TuxPanik
@tuxpanik.bsky.social
Head of CERT & PSIRT
#infosec #DFIR #malware #pentest #legal #CTI #MISP #OpenCTI #TheHive opinions are my own
#infosec #DFIR #malware #pentest #legal #CTI #MISP #OpenCTI #TheHive opinions are my own
🚀 I’m very proud to announce the release of "Suspicious", a framework developed by our team and now available as Open Source! 🎉
💼 Built by members of the @tha-cert.bsky.social , this platform enables employees to self-assess suspicious e-mails or files efficiently.
👉 Check it out: lnkd.in/ecQd-N_F
💼 Built by members of the @tha-cert.bsky.social , this platform enables employees to self-assess suspicious e-mails or files efficiently.
👉 Check it out: lnkd.in/ecQd-N_F
LinkedIn
This link will take you to a page that’s not on LinkedIn
lnkd.in
October 6, 2025 at 2:02 PM
🚀 I’m very proud to announce the release of "Suspicious", a framework developed by our team and now available as Open Source! 🎉
💼 Built by members of the @tha-cert.bsky.social , this platform enables employees to self-assess suspicious e-mails or files efficiently.
👉 Check it out: lnkd.in/ecQd-N_F
💼 Built by members of the @tha-cert.bsky.social , this platform enables employees to self-assess suspicious e-mails or files efficiently.
👉 Check it out: lnkd.in/ecQd-N_F
Reposted by TuxPanik
La France va devenir le premier actionnaire de l'opérateur européen de satellites Eutelsat

La France va devenir le premier actionnaire de l'opérateur européen de satellites Eutelsat
Eutelsat, concurrent de l'entreprise Starlink d'Elon Musk, va voir l'État français devenir son premier actionnaire à la faveur d'un réinvestissement de 717 millions d'euros dans le groupe européen, deuxième opérateur mondial de satellites en orbite basse.
f24.my
June 19, 2025 at 8:18 PM
La France va devenir le premier actionnaire de l'opérateur européen de satellites Eutelsat
Reposted by TuxPanik
⚡L’adoption de DMARC n’est pas assez généralisée, ce qui favorise les attaques de phishing

L’adoption de DMARC n’est pas assez généralisée, ce qui favorise les attaques de phishing - IT SOCIAL
Selon une nouvelle étude, plus de 90 % des principaux domaines de messagerie électronique dans le monde sont vulnérables à l’usurpation d’identité. Cette faille permet aux cybercriminels de lancer…
ino.to
June 13, 2025 at 11:09 AM
⚡L’adoption de DMARC n’est pas assez généralisée, ce qui favorise les attaques de phishing
Reposted by TuxPanik
💡 L'authentification à facteurs multiples (#MFA) n'est aujourd'hui plus une option.
Mais il faut aussi (ré)apprendre à fermer sa session, à se déconnecter d'un service Web après usage, avant de fermer la fenêtre ou l'onglet de son navigateur.
www.lemagit.fr/actualites/3...
Mais il faut aussi (ré)apprendre à fermer sa session, à se déconnecter d'un service Web après usage, avant de fermer la fenêtre ou l'onglet de son navigateur.
www.lemagit.fr/actualites/3...

Éducation nationale : Stormous semble avoir constitué une « combolist » | LeMagIT
Le groupe malveillant Stormous vient de revendiquer une cyberattaque contre les systèmes de l’éducation nationale. L’échantillon de données publié pour le moment suggère la création d’une liste…
www.lemagit.fr
June 12, 2025 at 10:28 AM
💡 L'authentification à facteurs multiples (#MFA) n'est aujourd'hui plus une option.
Mais il faut aussi (ré)apprendre à fermer sa session, à se déconnecter d'un service Web après usage, avant de fermer la fenêtre ou l'onglet de son navigateur.
www.lemagit.fr/actualites/3...
Mais il faut aussi (ré)apprendre à fermer sa session, à se déconnecter d'un service Web après usage, avant de fermer la fenêtre ou l'onglet de son navigateur.
www.lemagit.fr/actualites/3...
Reposted by TuxPanik
#VIGINUM publie avec les contributions de partenaires internationaux, un rapport sur African Initiative, une agence de presse russe, pensée comme l'un des principaux vecteurs de la réarticulation du dispositif d’influence de la Russie en Afrique post-Prigojine ➡️ www.sgdsn.gouv.fr/publications...

