Dmitri Alperovitch
@dmitri.silverado.org
29K followers
870 following
530 posts
Geopolitics, Russia, China, Cyber
Chairman @silverado.org
Author of WorldOnTheBrink.com
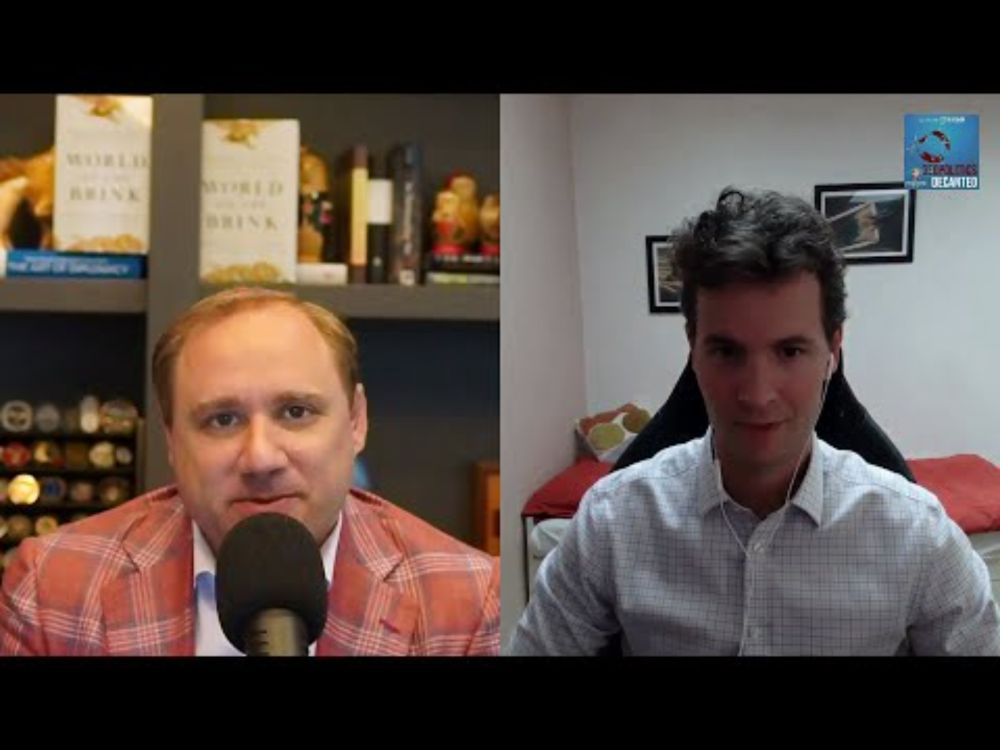
Host GeopoliticsDecanted.com podcast
Founder Alperovitch Institute for Cybersecurity Studies at Johns Hopkins SAIS
Co-Founder CrowdStrike
@DAlperovitch elsewhere
Posts
Media
Videos
Starter Packs
Pinned
Dmitri Alperovitch
@dmitri.silverado.org
· Aug 26
Reposted by Dmitri Alperovitch
Reposted by Dmitri Alperovitch
Dmitri Alperovitch
@dmitri.silverado.org
· Jul 16
Dmitri Alperovitch
@dmitri.silverado.org
· Jul 16
Dmitri Alperovitch
@dmitri.silverado.org
· Jul 16
Dmitri Alperovitch
@dmitri.silverado.org
· Jul 16
Dmitri Alperovitch
@dmitri.silverado.org
· Jul 16
Dmitri Alperovitch
@dmitri.silverado.org
· Jul 16
Dmitri Alperovitch
@dmitri.silverado.org
· Jul 16
Dmitri Alperovitch
@dmitri.silverado.org
· Jul 16
GPU Remote Attestation With Intel® Trust Authority | Intel® Tiber™ Trust Authority
Learn about the Intel® Trust Authority Python Client, CLI for Intel TDX and NVIDIA GPU, and Intel Trust Authority REST API that support GPU attestation.
docs.trustauthority.intel.com
Dmitri Alperovitch
@dmitri.silverado.org
· Jul 16
Dmitri Alperovitch
@dmitri.silverado.org
· Jul 16
Dmitri Alperovitch
@dmitri.silverado.org
· Jul 16
Dmitri Alperovitch
@dmitri.silverado.org
· Jul 16
Dmitri Alperovitch
@dmitri.silverado.org
· Jul 16
Dmitri Alperovitch
@dmitri.silverado.org
· Jul 16
Dmitri Alperovitch
@dmitri.silverado.org
· Jul 16
Dmitri Alperovitch
@dmitri.silverado.org
· Jul 16
Dmitri Alperovitch
@dmitri.silverado.org
· Jul 16