
Share all you know,
Abide by your handshake,
Have fun. - Dan Geer
github.com/leonjza/inet...
₁ seclists.org/oss-sec/2026...

github.com/leonjza/inet...
₁ seclists.org/oss-sec/2026...
#Cybersecurity #Infosec #INSO2026 #Cyberworkshops

github.com/sensepost/ob...

github.com/sensepost/ob...
sensepost.com/blog/2025/no...

sensepost.com/blog/2025/no...

sensepost.com/blog/2025/a-...
sensepost.com/blog/2025/a-...
👇
sensepost.com/blog/2025/no...
![A screenshot of the tool in action firing up an ssh session to another host.
./shellnot --daemon &
./shellnot --session 1 --input "ssh root@2.domain.com"
./shellnot --session 1 --output
ssh root@2.domain.com
root@2.domain.com”s password:
./shellnot --session 1 --input "toor"
./shellnot --session 1 --output
Last login: Sat May 24 16:45:40 2025 from 10.0.0.2
[root@localhost ~]$ ?
./shellnot --session 1 --input "id"
./shellnot --session 1 --output
id
uid=1001(root) gid=1001(root) groups=1001(root),970(docker),998(wheel)](https://cdn.bsky.app/img/feed_thumbnail/plain/did:plc:r6snvqf6fl4uuvenvgt54vsp/bafkreibl4bvg7qe4my3pebumqndaztoz2c3zcolhw7ajaps7erg3jlm2xi@jpeg)
👇
sensepost.com/blog/2025/no...
Reversing, exploits, disclosure pain - it has it all, and it's going to be fun! 💥
See ya soon Vegas. ☀️

Reversing, exploits, disclosure pain - it has it all, and it's going to be fun! 💥
See ya soon Vegas. ☀️

sensepost.com/blog/2025/in...
sensepost.com/blog/2025/in...
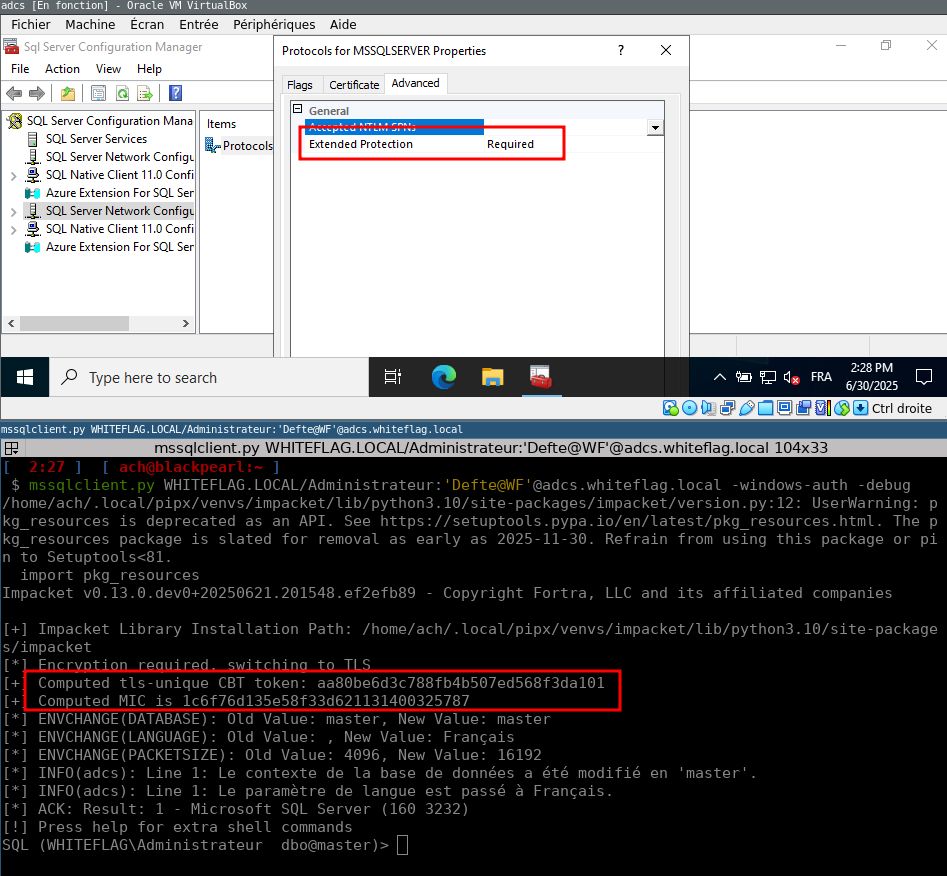
writeup: sensepost.com/blog/2025/is...
PR to impacket:
github.com/fortra/impac...
Demo: youtu.be/3mG2Ouu3Umk
writeup: sensepost.com/blog/2025/is...
PR to impacket:
github.com/fortra/impac...
Demo: youtu.be/3mG2Ouu3Umk
Here I have a cURL request, over an ICMP channel, funnelling HTTP requests in and out via our implant :D
Fun! 😄🔥



