https://shadowserver.org/partner

We have introduced an ECS logging script for our intelligence reports. This script uses Redis to queue events for Logstash.
Check it out at github.com/The-Shadowse...
8001 unique IPs likely vulnerable on 2026-01-12 (18783 exposed). Note Exploit PoCs are public.
Tree Map: dashboard.shadowserver.org/statistics/c...
Raw IP data: www.shadowserver.org/what-we-do/n...

8001 unique IPs likely vulnerable on 2026-01-12 (18783 exposed). Note Exploit PoCs are public.
Tree Map: dashboard.shadowserver.org/statistics/c...
Raw IP data: www.shadowserver.org/what-we-do/n...
Scan results: dashboard.shadowserver.org/statistics/c...
Sinkhole results:
dashboard.shadowserver.org/statistics/c...


Scan results: dashboard.shadowserver.org/statistics/c...
Sinkhole results:
dashboard.shadowserver.org/statistics/c...
dashboard.shadowserver.org/statistics/c...
dashboard.shadowserver.org/statistics/c...


dashboard.shadowserver.org/statistics/c...
dashboard.shadowserver.org/statistics/c...
Dashboard Tree Map view: dashboard.shadowserver.org/statistics/c...
IP data in Vulnerable HTTP: www.shadowserver.org/what-we-do/n...


Dashboard Tree Map view: dashboard.shadowserver.org/statistics/c...
IP data in Vulnerable HTTP: www.shadowserver.org/what-we-do/n...
After 5 1/2 years since being published still over 10K Fortinet firewalls remain unpatched. Actively exploited as recently highlighted by Fortinet: www.fortinet.com/blog/psirt-b...


After 5 1/2 years since being published still over 10K Fortinet firewalls remain unpatched. Actively exploited as recently highlighted by Fortinet: www.fortinet.com/blog/psirt-b...

interpol.int/en/News-and-...
Undertaken as part of African Joint Operation against Cybercrime (AFJOC) project, funded by UK FCDO, & EU/Council of Europe GLACY-e project

interpol.int/en/News-and-...
Undertaken as part of African Joint Operation against Cybercrime (AFJOC) project, funded by UK FCDO, & EU/Council of Europe GLACY-e project
WatchGuard Advisory: www.watchguard.com/wgrd-psirt/a...

WatchGuard Advisory: www.watchguard.com/wgrd-psirt/a...


92M stolen data items from 567K victim IPs across 228 countries
Additional data shared by LE partners under Operation Endgame
Updated blog:
shadowserver.org/news/rhadama...
Check your reports!

92M stolen data items from 567K victim IPs across 228 countries
Additional data shared by LE partners under Operation Endgame
Updated blog:
shadowserver.org/news/rhadama...
Check your reports!
We have introduced an ECS logging script for our intelligence reports. This script uses Redis to queue events for Logstash.
Check it out at github.com/The-Shadowse...

We have introduced an ECS logging script for our intelligence reports. This script uses Redis to queue events for Logstash.
Check it out at github.com/The-Shadowse...
See: dashboard.shadowserver.org/statistics/c...
Check for compromise & patch!
Thank you to Validin & LeakIX for the collaboration!

See: dashboard.shadowserver.org/statistics/c...
Check for compromise & patch!
Thank you to Validin & LeakIX for the collaboration!
dashboard.shadowserver.org/statistics/h...

dashboard.shadowserver.org/statistics/h...
IP data is being shared in Vulnerable HTTP reports: www.shadowserver.org/what-we-do/n...
Dashboard geo breakdown: dashboard.shadowserver.org/statistics/c...
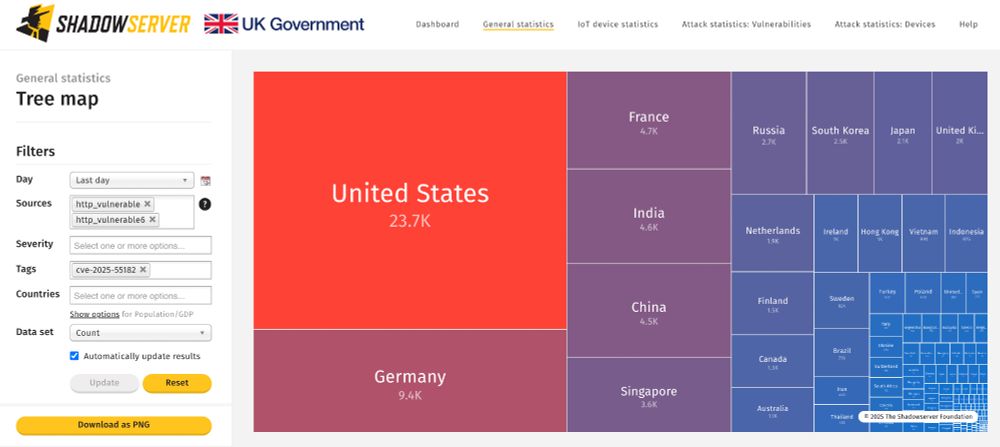
IP data is being shared in Vulnerable HTTP reports: www.shadowserver.org/what-we-do/n...
Dashboard geo breakdown: dashboard.shadowserver.org/statistics/c...
IP data is being shared in Vulnerable HTTP reports: www.shadowserver.org/what-we-do/n...
Dashboard geo breakdown: dashboard.shadowserver.org/statistics/c...

