Ooh thanks let me fix this
April 24, 2025 at 2:09 AM
Ooh thanks let me fix this
Add progressive web app support and I'll switch back
April 8, 2025 at 6:46 PM
Add progressive web app support and I'll switch back
Lastly:
We're sponsoring PlaidCTF this year at Zellic. This is a lifelong dream of mine. Thank you so much to the organizers for putting on such an excellent CTF each year!
PlaidCTF will be running starting this Friday. Sign up here: plaidctf.com
Cheers!
We're sponsoring PlaidCTF this year at Zellic. This is a lifelong dream of mine. Thank you so much to the organizers for putting on such an excellent CTF each year!
PlaidCTF will be running starting this Friday. Sign up here: plaidctf.com
Cheers!

April 2, 2025 at 8:50 PM
Lastly:
We're sponsoring PlaidCTF this year at Zellic. This is a lifelong dream of mine. Thank you so much to the organizers for putting on such an excellent CTF each year!
PlaidCTF will be running starting this Friday. Sign up here: plaidctf.com
Cheers!
We're sponsoring PlaidCTF this year at Zellic. This is a lifelong dream of mine. Thank you so much to the organizers for putting on such an excellent CTF each year!
PlaidCTF will be running starting this Friday. Sign up here: plaidctf.com
Cheers!
I really enjoyed this challenge. This thread was excerpted from the full writeup, which you can find here: blog.perfect.blue/Lot-of-Fish-...
That’s a Lot of Fish: PlaidCTF 2020
Writeup for the That’s a Lot of Fish challenge from PlaidCTF 2020
blog.perfect.blue
April 2, 2025 at 8:50 PM
I really enjoyed this challenge. This thread was excerpted from the full writeup, which you can find here: blog.perfect.blue/Lot-of-Fish-...
This is a NP complete problem, but luckily we can attack this with dynamic programming. My teammate Sampriti wrote a solver and it gave the solution
[0,9,15,2,1,4,3,8,10,5,13,11,14,6,7,12,0]
And if we feed this into the challenge, we actually get our flag!
[0,9,15,2,1,4,3,8,10,5,13,11,14,6,7,12,0]
And if we feed this into the challenge, we actually get our flag!

April 2, 2025 at 8:50 PM
This is a NP complete problem, but luckily we can attack this with dynamic programming. My teammate Sampriti wrote a solver and it gave the solution
[0,9,15,2,1,4,3,8,10,5,13,11,14,6,7,12,0]
And if we feed this into the challenge, we actually get our flag!
[0,9,15,2,1,4,3,8,10,5,13,11,14,6,7,12,0]
And if we feed this into the challenge, we actually get our flag!
This is asking us to find a permutation of (xs, ys) that results in the Manhattan distances between consecutive points sums to 0x470.
This is essentially finding a Hamiltonian cycle of specified length!
This is essentially finding a Hamiltonian cycle of specified length!
April 2, 2025 at 8:50 PM
This is asking us to find a permutation of (xs, ys) that results in the Manhattan distances between consecutive points sums to 0x470.
This is essentially finding a Hamiltonian cycle of specified length!
This is essentially finding a Hamiltonian cycle of specified length!
If you translate this to pseudocode, it basically implements this check:

April 2, 2025 at 8:50 PM
If you translate this to pseudocode, it basically implements this check:
Now, if you disassemble the bytecode, you'll realize there's control flow... even subroutines and functions!
Here's a screenshot from the Binary Ninja plugin
@hgarrereyn.bsky.social independently wrote as part of his solve.
Here's a screenshot from the Binary Ninja plugin
@hgarrereyn.bsky.social independently wrote as part of his solve.

April 2, 2025 at 8:50 PM
Now, if you disassemble the bytecode, you'll realize there's control flow... even subroutines and functions!
Here's a screenshot from the Binary Ninja plugin
@hgarrereyn.bsky.social independently wrote as part of his solve.
Here's a screenshot from the Binary Ninja plugin
@hgarrereyn.bsky.social independently wrote as part of his solve.
And the big array of binary digits we saw in the very first screenshot is actually the VM’s bytecode.
April 2, 2025 at 8:50 PM
And the big array of binary digits we saw in the very first screenshot is actually the VM’s bytecode.
It initializes a VM state using our input, then applies StepVM until the VM halts and returns a scalar. This scalar is the VM’s exit code (halt state). This final state is asserted to be zero. So our flag needs to satisfy this whole circuit.
April 2, 2025 at 8:50 PM
It initializes a VM state using our input, then applies StepVM until the VM halts and returns a scalar. This scalar is the VM’s exit code (halt state). This final state is asserted to be zero. So our flag needs to satisfy this whole circuit.
Essentially, this entire VM is used as a type constraint on our input!
Meaning, the type system, not any interpreted code, checks our input! The computation is done in this circuit, that is executed through type checking.
Meaning, the type system, not any interpreted code, checks our input! The computation is done in this circuit, that is executed through type checking.
April 2, 2025 at 8:50 PM
Essentially, this entire VM is used as a type constraint on our input!
Meaning, the type system, not any interpreted code, checks our input! The computation is done in this circuit, that is executed through type checking.
Meaning, the type system, not any interpreted code, checks our input! The computation is done in this circuit, that is executed through type checking.
And here's how they actually launch the VM and check the flag with it. They pass the flag as input to the VM (the VM code is parameterized by the input; the VM is parameterized by the code)

April 2, 2025 at 8:50 PM
And here's how they actually launch the VM and check the flag with it. They pass the flag as input to the VM (the VM code is parameterized by the input; the VM is parameterized by the code)
And here's the instruction set.

