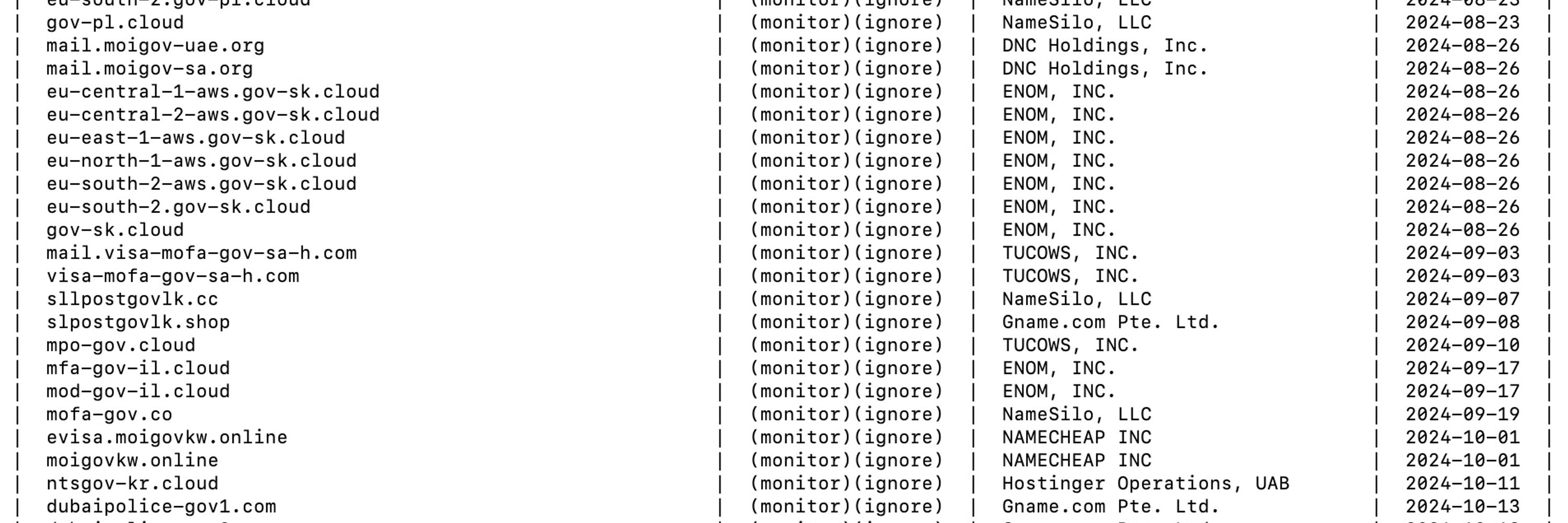
Download live malware samples mentioned here: https://github.com/StrikeReady-Inc/samples
If you prefer marketing (our product is great!) subscribe to our main page @strikeready.com
SCAN_BC_TH_1389.zip
SCAN_BC_TH_1389.zip


attd.z23.web.core[.]windows[.]net/ATTD-ASIA-2025.zip (live link, careful!)
ATTD-ASIA-2025.lnk a12357ff6c0f7b021f32b0c9cd3d01c4
ATTD-ASIA-2025.zip a8082a80cef9ccee9d7a35f5366e3afb
gzv.msi 32e7dcbd26b6455974d5b2c52c3ca421 🐴

attd.z23.web.core[.]windows[.]net/ATTD-ASIA-2025.zip (live link, careful!)
ATTD-ASIA-2025.lnk a12357ff6c0f7b021f32b0c9cd3d01c4
ATTD-ASIA-2025.zip a8082a80cef9ccee9d7a35f5366e3afb
gzv.msi 32e7dcbd26b6455974d5b2c52c3ca421 🐴
74e75830252220cbbe7e3adec4340d2d (sentinelone icon spoof) -> stratioai[.]org

74e75830252220cbbe7e3adec4340d2d (sentinelone icon spoof) -> stratioai[.]org
links to soigu.rar 1d286ce46904247d899b16bd82698a86 -> 50b94a39590f4e71dc0acdf642b52e31 -> sunmedical[.]st
links to soigu.rar 1d286ce46904247d899b16bd82698a86 -> 50b94a39590f4e71dc0acdf642b52e31 -> sunmedical[.]st
If you work in email security, any filter you write to detect targeted threats will eventually fire on this actor, plus one more (~supyra). They've emailed governments every single day for 15 years with pages and pages of this content, none of which is ever malicious

