
Attackers use AI to move more rapidly and quietly and get closer to your crown jewels. Anyone who has worked a cloud investigation knows how fast that early activity can disappear into normal noise.
More AIDR best practices: https://loom.ly/SkfW9Mc

Attackers use AI to move more rapidly and quietly and get closer to your crown jewels. Anyone who has worked a cloud investigation knows how fast that early activity can disappear into normal noise.
More AIDR best practices: https://loom.ly/SkfW9Mc
70% had critical or high-severity vulnerabilities in GitHub Actions workflows.
This research breaks down the most prevalent vulnerabilities, how attackers exploit them, and what to fix before it matters.
🔗 https://loom.ly/4EF7bPs

70% had critical or high-severity vulnerabilities in GitHub Actions workflows.
This research breaks down the most prevalent vulnerabilities, how attackers exploit them, and what to fix before it matters.
🔗 https://loom.ly/4EF7bPs
Attackers are entering through connected apps. Once inside, they move fast.
See the offer. Read the breakdowns. Start preventing.
https://loom.ly/YHHGQ-A

Attackers are entering through connected apps. Once inside, they move fast.
See the offer. Read the breakdowns. Start preventing.
https://loom.ly/YHHGQ-A
To every employee pushing the limits. To every partner extending our reach. This is your win.
Let them come.
https://loom.ly/X795lbc

To every employee pushing the limits. To every partner extending our reach. This is your win.
Let them come.
https://loom.ly/X795lbc

With Mitiga, they get nothing.
That's Zero-Impact Breach Prevention across Cloud, SaaS, AI, and Identity.
Real containment. No impact.
Let them come.
With Mitiga, they get nothing.
That's Zero-Impact Breach Prevention across Cloud, SaaS, AI, and Identity.
Real containment. No impact.
Let them come.
The ones who keep watch when others wind down.
The ones who ask the hard questions.
The ones who act before it’s too late.
We built Mitiga for you.
For resilience, not reaction.
For action, not aftermath.
Let them come.

The ones who keep watch when others wind down.
The ones who ask the hard questions.
The ones who act before it’s too late.
We built Mitiga for you.
For resilience, not reaction.
For action, not aftermath.
Let them come.

Attackers are stealing OAuth tokens from connected applications, like those from #Salesloft and #Gainsight, then walking in with full access. https://loom.ly/FRI71Eo

Attackers are stealing OAuth tokens from connected applications, like those from #Salesloft and #Gainsight, then walking in with full access. https://loom.ly/FRI71Eo

Brian Contos takes us inside cloud threat detection with behavioral analytics across AWS, GCP, and more. https://loom.ly/6qDt5kE
Brian Contos takes us inside cloud threat detection with behavioral analytics across AWS, GCP, and more. https://loom.ly/6qDt5kE
In this new episode of Mitiga Mic, Arif Khan, senior director leading services at Mitiga, breaks down how his team stops what legacy tools miss — before attackers do damage.
🎧 Watch now → https://loom.ly/QlQNdpU

In this new episode of Mitiga Mic, Arif Khan, senior director leading services at Mitiga, breaks down how his team stops what legacy tools miss — before attackers do damage.
🎧 Watch now → https://loom.ly/QlQNdpU
Gopal Padinjaruveetil, CISO at AAA, explains why SaaS, identity, and multi-cloud visibility define modern defense. And why every CISO is racing to connect the dots across their environments.
Gopal Padinjaruveetil, CISO at AAA, explains why SaaS, identity, and multi-cloud visibility define modern defense. And why every CISO is racing to connect the dots across their environments.
In our new “Now You See Me” series, Mitiga Labs breaks down the logs, risks, and detection tips SaaS defenders can’t afford to miss. https://loom.ly/imueWOs

In our new “Now You See Me” series, Mitiga Labs breaks down the logs, risks, and detection tips SaaS defenders can’t afford to miss. https://loom.ly/imueWOs
Often, it takes curiosity and persistence. Roei Sherman had his own interesting path. Now he's the head of research for Mitiga Labs. Hear his story on #MitigaMic. https://loom.ly/Ak0YXIs
Often, it takes curiosity and persistence. Roei Sherman had his own interesting path. Now he's the head of research for Mitiga Labs. Hear his story on #MitigaMic. https://loom.ly/Ak0YXIs
Best Practice number 4 in John Vecchi's blog focuses on speed of response: automate cloud investigations and root cause analysis at scale. https://loom.ly/SkfW9Mc

