Mastodon: https://s.pebcak.de/@winni
- native post-quantum keys
- built-in recipients for hw plugins
- age-inspect tool
- plugin framework
- batchpass plugin
- many improved error messages

- native post-quantum keys
- built-in recipients for hw plugins
- age-inspect tool
- plugin framework
- batchpass plugin
- many improved error messages
🔐 Security: Includes security fixes for crypto/x509 (CVE-2025-61729, CVE-2025-61727).
🗣 Announcement: https://groups.google.com/g/golang-announce/c/8FJoBkPddm4/m/kYpVlPw1CQAJ
📦 Download: https://go.dev/dl/#go1.25.5
#golang

🔐 Security: Includes security fixes for crypto/x509 (CVE-2025-61729, CVE-2025-61727).
🗣 Announcement: https://groups.google.com/g/golang-announce/c/8FJoBkPddm4/m/kYpVlPw1CQAJ
📦 Download: https://go.dev/dl/#go1.25.5
#golang
github.com/rs/cors/issu...

github.com/rs/cors/issu...
Check it out! github.com/wneessen/way...
#linux #waybar #golang
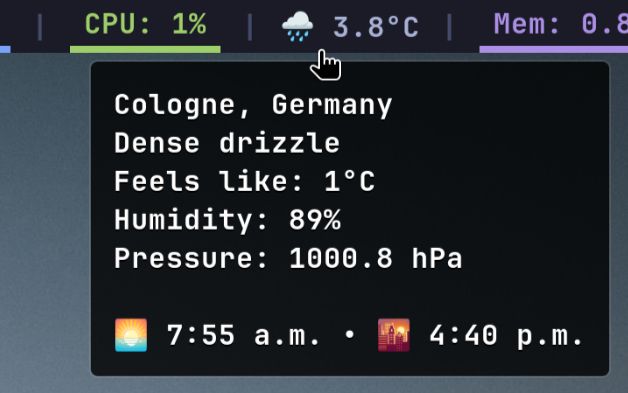

Check it out! github.com/wneessen/way...
#linux #waybar #golang
blog.cloudflare.com/18-november-...

blog.cloudflare.com/18-november-...
Feedback is, as always, welcome!
github.com/wneessen/way...
#linux #waybar #weather

Feedback is, as always, welcome!
github.com/wneessen/way...
#linux #waybar #weather
📡 Announcement: https://groups.google.com/g/golang-announce/c/tVVHm9gnwl8/m/-oTvYIjCAQAJ
🗃 Download: https://go.dev/dl/#go1.25.4
#golang

📡 Announcement: https://groups.google.com/g/golang-announce/c/tVVHm9gnwl8/m/-oTvYIjCAQAJ
🗃 Download: https://go.dev/dl/#go1.25.4
#golang
Phishing regularly upends people's lives. The Safe Browsing cat-and-mouse with all its opaque false positives will be necessary until we roll out phishing-resistant auth.
Phishing regularly upends people's lives. The Safe Browsing cat-and-mouse with all its opaque false positives will be necessary until we roll out phishing-resistant auth.
age still isn't PQ because it's waiting for trivial details of the HPKE hybrids to stabilize, but they are blocked on the CFRG.
The TLS, SSHM, and LAMPS (X.509) IETF WGs are not waiting for CFRG. I just posted a plea for HPKE to do the same.
age still isn't PQ because it's waiting for trivial details of the HPKE hybrids to stabilize, but they are blocked on the CFRG.
The TLS, SSHM, and LAMPS (X.509) IETF WGs are not waiting for CFRG. I just posted a plea for HPKE to do the same.
📣 Announcement: https://groups.google.com/g/golang-announce/c/YEyj6FUNbik/m/_SDlIvxuCAAJ
⬇️ Download: https://go.dev/dl/#go1.25.3
#golang

📣 Announcement: https://groups.google.com/g/golang-announce/c/YEyj6FUNbik/m/_SDlIvxuCAAJ
⬇️ Download: https://go.dev/dl/#go1.25.3
#golang
📢 Announcement: https://groups.google.com/g/golang-announce/c/4Emdl2iQ_bI/m/qZN5nc-mBgAJ
📦 Download: https://go.dev/dl/#go1.25.2
#golang

📢 Announcement: https://groups.google.com/g/golang-announce/c/4Emdl2iQ_bI/m/qZN5nc-mBgAJ
📦 Download: https://go.dev/dl/#go1.25.2
#golang
You can find the release notes here: github.com/wneessen/go-...
The corresponding security advisory can be found here: github.com/wneessen/go-...
We encouraged to update!

You can find the release notes here: github.com/wneessen/go-...
The corresponding security advisory can be found here: github.com/wneessen/go-...
We encouraged to update!
github.com/golang/go/is...

github.com/golang/go/is...
www.datadoghq.com/blog/continu...

www.datadoghq.com/blog/continu...
FIPS 140, like it or not, is often a requirement, and I was increasingly sad about large deployments replacing the Go crypto packages with non-memory safe cgo bindings.
Go is now one of the easiest and most secure ways to build under FIPS 140.
FIPS 140, like it or not, is often a requirement, and I was increasingly sad about large deployments replacing the Go crypto packages with non-memory safe cgo bindings.
Go is now one of the easiest and most secure ways to build under FIPS 140.
💀 Now that Private-Network Access (PNA) has been put on indefinite hold in favor of a new permission-based mechanism named "Local-Network Access", I've removed all support for PNA.
github.com/jub0bs/cors

💀 Now that Private-Network Access (PNA) has been put on indefinite hold in favor of a new permission-based mechanism named "Local-Network Access", I've removed all support for PNA.
github.com/jub0bs/cors
🏃♀️ Run it in dev! Run it in prod! File bugs! go.dev/issue/new
📢 Announcement: groups.google.com/g/golang-ann...
📦 Download: go.dev/dl/#go1.25rc1
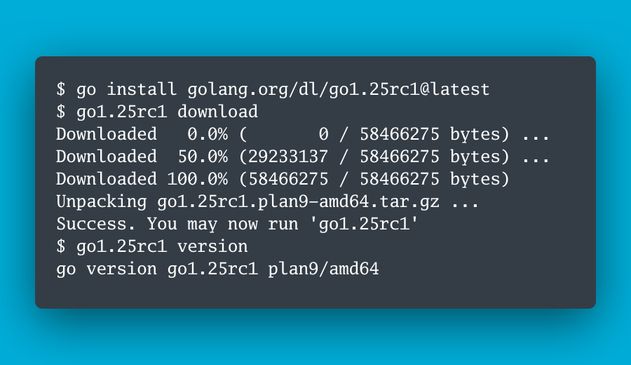
🏃♀️ Run it in dev! Run it in prod! File bugs! go.dev/issue/new
📢 Announcement: groups.google.com/g/golang-ann...
📦 Download: go.dev/dl/#go1.25rc1

go.dev/blog/error-s...
#golang

go.dev/blog/error-s...
#golang
Years of efforts on testing, limiting complexity, safe APIs, and readability have paid off! ✨
Yes I am taking a victory lap. No I am not sorry. 🏆

Years of efforts on testing, limiting complexity, safe APIs, and readability have paid off! ✨
Yes I am taking a victory lap. No I am not sorry. 🏆

Years of efforts on testing, limiting complexity, safe APIs, and readability have paid off! ✨
Yes I am taking a victory lap. No I am not sorry. 🏆




