
https://cspbypass.com has a compiled list of ways to bypass the Content-Security Policy. Check out the video below 👇
https://cspbypass.com has a compiled list of ways to bypass the Content-Security Policy. Check out the video below 👇
www.amazon.com/dp/B0BRD9B3GS

www.amazon.com/dp/B0BRD9B3GS
"Be politely paranoid." 👏
www.youtube.com/watch?v=xEdZ...

"Be politely paranoid." 👏
www.youtube.com/watch?v=xEdZ...
All the hard work and sleepless nights have paid off!
All the hard work and sleepless nights have paid off!

The main goal is to cover hosting fees etc. So if you want to support my work, I would highly appreciate it if you could become a sponsor.
github.com/sponsors/ren...
Thanks!

The main goal is to cover hosting fees etc. So if you want to support my work, I would highly appreciate it if you could become a sponsor.
github.com/sponsors/ren...
Thanks!
nvd.nist.gov/vuln/detail/...
nvd.nist.gov/vuln/detail/...
Link to vectors👇
portswigger.net/web-security...

Link to vectors👇
portswigger.net/web-security...
@0x999.net redirects the page to trigger onpageswap, hijacks the thrown error, and turns it into code. Inspired by @terjanq.me. Now available on the XSS cheat sheet.
Link to vector👇
portswigger.net/web-security...

@0x999.net redirects the page to trigger onpageswap, hijacks the thrown error, and turns it into code. Inspired by @terjanq.me. Now available on the XSS cheat sheet.
Link to vector👇
portswigger.net/web-security...
var s=document.createElement('style');s.innerHTML=decodeURIComponent(location.hash.slice(1));document.head.appendChild(s)
var s=document.createElement('style');s.innerHTML=decodeURIComponent(location.hash.slice(1));document.head.appendChild(s)
📺 Watch here: www.youtube.com/watch?v=qgB0...
🖥️ Follow along with the slides: 0-a.nl/nahamcon/
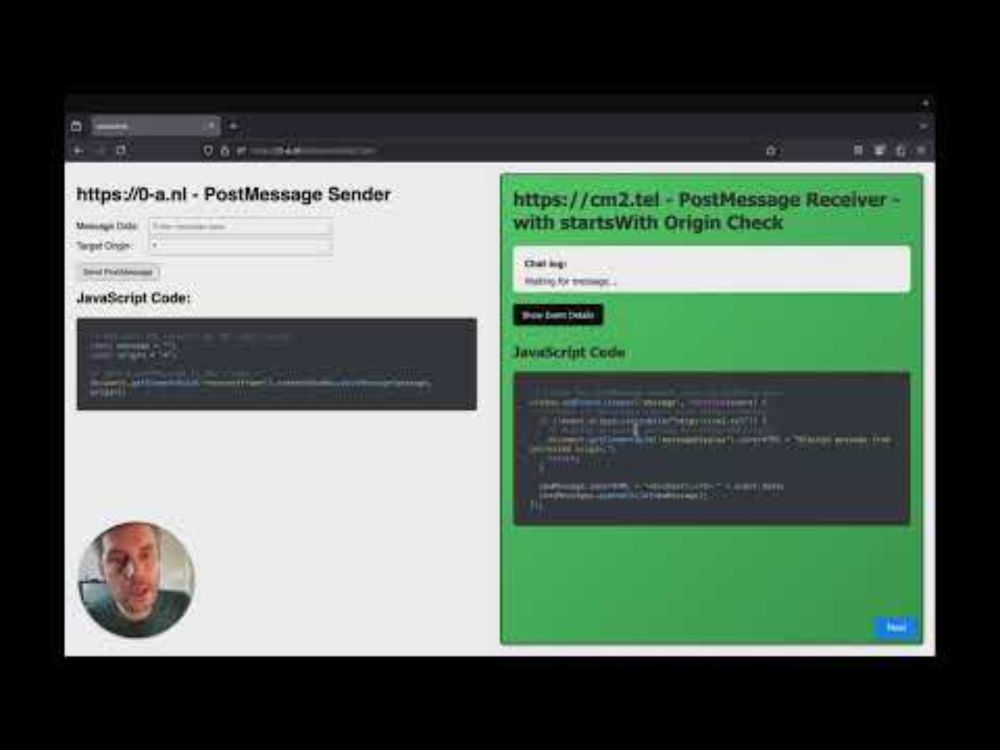
📺 Watch here: www.youtube.com/watch?v=qgB0...
🖥️ Follow along with the slides: 0-a.nl/nahamcon/

joaxcar.com/blog/2025/05...
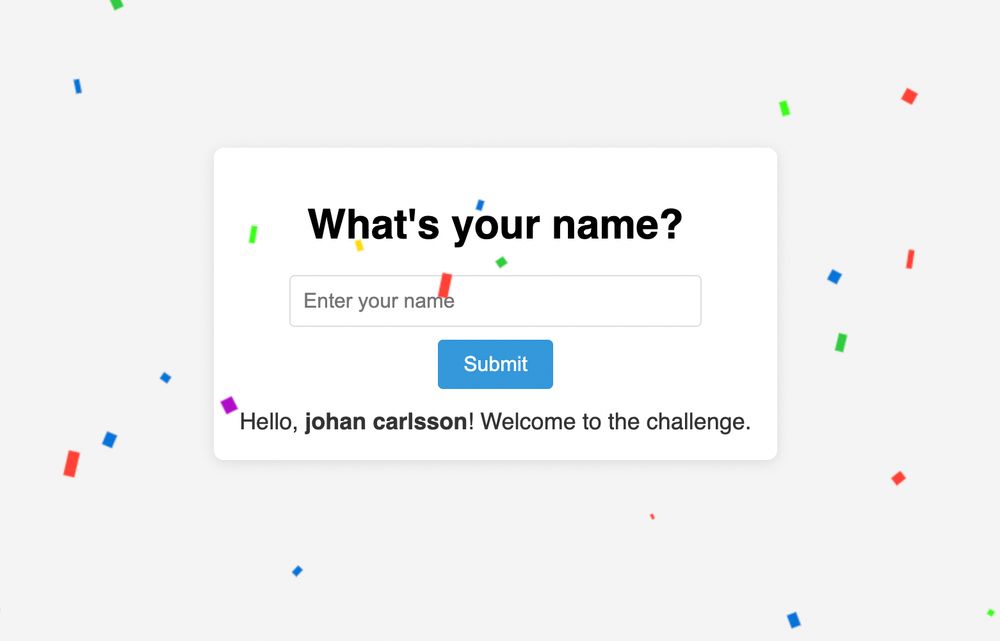
joaxcar.com/blog/2025/05...