Here I have a cURL request, over an ICMP channel, funnelling HTTP requests in and out via our implant :D
Fun! 😄🔥
👉See the interview: www.france24.com/en/tv-shows/...
👉See the interview: www.france24.com/en/tv-shows/...
Demo: youtu.be/tIveWYfYcCI

Demo: youtu.be/tIveWYfYcCI
sensepost.com/blog/2025/le...
Tooling: github.com/Orange-Cyber...
Demo: youtu.be/OTaCV4-6qHE
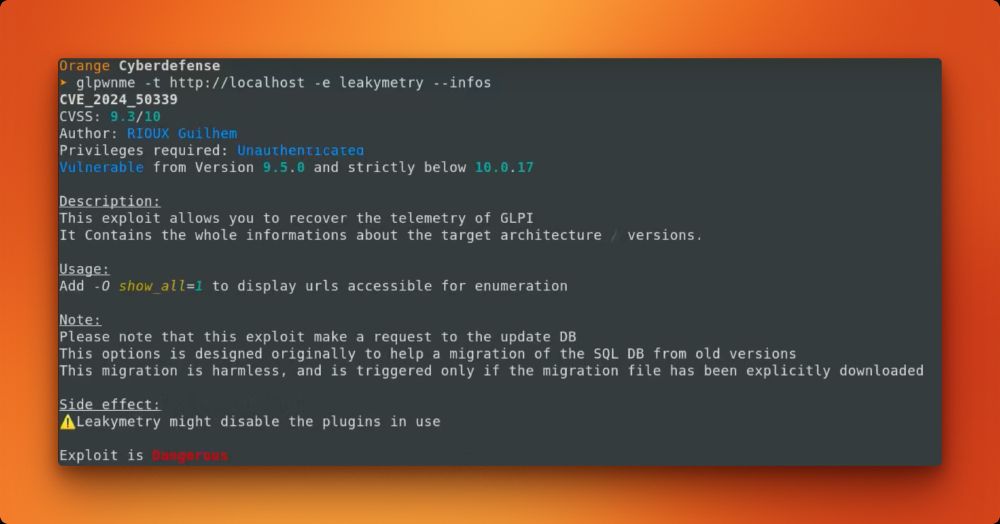
sensepost.com/blog/2025/le...
Tooling: github.com/Orange-Cyber...
Demo: youtu.be/OTaCV4-6qHE




Writeup: sensepost.com/blog/2025/ca...
Accompanying training/classifying tool capchan github.com/sensepost/ca...

Writeup: sensepost.com/blog/2025/ca...
Accompanying training/classifying tool capchan github.com/sensepost/ca...
(v3 of this skeet because there's no edit button and I need a proof reader)

(v3 of this skeet because there's no edit button and I need a proof reader)
github.com/sensepost/go...
sensepost.com/blog/2025/go...
github.com/sensepost/go...
sensepost.com/blog/2025/go...
sensepost.com/blog/2025/in...

sensepost.com/blog/2025/in...

