
All thought are mine and mine alone



The blog post is live! Read it here:
portswigger.net/research/web...

The blog post is live! Read it here:
portswigger.net/research/web...
Join me live on Sept 17 at 4PM (GMT+1)
discord.gg/portswigger?...

Join me live on Sept 17 at 4PM (GMT+1)
discord.gg/portswigger?...

@zakfedotkin.bsky.social
Because why be consistent when you can keep people guessing?
@zakfedotkin.bsky.social
Because why be consistent when you can keep people guessing?
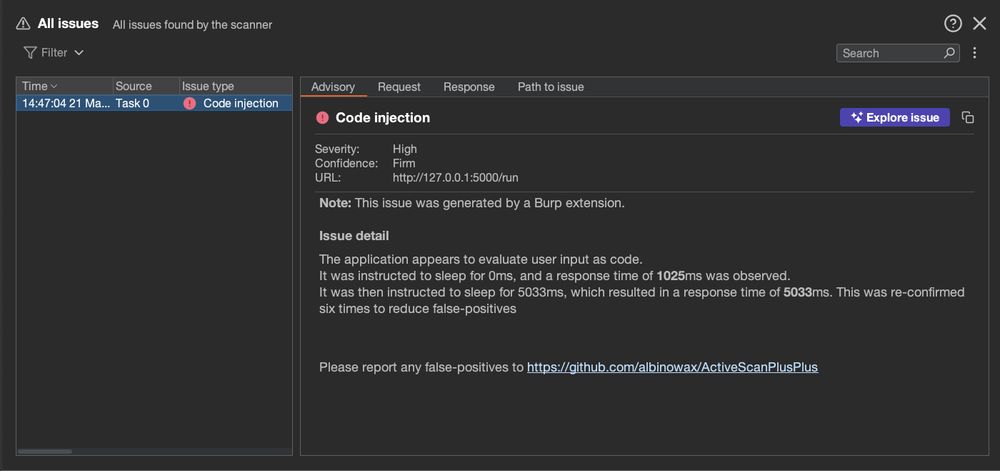

Think again, read our latest blog post!
Link in the comments👇
Think again, read our latest blog post!
Link in the comments👇

This idea came after our previous update from @dyak0xdb, which sparked great discussions! More updates are live. Link in the reply 👇

This idea came after our previous update from @dyak0xdb, which sparked great discussions! More updates are live. Link in the reply 👇

portswigger.net/research/byp...

portswigger.net/research/byp...

Now supports Ruby on Rails Encrypted Cookies:
- Brute force secret keys
- Decrypt cookie values
Update now:

Now supports Ruby on Rails Encrypted Cookies:
- Brute force secret keys
- Decrypt cookie values
Update now:
portswigger.net/research/byp...