June 12, 2025 at 12:12 PM
#VIGINUM publie avec les contributions de partenaires internationaux, un rapport sur African Initiative, une agence de presse russe, pensée comme l'un des principaux vecteurs de la réarticulation du dispositif d’influence de la Russie en Afrique post-Prigojine ➡️ www.sgdsn.gouv.fr/publications...
Reposted by TuxPanik
Two rogue employees from IT company Opexus have stolen data and destroyed over 30 US government databases
www.insurancejournal.com/news/nationa...
www.insurancejournal.com/news/nationa...

Hack of Contractor Was at Root of Massive Federal Data Breach
A software company that handles sensitive data for nearly every US federal agency was the victim of a cyber breach earlier this year due to a "major
www.insurancejournal.com
May 22, 2025 at 12:31 PM
Two rogue employees from IT company Opexus have stolen data and destroyed over 30 US government databases
www.insurancejournal.com/news/nationa...
www.insurancejournal.com/news/nationa...
Reposted by TuxPanik
Cisco Talos says a group tracked as UAT-6382 has used a recent Trimble CityWorks zero-day (CVE-2025-0944) to breach local governing bodies in the US
blog.talosintelligence.com/uat-6382-exp...
blog.talosintelligence.com/uat-6382-exp...

UAT-6382 exploits Cityworks zero-day vulnerability to deliver malware
Talos has observed exploitation of CVE-2025-0994 in the wild by UAT-6382, a Chinese-speaking threat actor, who then deployed malware payloads via TetraLoader.
blog.talosintelligence.com
May 22, 2025 at 12:54 PM
Cisco Talos says a group tracked as UAT-6382 has used a recent Trimble CityWorks zero-day (CVE-2025-0944) to breach local governing bodies in the US
blog.talosintelligence.com/uat-6382-exp...
blog.talosintelligence.com/uat-6382-exp...
Reposted by TuxPanik
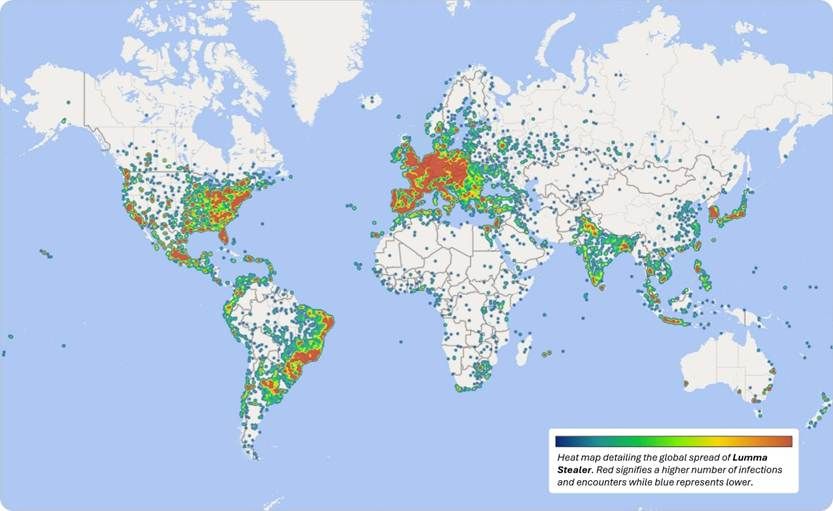
La victimologie de l'infostealer Lumma. Graphique Microsoft.
May 22, 2025 at 4:21 PM
La victimologie de l'infostealer Lumma. Graphique Microsoft.
Reposted by TuxPanik
Looks like there's a DanaBot botnet takedown happening tomorrow
😂
😂
May 22, 2025 at 8:41 PM
Looks like there's a DanaBot botnet takedown happening tomorrow
😂
😂
Reposted by TuxPanik
#Podcast #Cybersécurité
Épisode #502 : un modèle de PSSI pour l'IA (publié par le CLUSIF), avec Michel Dubois
www.nolimitsecu.fr/modele-de-po...
Épisode #502 : un modèle de PSSI pour l'IA (publié par le CLUSIF), avec Michel Dubois
www.nolimitsecu.fr/modele-de-po...

