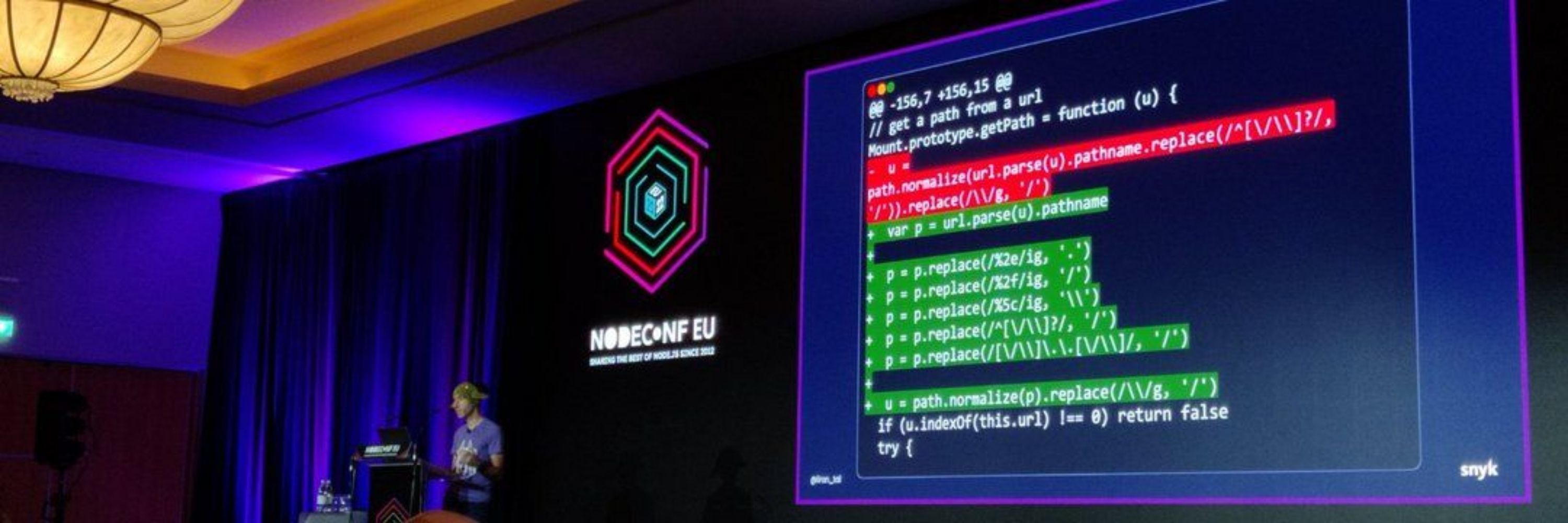
🌟 @GitHub Star
🏅 @OpenJS Pathfinder award for Security
🥑 DevRel at @snyksec
not just locally developed, but also commit and pushed it ;-)

not just locally developed, but also commit and pushed it ;-)
if you're churning out code strictly on terminal agents then willing to bet you're not reviewing all of it

if you're churning out code strictly on terminal agents then willing to bet you're not reviewing all of it

new lockfile-lint released with ESM config file support. get the next major version of the CLI if you want that Node.js module compatibility.

new lockfile-lint released with ESM config file support. get the next major version of the CLI if you want that Node.js module compatibility.
feels like I'm running my tests suite on the USS enterprise hah

feels like I'm running my tests suite on the USS enterprise hah
- העלות היא חצי שקלים חדשים
- העלות האלטרנטיבית היא בערך חצי שעה
הפעולה היא ווידוא ששינוי קוד (שהאייג׳נט ביצע מלכתחילה, אחד אחר) עובדים כמו שצריך ולא שוברים שום דבר

- העלות היא חצי שקלים חדשים
- העלות האלטרנטיבית היא בערך חצי שעה
הפעולה היא ווידוא ששינוי קוד (שהאייג׳נט ביצע מלכתחילה, אחד אחר) עובדים כמו שצריך ולא שוברים שום דבר



screenshot courtesy of Literat

screenshot courtesy of Literat

Uses the `railil` CLI to search Israel train station from-to schedule. Go give your lobster a new skill.

Uses the `railil` CLI to search Israel train station from-to schedule. Go give your lobster a new skill.
On February 11, Snyk is unveiling the latest innovations that empower builders to securely embrace AI-driven development - come tune in ;-)
📈 Strengthen your team’s foundation of DevSecOps for the age of AI development
🛠️ Develop guardrails to secure generative AI from the first p

On February 11, Snyk is unveiling the latest innovations that empower builders to securely embrace AI-driven development - come tune in ;-)
📈 Strengthen your team’s foundation of DevSecOps for the age of AI development
🛠️ Develop guardrails to secure generative AI from the first p






O, T, T, F, F, S, S, E, ?
O, T, T, F, F, S, S, E, ?
Looks nice?

Looks nice?
I got years of experience buddy. let me show you the way

I got years of experience buddy. let me show you the way




