
Alexandre Borges
@alexandreborges.bsky.social
Vulnerability Researcher | Exploit Developer (speaker 3x at DEF CON)
LANDFALL: New Commercial-Grade Android Spyware in Exploit Chain Targeting Samsung Devices:
unit42.paloaltonetworks.com/landfall-is-...
#exploitation #spyware #rce #infosec #cybersecurity #mobilesecurity #samsung #android #rce #vulnerability
unit42.paloaltonetworks.com/landfall-is-...
#exploitation #spyware #rce #infosec #cybersecurity #mobilesecurity #samsung #android #rce #vulnerability

November 8, 2025 at 12:25 AM
LANDFALL: New Commercial-Grade Android Spyware in Exploit Chain Targeting Samsung Devices:
unit42.paloaltonetworks.com/landfall-is-...
#exploitation #spyware #rce #infosec #cybersecurity #mobilesecurity #samsung #android #rce #vulnerability
unit42.paloaltonetworks.com/landfall-is-...
#exploitation #spyware #rce #infosec #cybersecurity #mobilesecurity #samsung #android #rce #vulnerability
Evading Elastic EDR's call stack signatures with call gadgets:
offsec.almond.consulting/evading-elas...
#edr #hacking #evasion #cybersecurity #informationsecurity #windows #programming #elastic
offsec.almond.consulting/evading-elas...
#edr #hacking #evasion #cybersecurity #informationsecurity #windows #programming #elastic

November 7, 2025 at 11:14 PM
Evading Elastic EDR's call stack signatures with call gadgets:
offsec.almond.consulting/evading-elas...
#edr #hacking #evasion #cybersecurity #informationsecurity #windows #programming #elastic
offsec.almond.consulting/evading-elas...
#edr #hacking #evasion #cybersecurity #informationsecurity #windows #programming #elastic
Breaking Into a Brother (MFC-J1010DW): Three Security Flaws in a Seemingly Innocent Printer:
starlabs.sg/blog/2025/11...
#cybersecurity #exploitation #printer #exploit #vulnerability
starlabs.sg/blog/2025/11...
#cybersecurity #exploitation #printer #exploit #vulnerability

November 7, 2025 at 1:14 AM
Breaking Into a Brother (MFC-J1010DW): Three Security Flaws in a Seemingly Innocent Printer:
starlabs.sg/blog/2025/11...
#cybersecurity #exploitation #printer #exploit #vulnerability
starlabs.sg/blog/2025/11...
#cybersecurity #exploitation #printer #exploit #vulnerability
Operation South Star: 0-day Espionage Campaign Targeting Domestic Mobile Phones:
ti.qianxin.com/blog/article...
#exploitation #exploit #threathunting #infosec #vulnerability #mobile #0day #dfir
ti.qianxin.com/blog/article...
#exploitation #exploit #threathunting #infosec #vulnerability #mobile #0day #dfir

November 4, 2025 at 1:38 PM
Operation South Star: 0-day Espionage Campaign Targeting Domestic Mobile Phones:
ti.qianxin.com/blog/article...
#exploitation #exploit #threathunting #infosec #vulnerability #mobile #0day #dfir
ti.qianxin.com/blog/article...
#exploitation #exploit #threathunting #infosec #vulnerability #mobile #0day #dfir
The cryptography behind electronic passports:
blog.trailofbits.com/2025/10/31/t...
#crypto #informationsecurity #cybersecurity #cryptography
blog.trailofbits.com/2025/10/31/t...
#crypto #informationsecurity #cybersecurity #cryptography

October 31, 2025 at 1:58 PM
The cryptography behind electronic passports:
blog.trailofbits.com/2025/10/31/t...
#crypto #informationsecurity #cybersecurity #cryptography
blog.trailofbits.com/2025/10/31/t...
#crypto #informationsecurity #cybersecurity #cryptography
Why nested deserialization is STILL harmful – Magento RCE (CVE-2025-54236):
slcyber.io/assetnote-se...
#infosec #cybersecurity #deserialization #rce #exploit #exploitation #cve
slcyber.io/assetnote-se...
#infosec #cybersecurity #deserialization #rce #exploit #exploitation #cve

