
Listen as he shares the story behind his open-source tool, IoT Hunter, and explains how, through automation, it helps defenders cover hundreds of CVEs. brnw.ch/21wXDRr

Listen as he shares the story behind his open-source tool, IoT Hunter, and explains how, through automation, it helps defenders cover hundreds of CVEs. brnw.ch/21wXDRr
Rhadamanthys: brnw.ch/21wXsCc
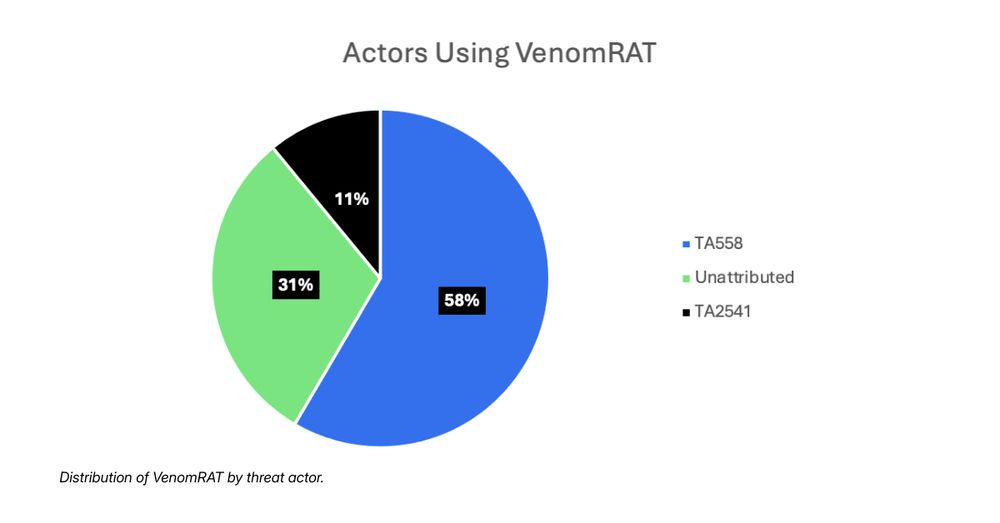
VenomRAT: brnw.ch/21wXsCd

Rhadamanthys: brnw.ch/21wXsCc
VenomRAT: brnw.ch/21wXsCd
@bloomberg.com spoke with our #ecrime experts who warned, "It is a full-scale supply chain threat."
Read the article: www.bloomberg.com/news/article....

@bloomberg.com spoke with our #ecrime experts who warned, "It is a full-scale supply chain threat."
Read the article: www.bloomberg.com/news/article....
Blog: www.proofpoint.com/us/blog/thre...

Blog: www.proofpoint.com/us/blog/thre...
Today, cargo theft is commonly conducted digitally by hacking the #supplychain to exploit gaps and steal #freight remotely.
🧵⤵️
Today, cargo theft is commonly conducted digitally by hacking the #supplychain to exploit gaps and steal #freight remotely.
🧵⤵️
We use this tool internally to help track multiple threat actors with high confidence.
We use this tool internally to help track multiple threat actors with high confidence.
Here, we detail our findings and security implications. ⤵️ brnw.ch/21wWOgL

Here, we detail our findings and security implications. ⤵️ brnw.ch/21wWOgL
Messages are sent from hundreds of compromised sender accounts impersonating ELSTER and contain malicious URLs.

Messages are sent from hundreds of compromised sender accounts impersonating ELSTER and contain malicious URLs.
The sophisticated cybercriminal, notably, appears to own its entire attack chain with multiple delivery techniques.
Learn about TA585 and one of its favored payloads, MonsterV2: brnw.ch/21wWAAU.

The sophisticated cybercriminal, notably, appears to own its entire attack chain with multiple delivery techniques.
Learn about TA585 and one of its favored payloads, MonsterV2: brnw.ch/21wWAAU.
Activity was observed from September 20-30th, affecting nearly half a million users in over 4,000 tenants.

Activity was observed from September 20-30th, affecting nearly half a million users in over 4,000 tenants.
Blog: www.proofpoint.com/us/blog/thre....

Blog: www.proofpoint.com/us/blog/thre....

