Details: buff.ly/xexR3dP

Details: buff.ly/xexR3dP

But that's only the start of the risk. Those same HITL prompts can have other security risks lurking within them.🧵2/4

But that's only the start of the risk. Those same HITL prompts can have other security risks lurking within them.🧵2/4
#ElysiaJS #CVE202566456 #RCE #AppSec #NodeSecurity #TypeScript 🧵1/5

#ElysiaJS #CVE202566456 #RCE #AppSec #NodeSecurity #TypeScript 🧵1/5
#SupplyChainSecrity #Vulnerability #ProductSecurity #InformationSecurity #CyberSecurity #Patch #Zitadel



#SupplyChainSecrity #Vulnerability #ProductSecurity #InformationSecurity #CyberSecurity #Patch #Zitadel
Details ➜ buff.ly/a5dVfj5
#vLLM #AIVulnerability #LLMSecurity #PyTorch #AppSec #DevSecOps
🧵1/4

Details ➜ buff.ly/a5dVfj5
#vLLM #AIVulnerability #LLMSecurity #PyTorch #AppSec #DevSecOps
🧵1/4
Admins and CI/CD owners should review immediately.
#7zip #RCE #DirectoryTraversal #AppSec #SoftwareSecurity
buff.ly/k6Tv0YL
🧵1/4

Admins and CI/CD owners should review immediately.
#7zip #RCE #DirectoryTraversal #AppSec #SoftwareSecurity
buff.ly/k6Tv0YL
🧵1/4
CVE-2025-64756 (CVSS 7.5) details + fixes: buff.ly/Nwqkdfz
#NPM #JavaScript #OpenSourceSecurity #AppSec #SupplyChainSecurity
🧵1/4

CVE-2025-64756 (CVSS 7.5) details + fixes: buff.ly/Nwqkdfz
#NPM #JavaScript #OpenSourceSecurity #AppSec #SupplyChainSecurity
🧵1/4
#SupplyChainSecurity #NPM #CyberThreat #ContagiousInterview 🧵1/6

#SupplyChainSecurity #NPM #CyberThreat #ContagiousInterview 🧵1/6
CVE-2025-64459 (CVSSv3 9.1) → buff.ly/kfcbY7e
A newly disclosed flaw affects:
• 5.1 (< 5.1.14)
• 4.2 (< 4.2.26)
• 5.2 (< 5.2.8)
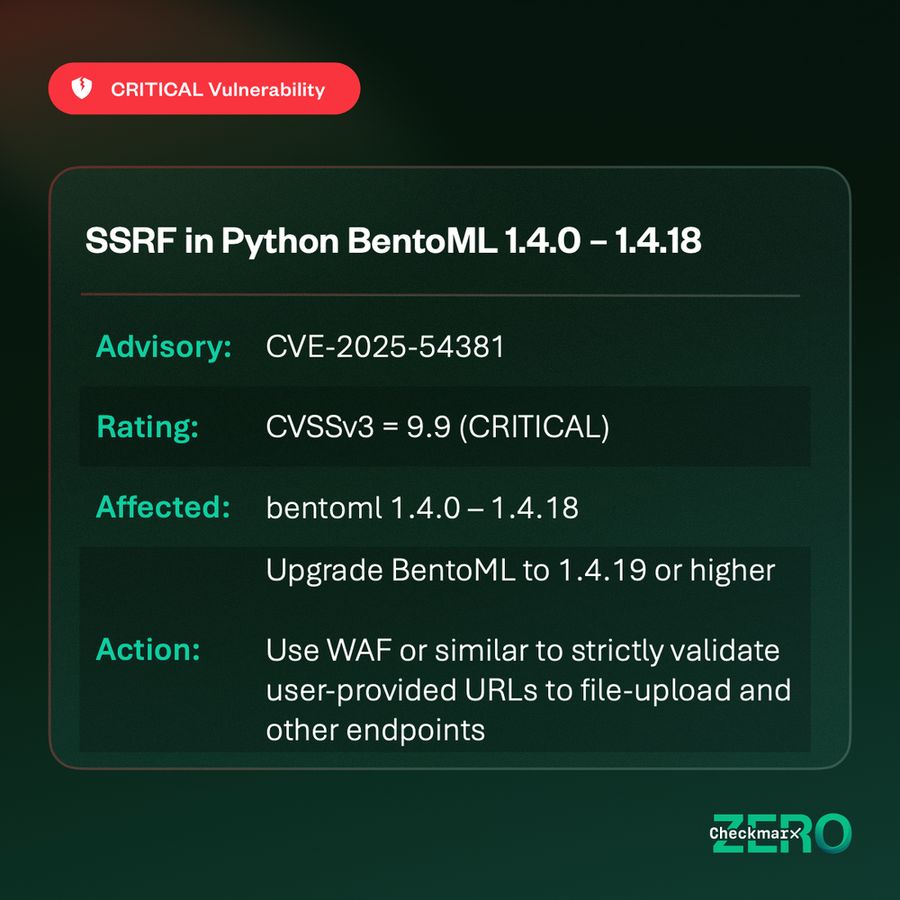
#AppSec #Python #WebSecurity 🧵1/5

CVE-2025-64459 (CVSSv3 9.1) → buff.ly/kfcbY7e
A newly disclosed flaw affects:
• 5.1 (< 5.1.14)
• 4.2 (< 4.2.26)
• 5.2 (< 5.2.8)
#AppSec #Python #WebSecurity 🧵1/5

CVE-2025-64095 -- buff.ly/UdKZLPl 🧵1/3

CVE-2025-64095 -- buff.ly/UdKZLPl 🧵1/3


Severity depends on how your apps handle requests, so calculate your environmental score carefully.
buff.ly/QHRV8ht
🧵1/5

Severity depends on how your apps handle requests, so calculate your environmental score carefully.
buff.ly/QHRV8ht
🧵1/5
#CyberSecurity #SupplyChainSecurity #SCA

#CyberSecurity #SupplyChainSecurity #SCA
Improper input validation → attackers can hijack other users’ sessions. For an #eCommerce platform, this means fraud + reputation damage.
Details: buff.ly/j3UDLHE 🧵1/4

Improper input validation → attackers can hijack other users’ sessions. For an #eCommerce platform, this means fraud + reputation damage.
Details: buff.ly/j3UDLHE 🧵1/4
🔗 buff.ly/MQXOrcZ
#AppSec #Kubernetes #CloudSecurity 🧵1/3

🔗 buff.ly/MQXOrcZ
#AppSec #Kubernetes #CloudSecurity 🧵1/3
If you use the Cozmoslabs WordPress Paid Membership Subscriptions plugin, update to 2.15.2 or newer. 🧵 2/2

If you use the Cozmoslabs WordPress Paid Membership Subscriptions plugin, update to 2.15.2 or newer. 🧵 2/2
It’s rated Medium (CVSS 6.7), but it allows node users to delete their own nodes without permission — a handy privilege escalation for attackers to cover tracks or damage integrity. buff.ly/3a9hIcB
#Kubernetes #CVE #AppSec #CloudSecurity
🧵 1/2

It’s rated Medium (CVSS 6.7), but it allows node users to delete their own nodes without permission — a handy privilege escalation for attackers to cover tracks or damage integrity. buff.ly/3a9hIcB
#Kubernetes #CVE #AppSec #CloudSecurity
🧵 1/2






Mark your calendar! 2pm (local time) on 6th August, at Arsenal Station 5

Mark your calendar! 2pm (local time) on 6th August, at Arsenal Station 5