Posts
Media
Videos
Starter Packs
Pinned
adorais.bsky.social
@adorais.bsky.social
· Apr 17

Around the World in 90 Days: State-Sponsored Actors Try ClickFix | Proofpoint US
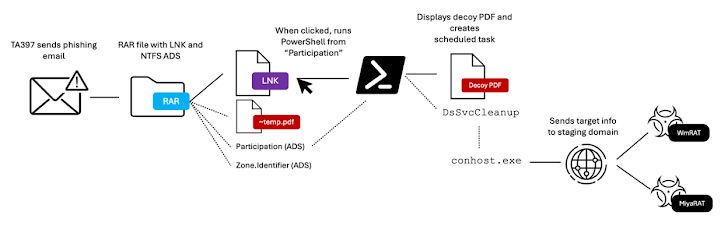
Key Findings While primarily a technique affiliated with cybercriminal actors, Proofpoint researchers discovered state-sponsored actors in multiple campaigns using the ClickFix social
www.proofpoint.com
adorais.bsky.social
@adorais.bsky.social
· May 13
adorais.bsky.social
@adorais.bsky.social
· Apr 17
Saher
@saffronsec.bsky.social
· Apr 17

Around the World in 90 Days: State-Sponsored Actors Try ClickFix | Proofpoint US
Key Findings While primarily a technique affiliated with cybercriminal actors, Proofpoint researchers discovered state-sponsored actors in multiple campaigns using the ClickFix social
www.proofpoint.com
adorais.bsky.social
@adorais.bsky.social
· Apr 17
adorais.bsky.social
@adorais.bsky.social
· Apr 17
adorais.bsky.social
@adorais.bsky.social
· Apr 17

Around the World in 90 Days: State-Sponsored Actors Try ClickFix | Proofpoint US
Key Findings While primarily a technique affiliated with cybercriminal actors, Proofpoint researchers discovered state-sponsored actors in multiple campaigns using the ClickFix social
www.proofpoint.com
adorais.bsky.social
@adorais.bsky.social
· Dec 17
adorais.bsky.social
@adorais.bsky.social
· Dec 12
Reposted