October 24, 2025 at 4:00 PM
Why nested deserialization is STILL harmful – Magento RCE (CVE-2025-54236):
slcyber.io/assetnote-se...
#infosec #cybersecurity #deserialization #rce #exploit #exploitation #cve
slcyber.io/assetnote-se...
#infosec #cybersecurity #deserialization #rce #exploit #exploitation #cve
Implementing a Persistent Key-Value Store in a Tamper-Resistant Device for SGX Enclave Applications:
dl.acm.org/doi/abs/10.1...
#sgx #cybersecurity #dataprotection #enclave #informationsecurity
dl.acm.org/doi/abs/10.1...
#sgx #cybersecurity #dataprotection #enclave #informationsecurity

October 23, 2025 at 1:48 AM
Implementing a Persistent Key-Value Store in a Tamper-Resistant Device for SGX Enclave Applications:
dl.acm.org/doi/abs/10.1...
#sgx #cybersecurity #dataprotection #enclave #informationsecurity
dl.acm.org/doi/abs/10.1...
#sgx #cybersecurity #dataprotection #enclave #informationsecurity
Memory Allocation in Go:
nghiant3223.github.io/2025/06/03/m...
#cybersecurity #informationsecurity #internals #golang #memory
nghiant3223.github.io/2025/06/03/m...
#cybersecurity #informationsecurity #internals #golang #memory

September 23, 2025 at 9:02 PM
Memory Allocation in Go:
nghiant3223.github.io/2025/06/03/m...
#cybersecurity #informationsecurity #internals #golang #memory
nghiant3223.github.io/2025/06/03/m...
#cybersecurity #informationsecurity #internals #golang #memory
Fantastic Rootkits: And Where to Find Them:
+ part_1: www.cyberark.com/resources/al...
+ part_2: www.cyberark.com/resources/al...
+ part_3: www.cyberark.com/resources/th...
#rootkit #windows #cybersecurity #malware #arm #informationsecurity
+ part_1: www.cyberark.com/resources/al...
+ part_2: www.cyberark.com/resources/al...
+ part_3: www.cyberark.com/resources/th...
#rootkit #windows #cybersecurity #malware #arm #informationsecurity

September 22, 2025 at 5:38 PM
Fantastic Rootkits: And Where to Find Them:
+ part_1: www.cyberark.com/resources/al...
+ part_2: www.cyberark.com/resources/al...
+ part_3: www.cyberark.com/resources/th...
#rootkit #windows #cybersecurity #malware #arm #informationsecurity
+ part_1: www.cyberark.com/resources/al...
+ part_2: www.cyberark.com/resources/al...
+ part_3: www.cyberark.com/resources/th...
#rootkit #windows #cybersecurity #malware #arm #informationsecurity
Race Against Time in the Kernel’s Clockwork:
streypaws.github.io/posts/Race-A...
#kernel #vulnerability #linux #cybersecurity #exploitation #informationsecurity #android
streypaws.github.io/posts/Race-A...
#kernel #vulnerability #linux #cybersecurity #exploitation #informationsecurity #android

September 13, 2025 at 2:36 PM
Race Against Time in the Kernel’s Clockwork:
streypaws.github.io/posts/Race-A...
#kernel #vulnerability #linux #cybersecurity #exploitation #informationsecurity #android
streypaws.github.io/posts/Race-A...
#kernel #vulnerability #linux #cybersecurity #exploitation #informationsecurity #android
Anatomy of a Billion-Download NPM Supply-Chain Attack:
jdstaerk.substack.com/p/we-just-fo...
github.com/Qix-/node-er...
#supplychainattack #npm #cybersecurity #malware #informationsecurity
jdstaerk.substack.com/p/we-just-fo...
github.com/Qix-/node-er...
#supplychainattack #npm #cybersecurity #malware #informationsecurity

September 8, 2025 at 11:08 PM
Anatomy of a Billion-Download NPM Supply-Chain Attack:
jdstaerk.substack.com/p/we-just-fo...
github.com/Qix-/node-er...
#supplychainattack #npm #cybersecurity #malware #informationsecurity
jdstaerk.substack.com/p/we-just-fo...
github.com/Qix-/node-er...
#supplychainattack #npm #cybersecurity #malware #informationsecurity
Secondary Context Path Traversal in Omnissa Workspace ONE UEM:
slcyber.io/assetnote-se...
#cybersecurity #vulnerability #hacking #securecode #exploitation
slcyber.io/assetnote-se...
#cybersecurity #vulnerability #hacking #securecode #exploitation