If you work in email security, any filter you write to detect targeted threats will eventually fire on this actor, plus one more (~supyra). They've emailed governments every single day for 15 years with pages and pages of this content, none of which is ever malicious
[email protected]
[email protected]
drive[.]google[.]com/file/d/14vgoZqBktuuhdhZSsaK5Py7Y2k1yqymh/view?usp=drive_link
CNSA-SUPARCO MoU.rar f4e0e18d86b06a30cddf61b56fdcf429

[email protected]
[email protected]
drive[.]google[.]com/file/d/14vgoZqBktuuhdhZSsaK5Py7Y2k1yqymh/view?usp=drive_link
CNSA-SUPARCO MoU.rar f4e0e18d86b06a30cddf61b56fdcf429
ПисьмоМВД.pdf.lnk (Letter from the Ministry of Internal Affairs.pdf.lnk)
00bd4de2bde0461accdd2e79279b08c2
-> document.pdf
->GameHook.exe
-> graphics-hook-filter64.dll
-> simhei.dat
00bd4de2bde0461accdd2e79279b08c2
8ee654d826ca5243e2ed1bc4d07f86be

ПисьмоМВД.pdf.lnk (Letter from the Ministry of Internal Affairs.pdf.lnk)
00bd4de2bde0461accdd2e79279b08c2
-> document.pdf
->GameHook.exe
-> graphics-hook-filter64.dll
-> simhei.dat
00bd4de2bde0461accdd2e79279b08c2
8ee654d826ca5243e2ed1bc4d07f86be
fliqr[.]codes/dl/cei8430kc2/Job-search-program.zip
-> תוכנית חיפוש עבודה.msi 7ebea1328b6fe3751dd0250452c466ce
fliqr[.]codes/dl/cei8430kc2/Job-search-program.zip
-> תוכנית חיפוש עבודה.msi 7ebea1328b6fe3751dd0250452c466ce


desktop-kspr25q
desktop-kspr25q
Запит на отримання інформації командира військової частини А0135_11-967_10.11.2025.HTA 2a04a7584d90cff161be936b0b3f43c0
Запит командира військової частини А0135.rar 5df7ff42d566156ce7c478f1a40896e3

Запит на отримання інформації командира військової частини А0135_11-967_10.11.2025.HTA 2a04a7584d90cff161be936b0b3f43c0
Запит командира військової частини А0135.rar 5df7ff42d566156ce7c478f1a40896e3
filesdownld.z13.web.core[.]windows[.]net/A9T3ZB7L1QX5.html
> twilight-voice-2c67.smith93011.workers[.]dev
>Chi Tiết Kế hoạch Chuyển đổi số và BADT. zip
filestoretome.z23.web.core[.]windows[.]net/filelocate.html > oumuenz[.]com >Details[.]zip

filesdownld.z13.web.core[.]windows[.]net/A9T3ZB7L1QX5.html
> twilight-voice-2c67.smith93011.workers[.]dev
>Chi Tiết Kế hoạch Chuyển đổi số và BADT. zip
filestoretome.z23.web.core[.]windows[.]net/filelocate.html > oumuenz[.]com >Details[.]zip
lnk + dll + exe in a zip? insta detection! 318456a2f2bf90d215cd14ee0314be0e8ae32796b18db49970297c64a3e916d4
lnk + dll + exe in a zip? insta detection! 318456a2f2bf90d215cd14ee0314be0e8ae32796b18db49970297c64a3e916d4


uses luajit with interesting comments, but llm derived regardless
uploaded from India
CBDT.pdf
crycert.dat
lua51.dll
PASSWORD.lnk
update.bin
update.exe

uses luajit with interesting comments, but llm derived regardless
uploaded from India
CBDT.pdf
crycert.dat
lua51.dll
PASSWORD.lnk
update.bin
update.exe




here's a recent gamaredon phish. cant stop wont stop ->
Повістка про виклик_357-16230-25_24.10.2025.pdf:.._.._.._.._.._.._AppData_Roaming_Microsoft_Windows_Start Menu_Programs_Startup_357-16230-25_24.10.2025.HTA
f2368a466c7a67ab3690736dd9d84f62

here's a recent gamaredon phish. cant stop wont stop ->
Повістка про виклик_357-16230-25_24.10.2025.pdf:.._.._.._.._.._.._AppData_Roaming_Microsoft_Windows_Start Menu_Programs_Startup_357-16230-25_24.10.2025.HTA
f2368a466c7a67ab3690736dd9d84f62



