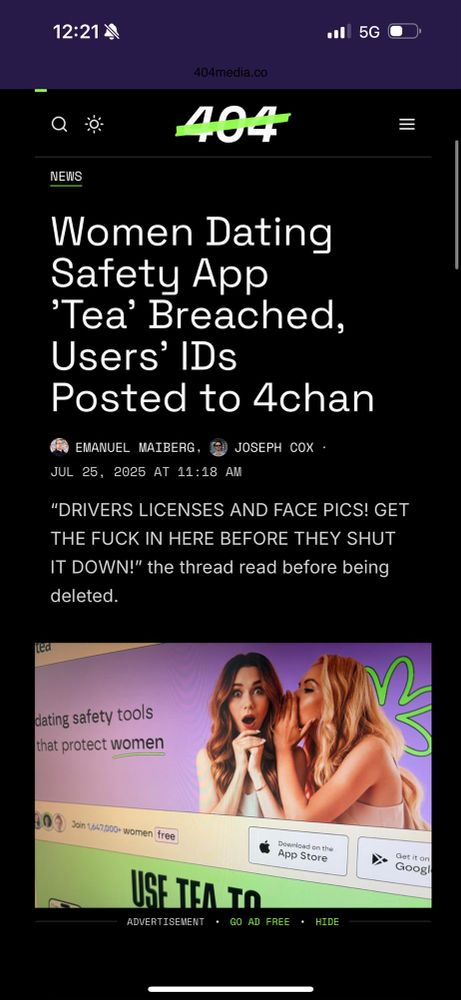
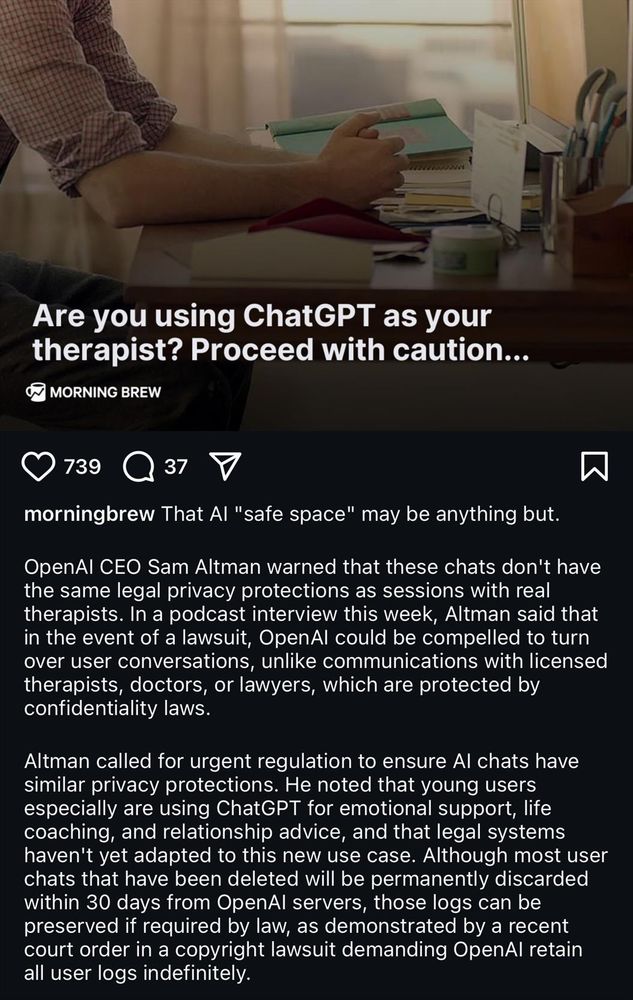
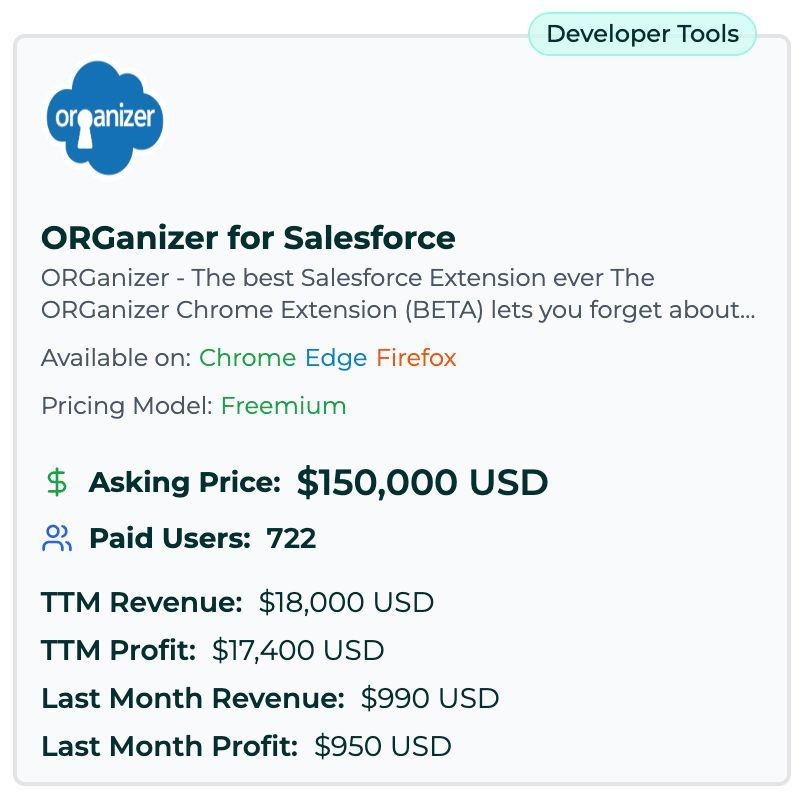
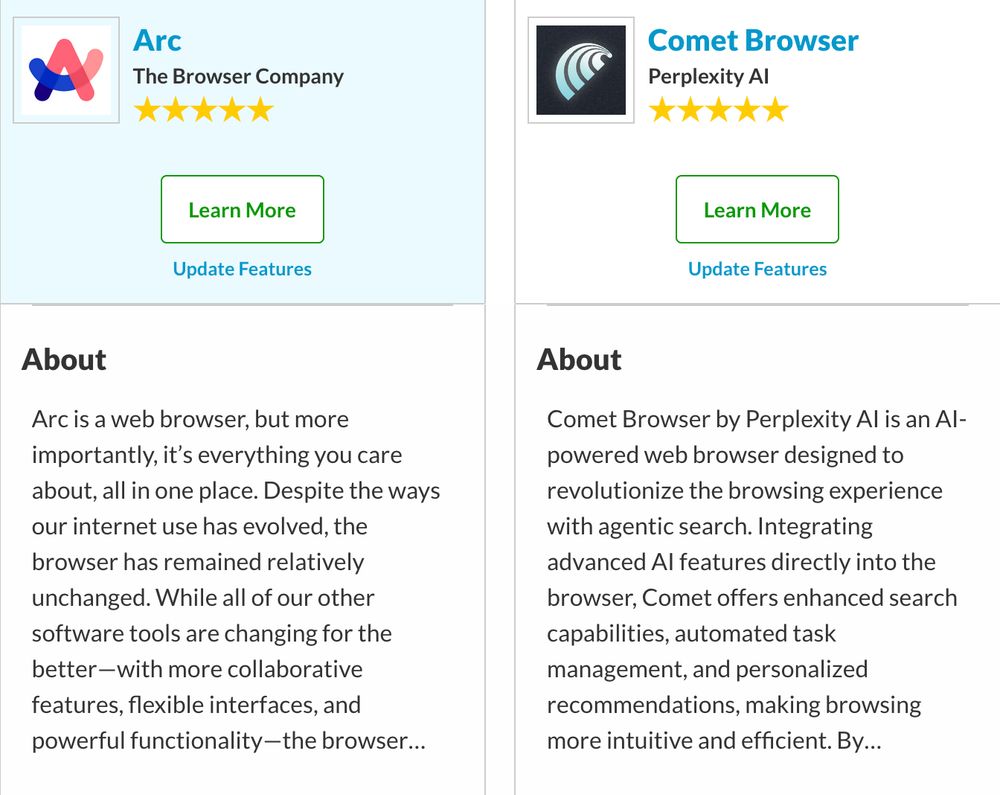
Matt Johansen
@mattjay.com
9.9K followers
480 following
810 posts
Friendly neighborhood cybersecurity guy | expect infosec news, appsec, cloud, dfir. | Long Island elder emo in ATX.
vulnu.com <- sign up for my weekly cybersecurity newsletter
Posts
Media
Videos
Starter Packs