
https://martinsohn.dk
Explore talks, topics, & speakers across the Tradecraft, OpenGraph, & new Practice Track, focused on turning Attack Path Management into an operational discipline.
Check out the agenda & plan your experience: ghst.ly/socon26-tw
🧵: 1/4
Explore talks, topics, & speakers across the Tradecraft, OpenGraph, & new Practice Track, focused on turning Attack Path Management into an operational discipline.
Check out the agenda & plan your experience: ghst.ly/socon26-tw
🧵: 1/4
This is how we rapidly developed a customer specific attack primitive for BloodHound that we call "ManagerOf" 👇
Today is a demo of how BloodHound's #OpenGraph helped a customer build ManagerOfHound.ps1 - going from attack path concept to a custom "ManagerOf" edge in BloodHound. Can it fit in a thread? Let's see...
🧵 1/6

This is how we rapidly developed a customer specific attack primitive for BloodHound that we call "ManagerOf" 👇
First dives into how we're improving the way BloodHound models attack paths through AD trusts: specterops.io/blog/2025/06...
Second covers an attack technique I came across while exploring AD trust abuse: specterops.io/blog/2025/06...
Hope you enjoy the read 🥳
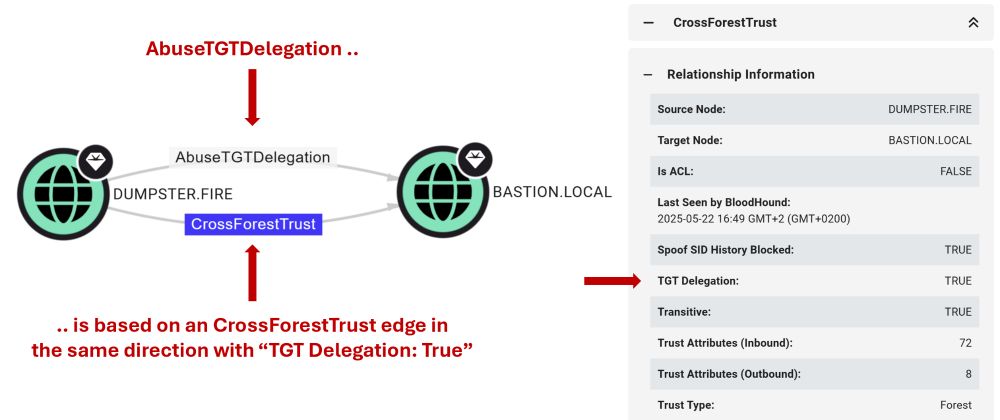
First dives into how we're improving the way BloodHound models attack paths through AD trusts: specterops.io/blog/2025/06...
Second covers an attack technique I came across while exploring AD trust abuse: specterops.io/blog/2025/06...
Hope you enjoy the read 🥳
Released with ~90 new Cypher queries, go check them out!
@joeydreijer.bsky.social and I spent many hours creating it and we hope you find it useful. All feedback is appreciated :)
Released with ~90 new Cypher queries, go check them out!
@joeydreijer.bsky.social and I spent many hours creating it and we hope you find it useful. All feedback is appreciated :)
Often helpdesk has GenericAll, misconfig'ed to apply on the OU itself, instead of only inheriting to principals within.
This week's 🔥 topic from @martinsohn.dk: the Microsoft-wont-fix-yet "BadSuccessor" attack that abuses Server 2025's dMSA feature for domain takeover.
This 🧵 shows how you can use BloodHound to find BadSuccessor risk.
(1/9)
Often helpdesk has GenericAll, misconfig'ed to apply on the OU itself, instead of only inheriting to principals within.
They combine 𝗰𝗼𝗲𝗿𝗰𝗶𝗼𝗻 and 𝗿𝗲𝗹𝗮𝘆𝗶𝗻𝗴, allowing Auth. Users to compromise computers. Read this excellent post by Elad Shamir if you are unfamiliar with those terms or want to know how to mitigate.
Relay attacks are more complicated than many people realize. Check out this deep dive from Elad Shamir on NTLM relay attacks & the new edges we recently added to BloodHound. ghst.ly/4lv3E31

They combine 𝗰𝗼𝗲𝗿𝗰𝗶𝗼𝗻 and 𝗿𝗲𝗹𝗮𝘆𝗶𝗻𝗴, allowing Auth. Users to compromise computers. Read this excellent post by Elad Shamir if you are unfamiliar with those terms or want to know how to mitigate.
I'm grateful I get to meet all you awesome people; community members and Specters. Huge thanks to the many speakers and trainers 💙
See you next year!