On this episode of DISCARDED, you'll hear why legacy features like Direct Send are a prime target for cybercriminals.
Stream now on our website: brnw.ch/21wVja5

On this episode of DISCARDED, you'll hear why legacy features like Direct Send are a prime target for cybercriminals.
Stream now on our website: brnw.ch/21wVja5
Bookmark the show page and reserve your seat at the table 🪑 alongside Selena Larson, Dave Bittner and Keith Mularski.
🔥 You won't want to miss it! thecyberwire.com/podcasts/onl...
#podcast #hotones

Bookmark the show page and reserve your seat at the table 🪑 alongside Selena Larson, Dave Bittner and Keith Mularski.
🔥 You won't want to miss it! thecyberwire.com/podcasts/onl...
#podcast #hotones
We have observed threat actor campaigns leveraging the AI-generated website builder Lovable to create and host cred phishing, malware, and fraud websites.
Learn more in our blog: brnw.ch/21wV3Zo

We have observed threat actor campaigns leveraging the AI-generated website builder Lovable to create and host cred phishing, malware, and fraud websites.
Learn more in our blog: brnw.ch/21wV3Zo
We first spotted this post by ANY.RUN about ClickFix delivering Rhadamanthys and began investigating. infosec.exchange/@anyrun_app/...
We first spotted this post by ANY.RUN about ClickFix delivering Rhadamanthys and began investigating. infosec.exchange/@anyrun_app/...
#FIDO #MFA
All the details in our blog: brnw.ch/21wURuW.

#FIDO #MFA
All the details in our blog: brnw.ch/21wURuW.

On this DISCARDED episode, we discuss the chaotic brilliance of mid-tier eCrime actors, why shared commodity tooling can make attribution difficult, why TA582 is so interesting, and much more.
Stream here 👉 brnw.ch/21wUw3L

On this DISCARDED episode, we discuss the chaotic brilliance of mid-tier eCrime actors, why shared commodity tooling can make attribution difficult, why TA582 is so interesting, and much more.
Stream here 👉 brnw.ch/21wUw3L
Proofpoint found threat actors targeting job seekers to distribute remote management tools that can lead to data or financial theft, or potentially to install follow-on malware like ransomware.
Proofpoint found threat actors targeting job seekers to distribute remote management tools that can lead to data or financial theft, or potentially to install follow-on malware like ransomware.
Blog: brnw.ch/21wUkQ8
#shipment #RFQ #finance #scam

Blog: brnw.ch/21wUkQ8
#shipment #RFQ #finance #scam
At least 3️⃣ distinct China-aligned threat actors are behind the efforts. brnw.ch/21wUctY
At least 3️⃣ distinct China-aligned threat actors are behind the efforts. brnw.ch/21wUctY
Learn about an interesting phishing campaign involving the “unsubscribe” link often included in marketing emails. 🔍 ⤵️
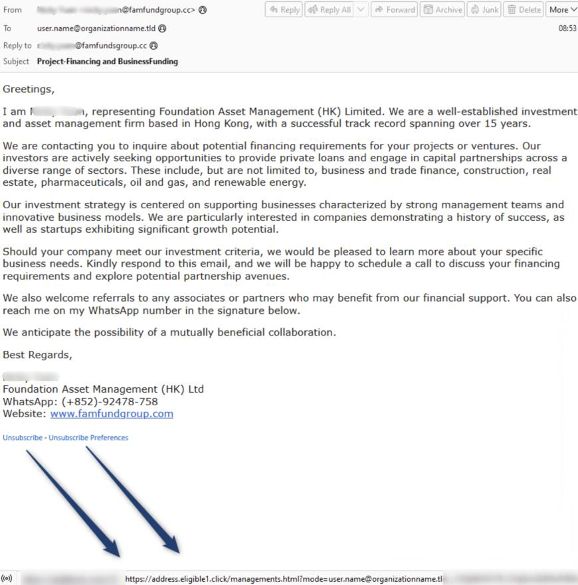
Learn about an interesting phishing campaign involving the “unsubscribe” link often included in marketing emails. 🔍 ⤵️
TA829 🤝 UNK_GreenSec
Proofpoint researchers published new insights on an intriguing overlap between 2 threat actor clusters—TA829 and UNK_GreenSec—in a campaign that blurs the lines between espionage and cybercriminal activity. brnw.ch/21wTN5x

TA829 🤝 UNK_GreenSec
Proofpoint researchers published new insights on an intriguing overlap between 2 threat actor clusters—TA829 and UNK_GreenSec—in a campaign that blurs the lines between espionage and cybercriminal activity. brnw.ch/21wTN5x
Read the blog: brnw.ch/21wTvpI.
#securityengineering #detectionengineering #securitycontrols

Read the blog: brnw.ch/21wTvpI.
#securityengineering #detectionengineering #securitycontrols