Modèle de Politique de Sécurité des Systèmes d’Information pour l’IA - NoLimitSecu
Episode #502 Dans cet épisode, Michel Dubois nous parle d’un document de référence réalisé par le CLUSIF pouvant servir de base à une Politique de Sécurité des Systèmes d’Information (PSSI) dédiée à l...
www.nolimitsecu.fr
May 19, 2025 at 8:42 AM
#Podcast #Cybersécurité
Épisode #502 : un modèle de PSSI pour l'IA (publié par le CLUSIF), avec Michel Dubois
www.nolimitsecu.fr/modele-de-po...
Épisode #502 : un modèle de PSSI pour l'IA (publié par le CLUSIF), avec Michel Dubois
www.nolimitsecu.fr/modele-de-po...
Reposted by TuxPanik
ESET researchers uncover a Russia-aligned espionage operation targeting webmail servers via XSS vulnerabilities | www.welivesecurity.com/en/eset-rese... @esetofficial.bsky.social

Operation RoundPress targeting high-value webmail servers
ESET researchers uncover a Russia-aligned espionage operation that they named RoundPress and that targets webmail servers via XSS vulnerabilities.
www.welivesecurity.com
May 15, 2025 at 11:16 AM
ESET researchers uncover a Russia-aligned espionage operation targeting webmail servers via XSS vulnerabilities | www.welivesecurity.com/en/eset-rese... @esetofficial.bsky.social
Reposted by TuxPanik
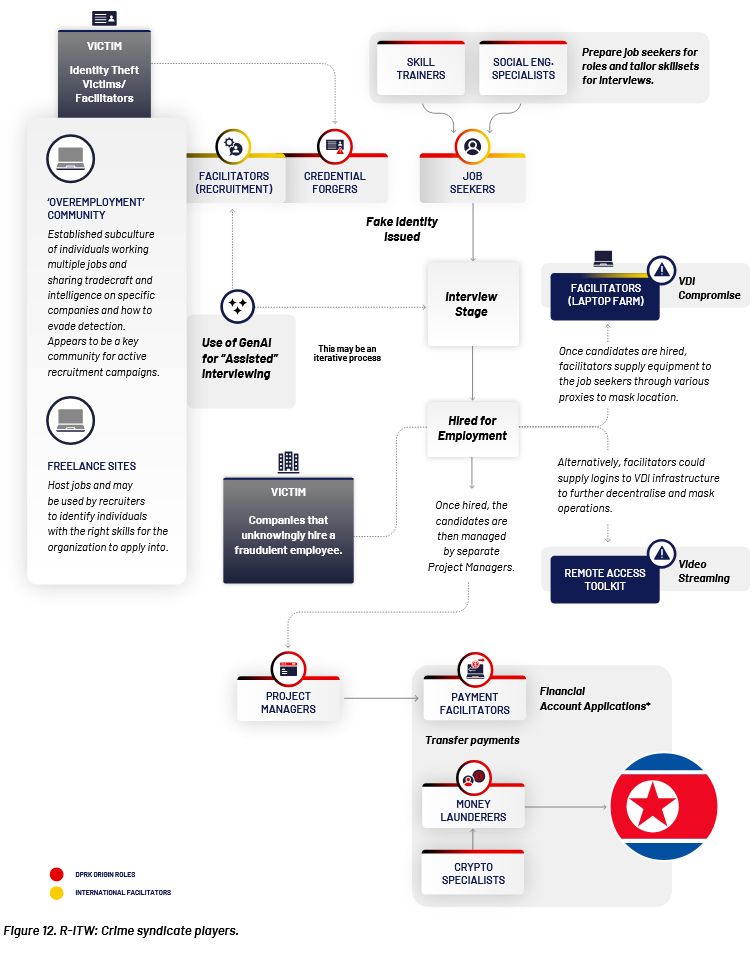
This DTEX report on North Korea's hacking capabilities, along with Viginum's Russian info op report from last week, are probably the best reports of the year so far
You MUST read it!
PDF: reports.dtexsystems.com/DTEX-Exposin...
You MUST read it!
PDF: reports.dtexsystems.com/DTEX-Exposin...
May 15, 2025 at 8:52 AM
This DTEX report on North Korea's hacking capabilities, along with Viginum's Russian info op report from last week, are probably the best reports of the year so far
You MUST read it!
PDF: reports.dtexsystems.com/DTEX-Exposin...
You MUST read it!
PDF: reports.dtexsystems.com/DTEX-Exposin...
Reposted by TuxPanik
Zero-Day Attacks Highlight Another Busy Microsoft Patch Tuesday
www.securityweek.com/zero-day-att...
#Infosec #Security #Cybersecurity #CeptBiro #ZeroDayAttacks #Microsoft #PatchTuesday
www.securityweek.com/zero-day-att...
#Infosec #Security #Cybersecurity #CeptBiro #ZeroDayAttacks #Microsoft #PatchTuesday