September 8, 2025 at 2:02 PM
Secondary Context Path Traversal in Omnissa Workspace ONE UEM:
slcyber.io/assetnote-se...
#cybersecurity #vulnerability #hacking #securecode #exploitation
slcyber.io/assetnote-se...
#cybersecurity #vulnerability #hacking #securecode #exploitation
A Novel Technique for SQL Injection in PDO’s Prepared Statements:
slcyber.io/assetnote-se...
#cybersecurity #hacking #websecurity #webapp #pentest #sql
slcyber.io/assetnote-se...
#cybersecurity #hacking #websecurity #webapp #pentest #sql

September 7, 2025 at 4:27 PM
A Novel Technique for SQL Injection in PDO’s Prepared Statements:
slcyber.io/assetnote-se...
#cybersecurity #hacking #websecurity #webapp #pentest #sql
slcyber.io/assetnote-se...
#cybersecurity #hacking #websecurity #webapp #pentest #sql
What is a CUDA Device Architecture?
modal.com/gpu-glossary...
#gpu #hardware #documentation #informationsecurity #cuda
modal.com/gpu-glossary...
#gpu #hardware #documentation #informationsecurity #cuda

August 14, 2025 at 12:03 AM
What is a CUDA Device Architecture?
modal.com/gpu-glossary...
#gpu #hardware #documentation #informationsecurity #cuda
modal.com/gpu-glossary...
#gpu #hardware #documentation #informationsecurity #cuda
So far, I have already written 15 articles (1045 pages), which have been published on my blog:
blog: exploitreversing.com
Series:
[+] ERS: Exploiting Reversing Series
[+] MAS: Malware Analysis Series
Enjoy reading and have a great day.
#windows #iOS #macOS #chrome #kernel #vulnerability
blog: exploitreversing.com
Series:
[+] ERS: Exploiting Reversing Series
[+] MAS: Malware Analysis Series
Enjoy reading and have a great day.
#windows #iOS #macOS #chrome #kernel #vulnerability

August 11, 2025 at 2:12 PM
So far, I have already written 15 articles (1045 pages), which have been published on my blog:
blog: exploitreversing.com
Series:
[+] ERS: Exploiting Reversing Series
[+] MAS: Malware Analysis Series
Enjoy reading and have a great day.
#windows #iOS #macOS #chrome #kernel #vulnerability
blog: exploitreversing.com
Series:
[+] ERS: Exploiting Reversing Series
[+] MAS: Malware Analysis Series
Enjoy reading and have a great day.
#windows #iOS #macOS #chrome #kernel #vulnerability
Malwoverview version 6.2 has been released:
github.com/alexandrebor...
Read the project page to learn how to adapt the configuration file to the changes.
Note: Updating Malwoverview using pip is not enough.
#threathunting #dfir #malware #incidentresponse
github.com/alexandrebor...
Read the project page to learn how to adapt the configuration file to the changes.
Note: Updating Malwoverview using pip is not enough.
#threathunting #dfir #malware #incidentresponse

