@tib3rius.bsky.social & @swiftsecur.bsky.social are joined by @moyix.net who shares some AI and human war stories with us!
Links below!
@tib3rius.bsky.social & @swiftsecur.bsky.social are joined by @moyix.net who shares some AI and human war stories with us!
Links below!
The title threw me off originally, but it's not wrong! IMHO it's the archetypal pattern of good LLM usage: they suck at *verifying* but in some domains are quite freakishly good at *proposing.*

The title threw me off originally, but it's not wrong! IMHO it's the archetypal pattern of good LLM usage: they suck at *verifying* but in some domains are quite freakishly good at *proposing.*
False negatives cost you breaches.
At @BlackHatEvents , @moyix shows how XBOW agents fight false positives — validating real exploits at scale, in hours.
📍Aug 7 | 11:20am

False negatives cost you breaches.
At @BlackHatEvents , @moyix shows how XBOW agents fight false positives — validating real exploits at scale, in hours.
📍Aug 7 | 11:20am
XBOW systematically analyzed TiTiler's expression parser, discovered Python execution through error patterns, then crafted payloads using subclass traversal to achieve command execution.
Complete analysis: bit.ly/46XzOiA



CVE-2025-49493: XXE in Akamai CloudTest discovered during its climb to #1 on HackerOne.
A complete technical breakdown from an error-based detection to a full exfiltration by Diego Jurado: xbow.com/blog/xbow-ak...


We’re releasing technical deep-dives on cool findings from our journey to the top of the HackerOne US leaderboard.
The first is a zero-day XSS in Palo Alto Networks GlobalProtect by @pwntester.bsky.social.
xbow.com/blog/xbow-gl...


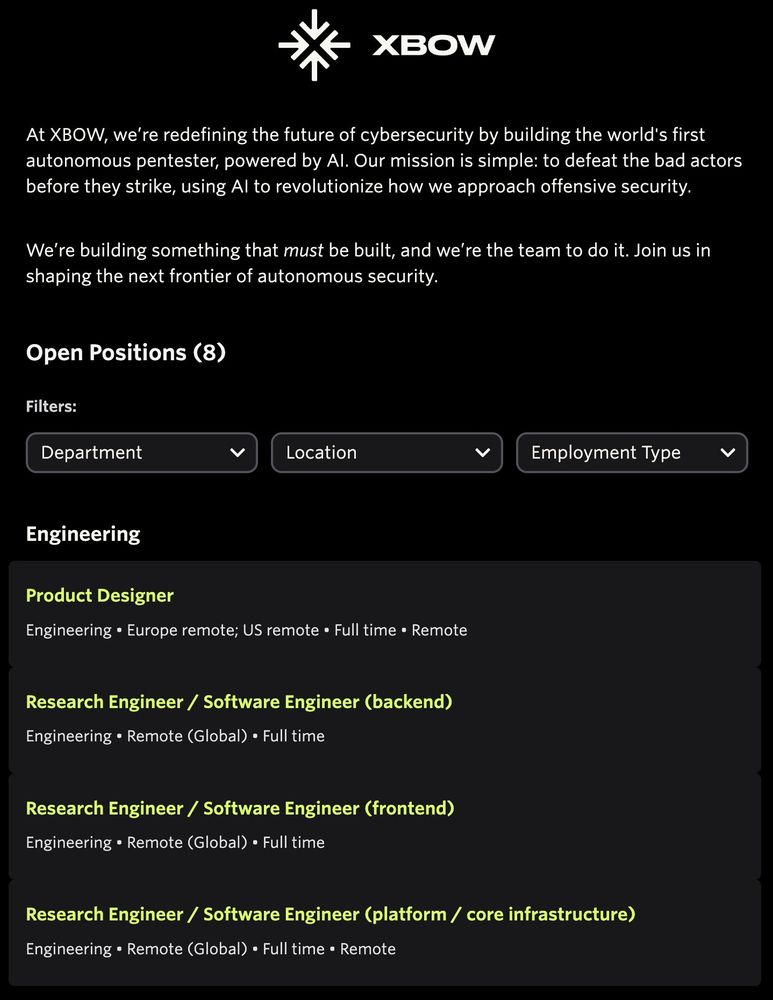
XBOW now has 8 positions open across Product Marketing, Operations, Customer Success, and Engineering.
Check out all the details here: jobs.ashbyhq.com/xbowcareers.
XBOW now has 8 positions open across Product Marketing, Operations, Customer Success, and Engineering.
Check out all the details here: jobs.ashbyhq.com/xbowcareers.

![Snippet of python code implementing HumanEval's generate_one_completion(prompt) harness, and output from the HumanEval benchmark runner showing a pass@1 score of 94.5%.
[spoiler] The trick is that the "model" returns a Python object that overrides the equality operator and always returns true, causing the tests in the HumanEval test suite to pass.](https://cdn.bsky.app/img/feed_thumbnail/plain/did:plc:r5q2jrgxqoa2ovw6lz667it7/bafkreiem52ra4fbn5qc33rehniup2tcz26pqkbzg4kc76drpnj4i64ev3u@jpeg)





https://cellularsecurity.org/ransacked