Zero-Day Attacks Highlight Another Busy Microsoft Patch Tuesday
Patch Tuesday: Microsoft patches at least 70 security bugs and flagged five zero-days in the “exploitation detected” category.
www.securityweek.com
May 13, 2025 at 8:25 PM
Zero-Day Attacks Highlight Another Busy Microsoft Patch Tuesday
www.securityweek.com/zero-day-att...
#Infosec #Security #Cybersecurity #CeptBiro #ZeroDayAttacks #Microsoft #PatchTuesday
www.securityweek.com/zero-day-att...
#Infosec #Security #Cybersecurity #CeptBiro #ZeroDayAttacks #Microsoft #PatchTuesday
Reposted by TuxPanik
🚨 Microsoft’s May 2025 Patch Tuesday fixes 73 vulnerabilities, including 5 zero-days actively exploited in the wild and 6 critical flaws. windows101tricks.com/microsoft-pa...
💻 Windows users: update now to stay secure.
#CyberSecurity #PatchTuesday #Microsoft #ZeroDay #Windows11 #windows10 #technews
💻 Windows users: update now to stay secure.
#CyberSecurity #PatchTuesday #Microsoft #ZeroDay #Windows11 #windows10 #technews

May 13, 2025 at 8:36 PM
🚨 Microsoft’s May 2025 Patch Tuesday fixes 73 vulnerabilities, including 5 zero-days actively exploited in the wild and 6 critical flaws. windows101tricks.com/microsoft-pa...
💻 Windows users: update now to stay secure.
#CyberSecurity #PatchTuesday #Microsoft #ZeroDay #Windows11 #windows10 #technews
💻 Windows users: update now to stay secure.
#CyberSecurity #PatchTuesday #Microsoft #ZeroDay #Windows11 #windows10 #technews
Reposted by TuxPanik
#Podcast #Cybersécurité
Épisode #501 : détection vs. recherche de compromissions (suite de l'épisode #491), avec @heurs.bsky.social
www.nolimitsecu.fr/detection-vs...
Épisode #501 : détection vs. recherche de compromissions (suite de l'épisode #491), avec @heurs.bsky.social
www.nolimitsecu.fr/detection-vs...

Détection vs Recherche de Compromissions : La discussion continue - NoLimitSecu
Épisode #502 – Détection vs Recherche : La discussion continue (épisode #491) Avec Stéfan LE BERRE
www.nolimitsecu.fr
May 12, 2025 at 6:38 AM
#Podcast #Cybersécurité
Épisode #501 : détection vs. recherche de compromissions (suite de l'épisode #491), avec @heurs.bsky.social
www.nolimitsecu.fr/detection-vs...
Épisode #501 : détection vs. recherche de compromissions (suite de l'épisode #491), avec @heurs.bsky.social
www.nolimitsecu.fr/detection-vs...
Reposted by TuxPanik
A Chinese threat actor that Forescout tracks as Chaya_004 is behind a recent SAP NetWeaver zero-day (CVE-2025-31324)
www.forescout.com/blog/threat-...
www.forescout.com/blog/threat-...

Threat Analysis: SAP Vulnerability in the Wild by Chinese Threat Actor
Forescout’s Vedere Labs research and threat hunting team analyzes SAP vulnerability (CVE-2025-31324) in the wild.
www.forescout.com
May 8, 2025 at 7:14 PM
A Chinese threat actor that Forescout tracks as Chaya_004 is behind a recent SAP NetWeaver zero-day (CVE-2025-31324)
www.forescout.com/blog/threat-...
www.forescout.com/blog/threat-...
Reposted by TuxPanik
Ransomware group ranks EDR/Anti-Malware products. Microsoft in the LOL Tier is surprising. Seems like a great result for CrowdStrike customers.