July 27, 2025 at 5:22 PM
Malwoverview version 6.2 has been released:
github.com/alexandrebor...
Read the project page to learn how to adapt the configuration file to the changes.
Note: Updating Malwoverview using pip is not enough.
#threathunting #dfir #malware #incidentresponse
github.com/alexandrebor...
Read the project page to learn how to adapt the configuration file to the changes.
Note: Updating Malwoverview using pip is not enough.
#threathunting #dfir #malware #incidentresponse
[CVE-2025-38001] Exploiting All Google kernelCTF Instances And Debian 12 With A 0-Day For $82k: A RBTree Family Drama (Part One: LTS & COS):
syst3mfailure.io/rbtree-famil...
#cybersecurity #informationsecurity #exploitation #google #kernel #linux #cybersecurity #zeroday
syst3mfailure.io/rbtree-famil...
#cybersecurity #informationsecurity #exploitation #google #kernel #linux #cybersecurity #zeroday
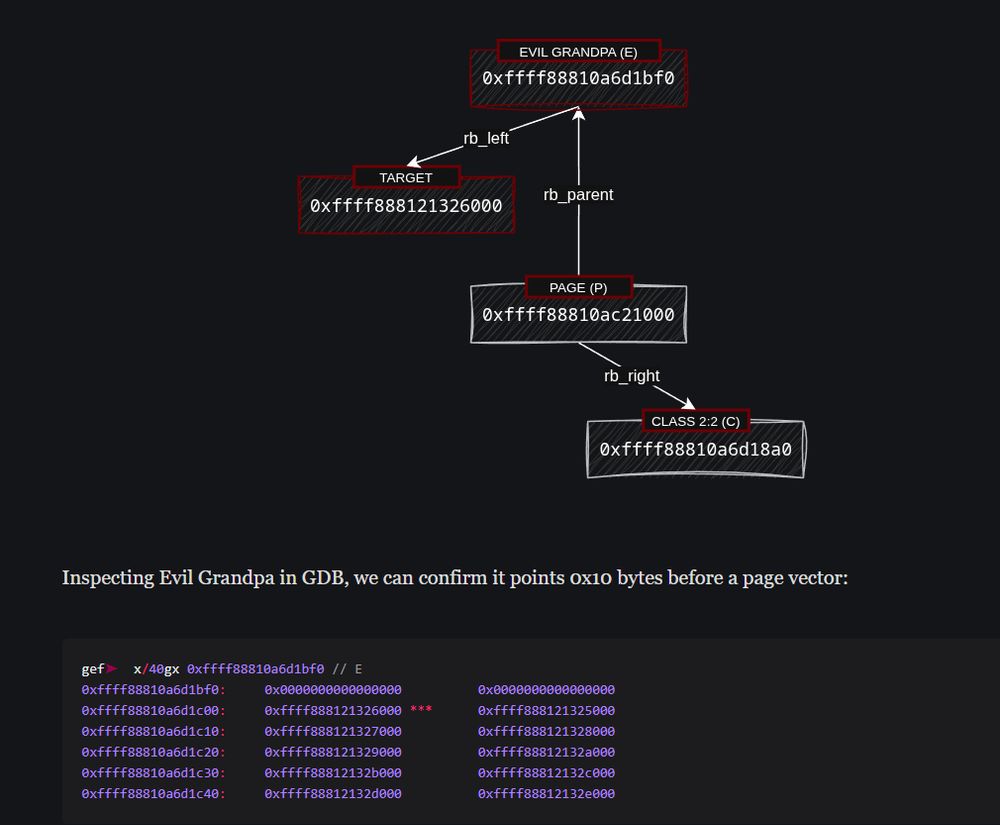
July 12, 2025 at 2:06 PM
[CVE-2025-38001] Exploiting All Google kernelCTF Instances And Debian 12 With A 0-Day For $82k: A RBTree Family Drama (Part One: LTS & COS):
syst3mfailure.io/rbtree-famil...
#cybersecurity #informationsecurity #exploitation #google #kernel #linux #cybersecurity #zeroday
syst3mfailure.io/rbtree-famil...
#cybersecurity #informationsecurity #exploitation #google #kernel #linux #cybersecurity #zeroday
Pwning Solana for Fun and Profit - Exploiting a Subtle Rust Bug for Validator RCE and Money-Printing:
anatomi.st/blog/2025_06...
#cybersecurity #exploiting #exploitation #infosec #informationsecurity #rce #web3 #rust
anatomi.st/blog/2025_06...
#cybersecurity #exploiting #exploitation #infosec #informationsecurity #rce #web3 #rust

June 30, 2025 at 11:31 PM
Pwning Solana for Fun and Profit - Exploiting a Subtle Rust Bug for Validator RCE and Money-Printing:
anatomi.st/blog/2025_06...
#cybersecurity #exploiting #exploitation #infosec #informationsecurity #rce #web3 #rust
anatomi.st/blog/2025_06...
#cybersecurity #exploiting #exploitation #infosec #informationsecurity #rce #web3 #rust
Phantom Persistence:
blog.phantomsec.tools/phantom-pers...
#cybersecurity #hacking #malware #informationsecurity #redteam #blueteam #programming
blog.phantomsec.tools/phantom-pers...
#cybersecurity #hacking #malware #informationsecurity #redteam #blueteam #programming

June 23, 2025 at 4:27 PM
5Ghoul - 5G NR Attacks & 5G OTA Fuzzing:
(project): github.com/asset-group/...
(paper): asset-group.github.io/papers/5Ghou...
#telecom #infosec #cybersecurity #fuzzing #ota #5g #smartphones #mobile #mobilesecurity
(project): github.com/asset-group/...
(paper): asset-group.github.io/papers/5Ghou...
#telecom #infosec #cybersecurity #fuzzing #ota #5g #smartphones #mobile #mobilesecurity