I'm grateful I get to meet all you awesome people; community members and Specters. Huge thanks to the many speakers and trainers 💙
See you next year!
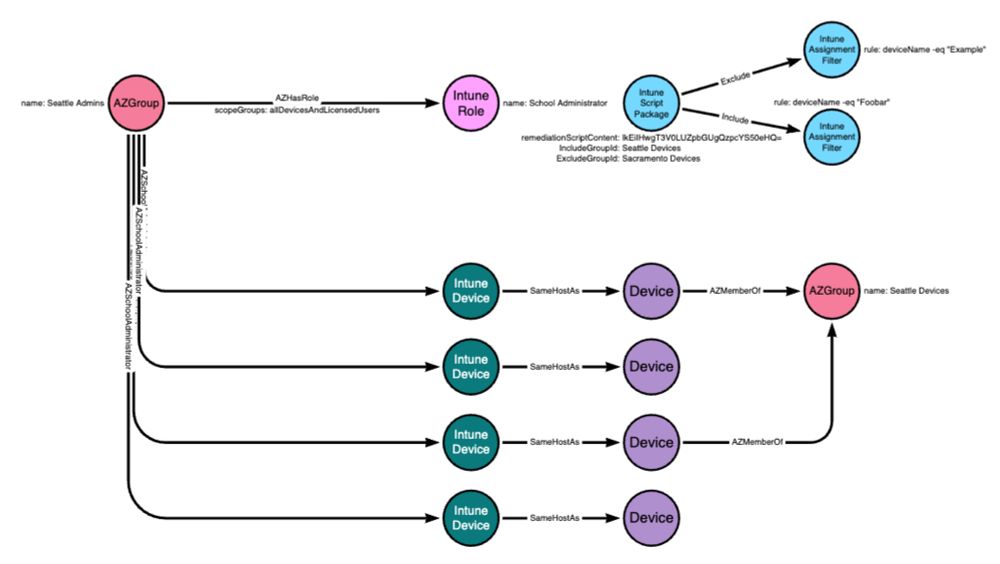
Check out the blog post from @bouj33boy.bsky.social to learn more. ghst.ly/3VJ5y4F

Check out the blog post from @bouj33boy.bsky.social to learn more. ghst.ly/3VJ5y4F

A Kerberos relay & forwarder for MiTM attacks!
>Relays Kerberos AP-REQ tickets
>Manages multiple SMB consoles
>Works on Win& Linux with .NET 8.0
>...
GitHub: github.com/decoder-it/K...

A Kerberos relay & forwarder for MiTM attacks!
>Relays Kerberos AP-REQ tickets
>Manages multiple SMB consoles
>Works on Win& Linux with .NET 8.0
>...
GitHub: github.com/decoder-it/K...
Outputs data in ldapsearch format that can be converted to BH JSON with BOFHound.
blog.fndsec.net/2024/11/25/s...

Outputs data in ldapsearch format that can be converted to BH JSON with BOFHound.
blog.fndsec.net/2024/11/25/s...


www.netspi.com/blog/technic...

www.netspi.com/blog/technic...
specterops.io/so-con/

specterops.io/so-con/

- MS Exchange On-Premises
- ADCS
- Insights from isolating Tier Zero with BloodHound Enterprise customers
Watch live or register for on-demand at ghst.ly/4eSssxL

- MS Exchange On-Premises
- ADCS
- Insights from isolating Tier Zero with BloodHound Enterprise customers
Watch live or register for on-demand at ghst.ly/4eSssxL