April 2, 2025 at 8:50 PM
And here's the instruction set.
Here's the full processor state. It also implements binary heaps built in which is very very quirky.
Again, keep in mind every name here used to be the name of a fish🫠 This is all manually renamed
Again, keep in mind every name here used to be the name of a fish🫠 This is all manually renamed

April 2, 2025 at 8:50 PM
Here's the full processor state. It also implements binary heaps built in which is very very quirky.
Again, keep in mind every name here used to be the name of a fish🫠 This is all manually renamed
Again, keep in mind every name here used to be the name of a fish🫠 This is all manually renamed
Guess what! It's a virtual machine.
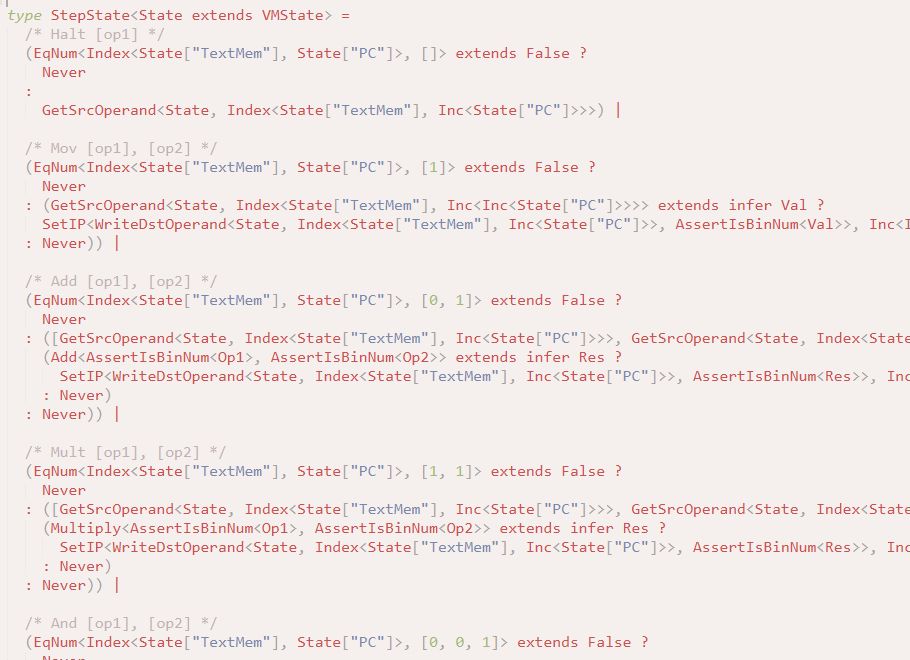
April 2, 2025 at 8:50 PM
Guess what! It's a virtual machine.
Yup... this is implementing computing the operand value for an instruction. Oh boy... this is probably going to be an entire RISC CPU.
RISC processors often fetch operand values during the instruction decode stage, and that's what's going on here.
RISC processors often fetch operand values during the instruction decode stage, and that's what's going on here.

April 2, 2025 at 8:50 PM
Yup... this is implementing computing the operand value for an instruction. Oh boy... this is probably going to be an entire RISC CPU.
RISC processors often fetch operand values during the instruction decode stage, and that's what's going on here.
RISC processors often fetch operand values during the instruction decode stage, and that's what's going on here.
I was feeling pretty good at this point. I was understanding what everything was doing.
But then my heart sank when I saw this.
Can you guess what this does?
But then my heart sank when I saw this.
Can you guess what this does?

April 2, 2025 at 8:50 PM
I was feeling pretty good at this point. I was understanding what everything was doing.
But then my heart sank when I saw this.
Can you guess what this does?
But then my heart sank when I saw this.
Can you guess what this does?
Keep in mind, all of these identifiers and strings were just names of fish.
So I was sitting there discovering how "Tuna" is actually a ripple-carry adder.
So I was sitting there discovering how "Tuna" is actually a ripple-carry adder.
April 2, 2025 at 8:50 PM
Keep in mind, all of these identifiers and strings were just names of fish.
So I was sitting there discovering how "Tuna" is actually a ripple-carry adder.
So I was sitting there discovering how "Tuna" is actually a ripple-carry adder.
Here is how they index into a list. They do this by recursively skipping every other element based on the bits of the index (!!!)

April 2, 2025 at 8:50 PM
Here is how they index into a list. They do this by recursively skipping every other element based on the bits of the index (!!!)
We can even build a multiplier!

April 2, 2025 at 8:50 PM
We can even build a multiplier!
What about bitwise arithmetic?

April 2, 2025 at 8:50 PM
What about bitwise arithmetic?
Now you may be wondering... that's great but how can we do arithmetic? How do we add two BinNums?
Well...using a full adder of course :-)
Well...using a full adder of course :-)

April 2, 2025 at 8:50 PM
Now you may be wondering... that's great but how can we do arithmetic? How do we add two BinNums?
Well...using a full adder of course :-)
Well...using a full adder of course :-)
So this is basically building up bit-level computation. The types set up a circuit, and valid evaluations of the circuit type check.
The flag checker is implemented in this circuit, and we need to (1) reverse how logic is implemented in circuit form; then (2) reverse the logic.
The flag checker is implemented in this circuit, and we need to (1) reverse how logic is implemented in circuit form; then (2) reverse the logic.
April 2, 2025 at 8:50 PM
So this is basically building up bit-level computation. The types set up a circuit, and valid evaluations of the circuit type check.
The flag checker is implemented in this circuit, and we need to (1) reverse how logic is implemented in circuit form; then (2) reverse the logic.
The flag checker is implemented in this circuit, and we need to (1) reverse how logic is implemented in circuit form; then (2) reverse the logic.

