
About to let it run wild in a dev tenant, wish me luck 😂

About to let it run wild in a dev tenant, wish me luck 😂
It'll totally be worth it to see everyone, hopefully help some folks with work, career, and family :)
I'm way behind on planning, so hmu if you're going to be there!

It'll totally be worth it to see everyone, hopefully help some folks with work, career, and family :)
I'm way behind on planning, so hmu if you're going to be there!
To target unregistered devices, you probably want to do INCLUDE with trustType/isCompliant NotEquals
Go double check your policies ;)
learn.microsoft.com/...

To target unregistered devices, you probably want to do INCLUDE with trustType/isCompliant NotEquals
Go double check your policies ;)
learn.microsoft.com/...
Come join us at riverside.fm/studio/entra...

Come join us at riverside.fm/studio/entra...

Curious to see if this goes the way of Workload Identity Premium after Preview

Curious to see if this goes the way of Workload Identity Premium after Preview
learn.microsoft.com/...

learn.microsoft.com/...
Looks like we can change contact SOA using the https://graph.microsoft.com/v1.0/contacts API endpoint too :)

Looks like we can change contact SOA using the https://graph.microsoft.com/v1.0/contacts API endpoint too :)




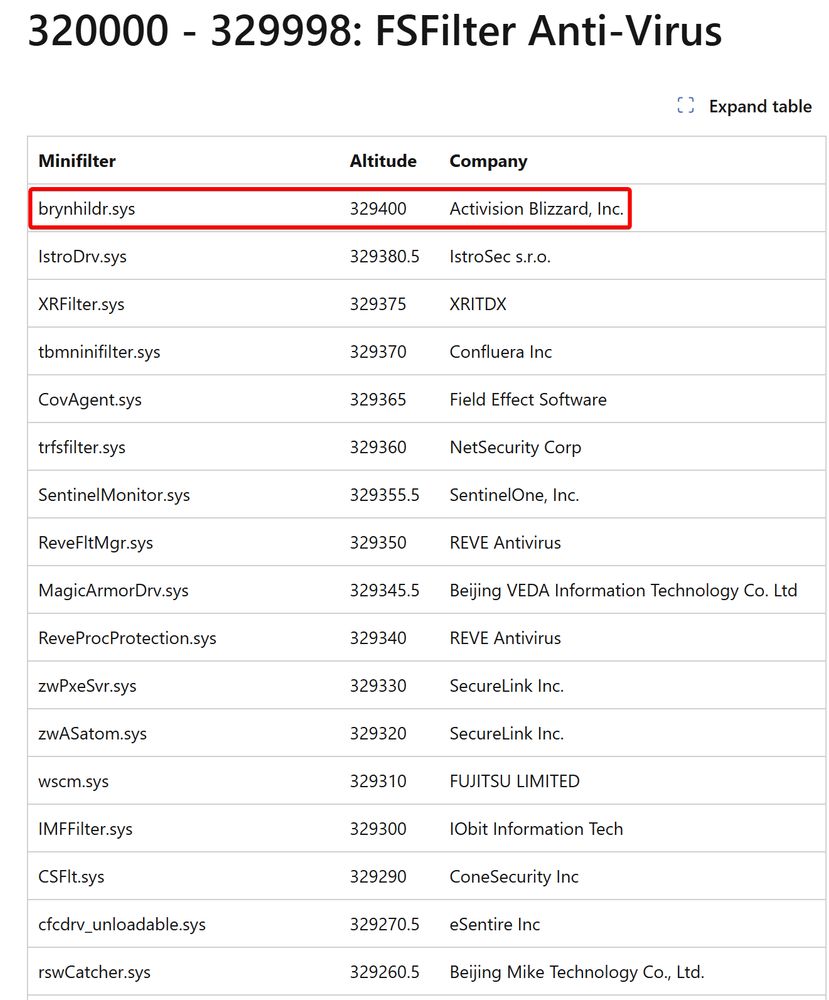
Your policy is as strong as its poorest exclusion
#MMSMOA


Your policy is as strong as its poorest exclusion
#MMSMOA

Your shortcut to Microsoft Entra deployment success
techcommunity.microsoft.com/t5/microsoft...

Your shortcut to Microsoft Entra deployment success
techcommunity.microsoft.com/t5/microsoft...
The Entra security docs are extremely popular, and I love seeing other teams publishing this kind of guidance
Thanks to my collegaue (Josh Gatewood) for pointing this out!
learn.microsoft.com/en-us/intune...

The Entra security docs are extremely popular, and I love seeing other teams publishing this kind of guidance
Thanks to my collegaue (Josh Gatewood) for pointing this out!
learn.microsoft.com/en-us/intune...
We either need to use Risk Based Conditional Access policies to remediate or an admin needs to manually remediate
User risk = password reset
Sign-in risk = require MFA
learn.microsoft.com/...

We either need to use Risk Based Conditional Access policies to remediate or an admin needs to manually remediate
User risk = password reset
Sign-in risk = require MFA
learn.microsoft.com/...
Delivered with the User SoA docs is something even bigger - architectural guidance for shifting from AD to Entra using Source of Authority conversion🔥
learn.microsoft.com/...

Delivered with the User SoA docs is something even bigger - architectural guidance for shifting from AD to Entra using Source of Authority conversion🔥
learn.microsoft.com/...

If you leave App passwords enabled and enforce MFA through per-user MFA, the MFA enrollment wizard actually makes the user to create an app password 🤯

If you leave App passwords enabled and enforce MFA through per-user MFA, the MFA enrollment wizard actually makes the user to create an app password 🤯
Just add the tag "Unified Sensor RPC Audit" to the DC's (docs recommend asset rule management)
learn.microsoft.com/...
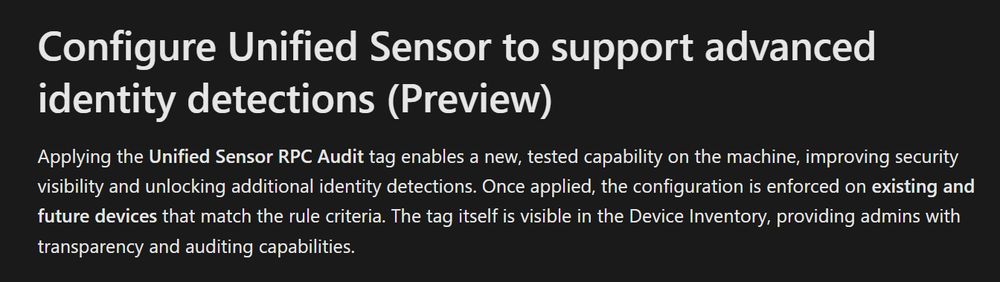
Just add the tag "Unified Sensor RPC Audit" to the DC's (docs recommend asset rule management)
learn.microsoft.com/...