IP data is being shared in Vulnerable HTTP reports: www.shadowserver.org/what-we-do/n...
Dashboard geo breakdown: dashboard.shadowserver.org/statistics/c...
VulnCheck (vulncheck.com) continues to grow as we welcome them as a new Shadowserver Alliance Partner -Silver tier!
We look forward to enhancing our joint efforts to help network defenders globally with vulnerability management.

VulnCheck (vulncheck.com) continues to grow as we welcome them as a new Shadowserver Alliance Partner -Silver tier!
We look forward to enhancing our joint efforts to help network defenders globally with vulnerability management.
Data shared in a our Compromised Account Report www.shadowserver.org/what-we-do/n... (search for 2025-11-26 & compromised_account prefix)

Data shared in a our Compromised Account Report www.shadowserver.org/what-we-do/n... (search for 2025-11-26 & compromised_account prefix)

dashboard.shadowserver.org/statistics/c...

dashboard.shadowserver.org/statistics/c...
86M stolen data items from 525K victim IPs across 226 countries included in our new Rhadamanthys Historic Bot Victims Special Report, run overnight 2025-11-12
More details:
shadowserver.org/news/rhadama...

86M stolen data items from 525K victim IPs across 226 countries included in our new Rhadamanthys Historic Bot Victims Special Report, run overnight 2025-11-12
More details:
shadowserver.org/news/rhadama...
The Australian Signals Directorate (ASD) recently published an advisory on the BadCandy implant still present in many Cisco IOS XE devices: www.cyber.gov.au/about-us/vie...
We still see around 15 000 Cisco IOS XE devices with the implant
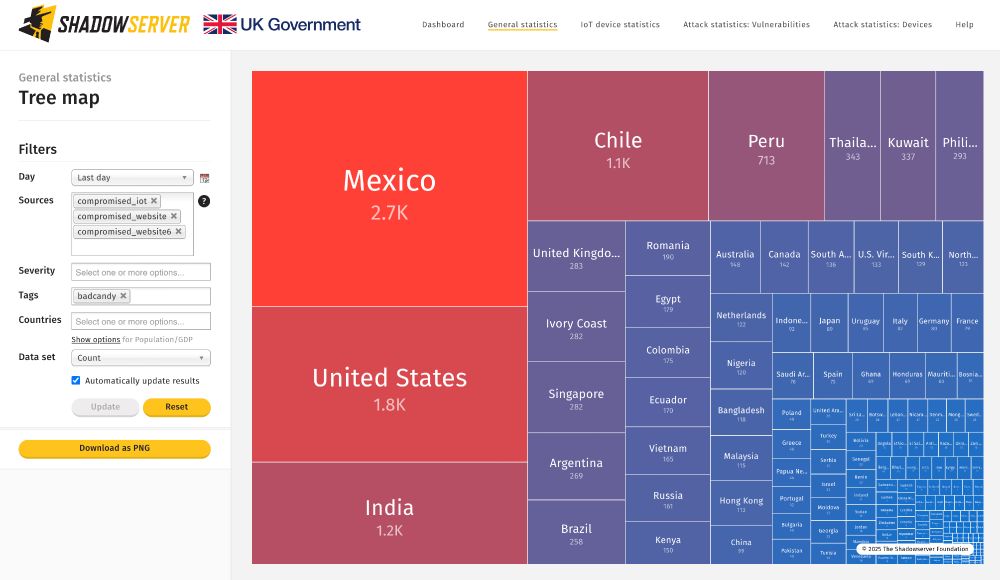
The Australian Signals Directorate (ASD) recently published an advisory on the BadCandy implant still present in many Cisco IOS XE devices: www.cyber.gov.au/about-us/vie...
We still see around 15 000 Cisco IOS XE devices with the implant
We found nearly 8898 unpatched DNS open resolvers on 2025-10-30, down to 6653 on 2025-11-01: dashboard.shadowserver.org/statistics/c...

We found nearly 8898 unpatched DNS open resolvers on 2025-10-30, down to 6653 on 2025-11-01: dashboard.shadowserver.org/statistics/c...

Top affected: US with 23.2K instances

Top affected: US with 23.2K instances