June 17, 2025 at 1:51 PM
5Ghoul - 5G NR Attacks & 5G OTA Fuzzing:
(project): github.com/asset-group/...
(paper): asset-group.github.io/papers/5Ghou...
#telecom #infosec #cybersecurity #fuzzing #ota #5g #smartphones #mobile #mobilesecurity
(project): github.com/asset-group/...
(paper): asset-group.github.io/papers/5Ghou...
#telecom #infosec #cybersecurity #fuzzing #ota #5g #smartphones #mobile #mobilesecurity
Emulating an iPhone in QEMU:
Part 01: eshard.com/posts/emulat...
Part 02: eshard.com/posts/emulat...
#ios #iphone #emulation #cybersecurity #securityresearch #reverseengineering #infosec #informationsecurity
Part 01: eshard.com/posts/emulat...
Part 02: eshard.com/posts/emulat...
#ios #iphone #emulation #cybersecurity #securityresearch #reverseengineering #infosec #informationsecurity

June 6, 2025 at 2:00 PM
Emulating an iPhone in QEMU:
Part 01: eshard.com/posts/emulat...
Part 02: eshard.com/posts/emulat...
#ios #iphone #emulation #cybersecurity #securityresearch #reverseengineering #infosec #informationsecurity
Part 01: eshard.com/posts/emulat...
Part 02: eshard.com/posts/emulat...
#ios #iphone #emulation #cybersecurity #securityresearch #reverseengineering #infosec #informationsecurity
Hypervisors for Memory Introspection and Reverse Engineering:
secret.club/2025/06/02/h...
#reverveengineering #infosec #hypervisor #memoryanalysis #windows #rust
secret.club/2025/06/02/h...
#reverveengineering #infosec #hypervisor #memoryanalysis #windows #rust

June 3, 2025 at 4:40 PM
Hypervisors for Memory Introspection and Reverse Engineering:
secret.club/2025/06/02/h...
#reverveengineering #infosec #hypervisor #memoryanalysis #windows #rust
secret.club/2025/06/02/h...
#reverveengineering #infosec #hypervisor #memoryanalysis #windows #rust
Analysis of CVE-2024-38063 - Exploiting The Kernel Via IPv6 [EN]:
0xreverse.com/analysis-of-...
#cve #kernel #cybersecurity #vulnerability #ipv6 #infosec #windows
0xreverse.com/analysis-of-...
#cve #kernel #cybersecurity #vulnerability #ipv6 #infosec #windows

April 27, 2025 at 3:37 AM
Analysis of CVE-2024-38063 - Exploiting The Kernel Via IPv6 [EN]:
0xreverse.com/analysis-of-...
#cve #kernel #cybersecurity #vulnerability #ipv6 #infosec #windows
0xreverse.com/analysis-of-...
#cve #kernel #cybersecurity #vulnerability #ipv6 #infosec #windows
Technical analysis of CVE-2025-31201: reverse engineering the diff between iOS 18.4 and 18.4.1 to study the changes made to RPAC.:
blog.epsilon-sec.com/cve-2025-312...
#iOS #apple #cybersecurity #reversing #pac #security #cve #vulnerability
blog.epsilon-sec.com/cve-2025-312...
#iOS #apple #cybersecurity #reversing #pac #security #cve #vulnerability

April 20, 2025 at 3:22 PM
Technical analysis of CVE-2025-31201: reverse engineering the diff between iOS 18.4 and 18.4.1 to study the changes made to RPAC.:
blog.epsilon-sec.com/cve-2025-312...
#iOS #apple #cybersecurity #reversing #pac #security #cve #vulnerability
blog.epsilon-sec.com/cve-2025-312...
#iOS #apple #cybersecurity #reversing #pac #security #cve #vulnerability
Auto-color - Linux backdoor :
zw01f.github.io/malware%20an...
#linux #backdoor #informationsecurity #cybersecurity #redteam #malware
zw01f.github.io/malware%20an...
#linux #backdoor #informationsecurity #cybersecurity #redteam #malware

April 7, 2025 at 4:50 PM
Auto-color - Linux backdoor :
zw01f.github.io/malware%20an...
#linux #backdoor #informationsecurity #cybersecurity #redteam #malware
zw01f.github.io/malware%20an...
#linux #backdoor #informationsecurity #cybersecurity #redteam #malware

