








Great whirlwind tour of “just do the fucking basics already”!!!
Loved it.
9/fin


Great whirlwind tour of “just do the fucking basics already”!!!
Loved it.
9/fin


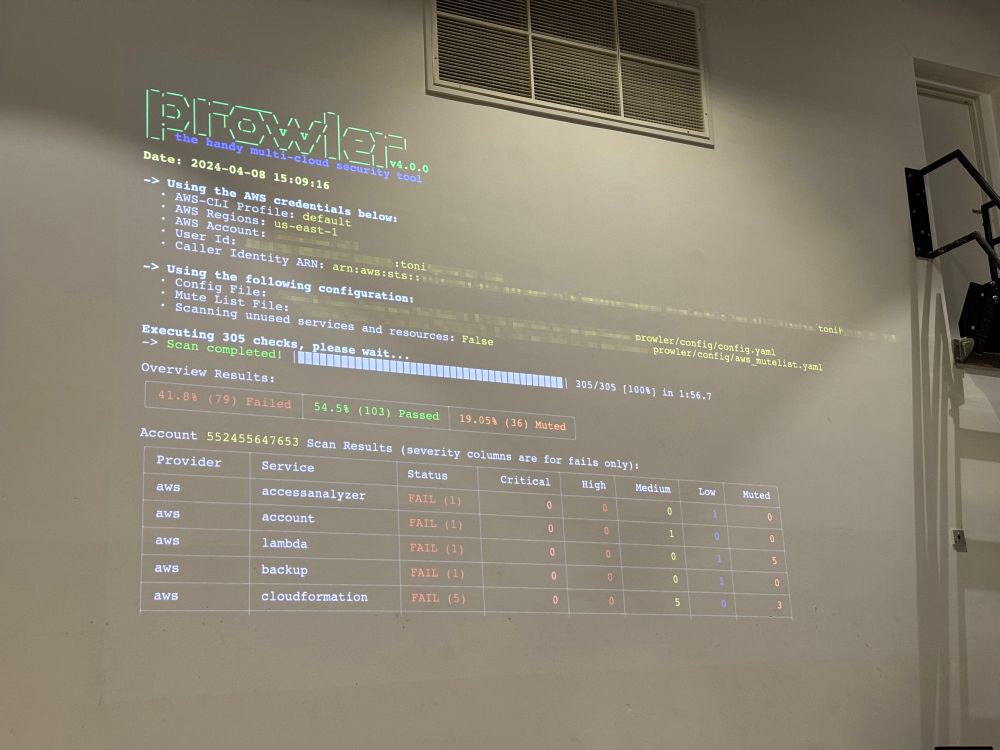









So most of the incidents then.
1/n

So most of the incidents then.
1/n
That was fun!
But how do I launder money, we’ve not learned that yet ;-)
8/fin


That was fun!
But how do I launder money, we’ve not learned that yet ;-)
8/fin






Make a mistake: all your money gone.
Lose your key: all your money gone.
Great - future of finance right there.
4/n

Make a mistake: all your money gone.
Lose your key: all your money gone.
Great - future of finance right there.
4/n
3/n

3/n