Best Practice number 4 in John Vecchi's blog focuses on speed of response: automate cloud investigations and root cause analysis at scale. https://loom.ly/SkfW9Mc
CISOs like Gopal Padinjaruveetil (AAA) know that keeping up with this velocity takes more than posture-based prevention. It takes real-time detection, response, and genuine cyber resilience.
CISOs like Gopal Padinjaruveetil (AAA) know that keeping up with this velocity takes more than posture-based prevention. It takes real-time detection, response, and genuine cyber resilience.
One user. One token.
That’s how attackers breached Nikkei’s Slack and exposed 17,000+ records.
SaaS is the soft underbelly: minimal visibility, direct access.
Let them come — but make sure they get nothing. https://loom.ly/iNw5iQQ

One user. One token.
That’s how attackers breached Nikkei’s Slack and exposed 17,000+ records.
SaaS is the soft underbelly: minimal visibility, direct access.
Let them come — but make sure they get nothing. https://loom.ly/iNw5iQQ
If you’re ready to fight smarter — and make sure attackers walk away with nothing — let’s talk.
At Mitiga, we’re building a world where breaches don’t matter.
https://loom.ly/BIMiBuc

If you’re ready to fight smarter — and make sure attackers walk away with nothing — let’s talk.
At Mitiga, we’re building a world where breaches don’t matter.
https://loom.ly/BIMiBuc
By the time an alert lands, the attack is already spreading across systems, identities, and SaaS apps.
Read "Top 5 Best Practices for AI-Powered Cloud Detection and Response": https://loom.ly/SkfW9Mc

By the time an alert lands, the attack is already spreading across systems, identities, and SaaS apps.
Read "Top 5 Best Practices for AI-Powered Cloud Detection and Response": https://loom.ly/SkfW9Mc
📺 loom.ly/Ak0YXIs

📺 loom.ly/Ak0YXIs
Attackers get in through SaaS and move fast across cloud and identity.
Mitiga delivers Zero-Impact Breach Prevention detecting and responding before attacks cause impact. https://loom.ly/AZMTQ8s
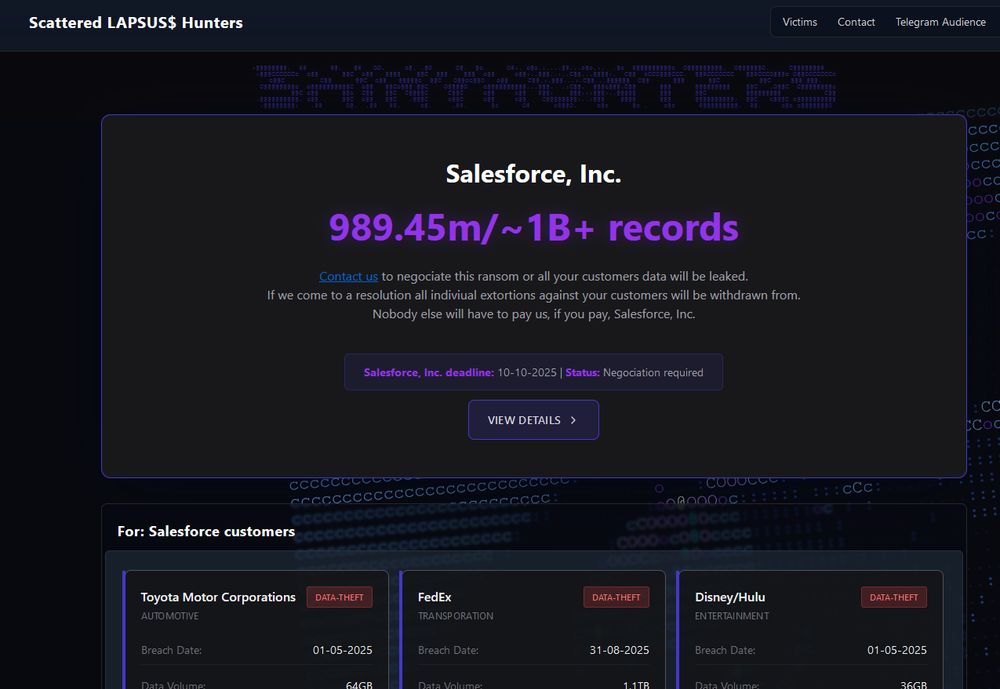
Attackers get in through SaaS and move fast across cloud and identity.
Mitiga delivers Zero-Impact Breach Prevention detecting and responding before attacks cause impact. https://loom.ly/AZMTQ8s
Good. We're watching.
When attackers try to blend in, our AI-native platform already knows that something isn't quite right.
Let them come.
Good. We're watching.
When attackers try to blend in, our AI-native platform already knows that something isn't quite right.
Let them come.


