One of the most critical elements of a strategy is a roadmap that lays out how to achieve that business vision. In today’s world of constant change, that roadmap must be agile so that it can be adapted and changed as you learn.
🧵

One of the most critical elements of a strategy is a roadmap that lays out how to achieve that business vision. In today’s world of constant change, that roadmap must be agile so that it can be adapted and changed as you learn.
🧵
Policies should be designed to set a productive and helpful level of “security friction” in business and technology processes.
🧵

Policies should be designed to set a productive and helpful level of “security friction” in business and technology processes.
🧵
🧵
🧵

Agile security is simply acknowledging that the real world is messy and unpredictable, and adapting to that. Zero Trust enables an agile approach to security.
🧵

Agile security is simply acknowledging that the real world is messy and unpredictable, and adapting to that. Zero Trust enables an agile approach to security.
🧵
🔷 If you reward technology teams to ignore cybersecurity, they will.
🔷 If you think security teams can magically stop criminals and spies while this is happening, you are fooling yourself.

🔷 If you reward technology teams to ignore cybersecurity, they will.
🔷 If you think security teams can magically stop criminals and spies while this is happening, you are fooling yourself.
From the Security Roles and Glossary standard Part 2 : Section 4.4
🔷 Download the Standard - publications.opengroup.org/s252
🔷 Read the Article - www.linkedin.com/pulse/securi...
🧵

From the Security Roles and Glossary standard Part 2 : Section 4.4
🔷 Download the Standard - publications.opengroup.org/s252
🔷 Read the Article - www.linkedin.com/pulse/securi...
🧵
A lot of people mistake manager or leadership jobs for "technical person in charge"
This slide is from a career talk I gave recently.

A lot of people mistake manager or leadership jobs for "technical person in charge"
This slide is from a career talk I gave recently.
Regardless of the size of your Zero Trust efforts, you should always rigorously and intensely prioritize your effort, ensuring you are continually focused on driving quick wins and incremental progress.

Regardless of the size of your Zero Trust efforts, you should always rigorously and intensely prioritize your effort, ensuring you are continually focused on driving quick wins and incremental progress.
For guidance on how to secure privileged access, see aka.ms/SPA

For guidance on how to secure privileged access, see aka.ms/SPA
(short 🧵 with download link for an open standard at the end)

(short 🧵 with download link for an open standard at the end)
This includes slides from two sessions:
◼️ Security and Zero Trust Body of Knowledge Introduction and Overview
◼️ Security Roles and Glossary Standard Overview and Vision
www.slideshare.net/slideshow/se...
🧵
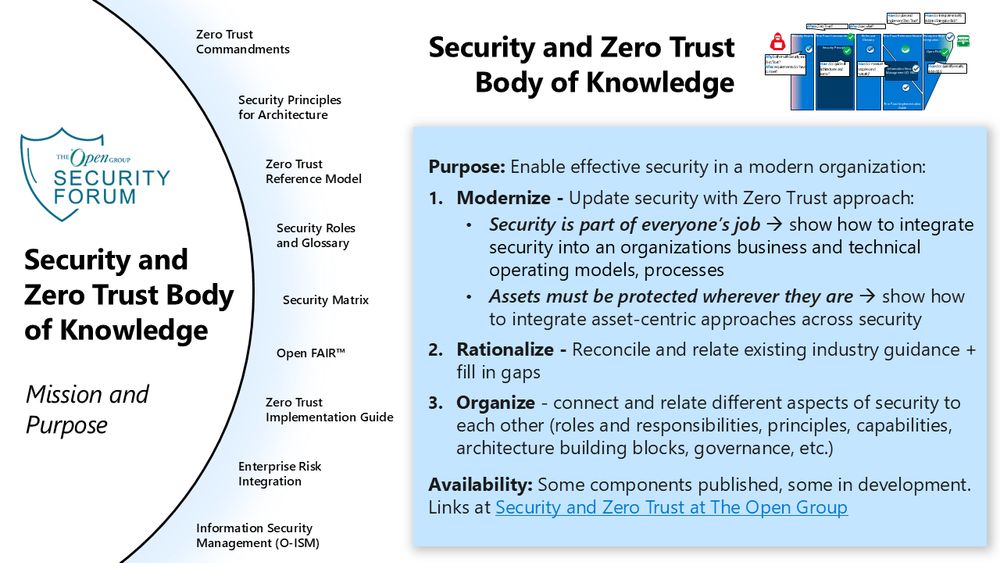
This includes slides from two sessions:
◼️ Security and Zero Trust Body of Knowledge Introduction and Overview
◼️ Security Roles and Glossary Standard Overview and Vision
www.slideshare.net/slideshow/se...
🧵
The greatest obstacle to security success is assuming and expecting that perfect security is possible (or worthwhile to pursue).
(1 of 2)

The greatest obstacle to security success is assuming and expecting that perfect security is possible (or worthwhile to pursue).
(1 of 2)
Worried the problems will come back as soon as you stop investing in security?
You're probably right...
a 🧵

Worried the problems will come back as soon as you stop investing in security?
You're probably right...
a 🧵
If you think security teams can magically stop criminals and spies while this is happening, you are fooling yourself.

If you think security teams can magically stop criminals and spies while this is happening, you are fooling yourself.
🔷 If you reward business leaders to ignore cybersecurity, they will.
... a 🧵

🔷 If you reward business leaders to ignore cybersecurity, they will.
... a 🧵
(and yes, there are animations and morph transitions in the downloadable slides - aka.ms/mcra)
🧵

(and yes, there are animations and morph transitions in the downloadable slides - aka.ms/mcra)
🧵
That's what often happens when you don't logs for security:
a 🧵

That's what often happens when you don't logs for security:
a 🧵
Cybersecurity professionals are currently and always will be set up to fail (and blamed for those failures) UNLESS security accountability and responsibility are correctly assigned across business, technology, and security roles
a 🧵

Cybersecurity professionals are currently and always will be set up to fail (and blamed for those failures) UNLESS security accountability and responsibility are correctly assigned across business, technology, and security roles
a 🧵
How to become a trusted advisor instead of being sent to the kids table & ignored while waiting to be blamed/fired at the next incident?
a 🧵

How to become a trusted advisor instead of being sent to the kids table & ignored while waiting to be blamed/fired at the next incident?
a 🧵
a short 🧵

a short 🧵
Building and securing AI Agents is fundamentally different - they are the programs/applications/apps of the AI platform, but managing risk from them is fundamentally different than previous apps because they come with so much functionality.

Building and securing AI Agents is fundamentally different - they are the programs/applications/apps of the AI platform, but managing risk from them is fundamentally different than previous apps because they come with so much functionality.
Check out the Security Roles and Glossary Standard we just published.
www.linkedin.com/pulse/securi...

Check out the Security Roles and Glossary Standard we just published.
www.linkedin.com/pulse/securi...