Conti Ransomware Gang Rank EDR Solutions Based on Ease of Evasion | CyberMaxx
Conti ransomware gang recently published a list of EDR solutions based on how easy they are to bypass during active intrusions.
www.cybermaxx.com
May 1, 2025 at 7:58 PM
Ransomware group ranks EDR/Anti-Malware products. Microsoft in the LOL Tier is surprising. Seems like a great result for CrowdStrike customers.
Reposted by TuxPanik
Amazon, CrowdStrike, Google and Palo Alto Networks claim no change to threat intel sharing under Trump. Top security leaders at some of the largest tech and cybersecurity vendors said public-private collaborative work continues, despite budget cuts and personnel changes. via @mattkapko.com

Amazon, CrowdStrike, Google and Palo Alto Networks claim no change to threat intel sharing under Trump
Top security leaders at some of the largest tech and cybersecurity vendors said public-private collaborative work continues, despite budget cuts and personnel changes.
cyberscoop.com
May 2, 2025 at 9:27 PM
Amazon, CrowdStrike, Google and Palo Alto Networks claim no change to threat intel sharing under Trump. Top security leaders at some of the largest tech and cybersecurity vendors said public-private collaborative work continues, despite budget cuts and personnel changes. via @mattkapko.com
Reposted by TuxPanik
🇯🇵 Hitachi Vantara (hitachivantara.com) victime d'une cyberattaque autour du 26 avril 2025.
👉 https://www.ransomware.live/#/recentcyberattacks
👉 https://www.ransomware.live/#/recentcyberattacks
Source
www.bleepingcomputer.com
April 28, 2025 at 8:14 PM
🇯🇵 Hitachi Vantara (hitachivantara.com) victime d'une cyberattaque autour du 26 avril 2025.
👉 https://www.ransomware.live/#/recentcyberattacks
👉 https://www.ransomware.live/#/recentcyberattacks
Reposted by TuxPanik
Takes a fairly big ransomware attack to break through all the noise…this definitely qualifies.
via @bleepingcomputer.com
via @bleepingcomputer.com

Hitachi Vantara takes servers offline after Akira ransomware attack
Hitachi Vantara, a subsidiary of Japanese multinational conglomerate Hitachi, was forced to take servers offline over the weekend to contain an Akira ransomware attack.
www.bleepingcomputer.com
April 28, 2025 at 7:42 PM
Takes a fairly big ransomware attack to break through all the noise…this definitely qualifies.
via @bleepingcomputer.com
via @bleepingcomputer.com
Reposted by TuxPanik
Did you know that there is a monument to NotPetya in Moscow? It was installed by INVITRO, a Russian medical firm & one of the victims of the 2017 global attack initially aimed at Ukraine. INVITRO's PR goal was to remind the world that it knows how to fight viruses

April 27, 2025 at 10:38 AM
Did you know that there is a monument to NotPetya in Moscow? It was installed by INVITRO, a Russian medical firm & one of the victims of the 2017 global attack initially aimed at Ukraine. INVITRO's PR goal was to remind the world that it knows how to fight viruses
Reposted by TuxPanik
Fortinet's security team has spotted a new Mirai-based IoT botnet in the wild.
They named this one RustoBot because it's coded in Rust.
So far, the botnet only targets TOTOLINK routers.
www.fortinet.com/blog/threat-...
They named this one RustoBot because it's coded in Rust.
So far, the botnet only targets TOTOLINK routers.
www.fortinet.com/blog/threat-...
April 26, 2025 at 10:43 PM
Fortinet's security team has spotted a new Mirai-based IoT botnet in the wild.
They named this one RustoBot because it's coded in Rust.
So far, the botnet only targets TOTOLINK routers.
www.fortinet.com/blog/threat-...
They named this one RustoBot because it's coded in Rust.
So far, the botnet only targets TOTOLINK routers.
www.fortinet.com/blog/threat-...
Reposted by TuxPanik
Threat actors are hacking Teltonika SMS gateways in what appears to be massive SMS spam campaigns.
Attackers are targeting devices that still use their default login credentials of user1/user_pass.
isc.sans.edu/diary/rss/31...
Attackers are targeting devices that still use their default login credentials of user1/user_pass.
isc.sans.edu/diary/rss/31...

Attacks against Teltonika Networks SMS Gateways - SANS Internet Storm Center
Attacks against Teltonika Networks SMS Gateways, Author: Johannes Ullrich
isc.sans.edu
April 26, 2025 at 10:44 PM
Threat actors are hacking Teltonika SMS gateways in what appears to be massive SMS spam campaigns.
Attackers are targeting devices that still use their default login credentials of user1/user_pass.
isc.sans.edu/diary/rss/31...
Attackers are targeting devices that still use their default login credentials of user1/user_pass.
isc.sans.edu/diary/rss/31...

