Views expressed here are personal and do not represent the views of my employers.
The tech giant developed a customized version of its cloud platform for Israel’s Unit 8200, which is housing audio files of millions of calls by Palestinians.
www.972mag.com/microsoft-82...

We have now analyzed 9 other benchmarks for scientific reasoning, math, robotics, computer use, and self-driving; we observe generally similar rates of improvement.

We have now analyzed 9 other benchmarks for scientific reasoning, math, robotics, computer use, and self-driving; we observe generally similar rates of improvement.
The results surprised us: Developers thought they were 20% faster with AI tools, but they were actually 19% slower when they had access to AI than when they didn't.
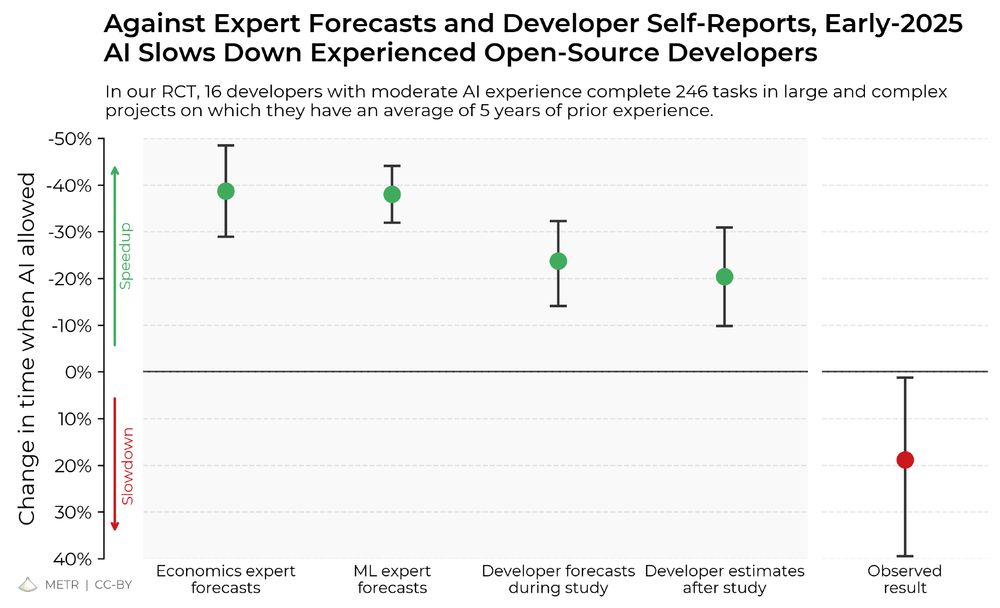
The results surprised us: Developers thought they were 20% faster with AI tools, but they were actually 19% slower when they had access to AI than when they didn't.
Any time you combine access to private data, exposure to untrusted content and the ability to externally communicate an attacker can trick the system into stealing your data […]
Any time you combine access to private data, exposure to untrusted content and the ability to externally communicate an attacker can trick the system into stealing your data […]

Because gaining from AI requires organizational innovation. www.oneusefulthing.org/p/making-ai-...

If you're a podcast person, other coverage includes this podcast from @techpolicypress.bsky.social! www.techpolicy.press/should-agi-r...
If you're a podcast person, other coverage includes this podcast from @techpolicypress.bsky.social! www.techpolicy.press/should-agi-r...

2. The packages don’t exist. Which would normally cause an error but
3. Nefarious people have made malware under the package names that LLMs make up most often. So
4. Now the LLM code points to malware.

2. The packages don’t exist. Which would normally cause an error but
3. Nefarious people have made malware under the package names that LLMs make up most often. So
4. Now the LLM code points to malware.
1. An AI-powered agent's capability is determined by its tools and its planning ability
2. How to select the best tools for your agent
3. How to augment a model’s planning capability
4. Agent’s failure modes
Feedback is much appreciated!

1. An AI-powered agent's capability is determined by its tools and its planning ability
2. How to select the best tools for your agent
3. How to augment a model’s planning capability
4. Agent’s failure modes
Feedback is much appreciated!