
The new Genkit Extension for Gemini CLI brings intelligent code generation, debugging, and best practices guidance directly into your command line.
See how it helps you build smarter AI apps → goo.gle/4nNmrr4

The new Genkit Extension for Gemini CLI brings intelligent code generation, debugging, and best practices guidance directly into your command line.
See how it helps you build smarter AI apps → goo.gle/4nNmrr4
⚡️ Imagen 4: Now available to enhance creative development. Preview via Gemini API and Google AI Studio.
Learn more: goo.gle/3Tc3C30
#BuildwithGemini




⚡️ Imagen 4: Now available to enhance creative development. Preview via Gemini API and Google AI Studio.
Learn more: goo.gle/3Tc3C30
#BuildwithGemini
www.independent.co.uk/news/uk/poli...

www.independent.co.uk/news/uk/poli...
#GDE #DockerCaptain #UIPathMVP
#GDE #DockerCaptain #UIPathMVP
Def going to integrate this work into Konductor devcontainer next, but I really enjoyed learning about some of the new tooling making code chores a lot easier.
Blog for giggles.
Def going to integrate this work into Konductor devcontainer next, but I really enjoyed learning about some of the new tooling making code chores a lot easier.
Blog for giggles.
I don't even really need to start using it. Just having it nearby is comforting enough that I feel more in control of my life.
I don't even really need to start using it. Just having it nearby is comforting enough that I feel more in control of my life.
A curated collection covering models, datasets, reward designs, optimization methods, hyperparameters, empirical findings, theoretical insights, and everything about reasoning with reinforcement learning.
github.com/TsinghuaC3I/...

A curated collection covering models, datasets, reward designs, optimization methods, hyperparameters, empirical findings, theoretical insights, and everything about reasoning with reinforcement learning.
github.com/TsinghuaC3I/...

🧱 Examples of:
- Hexagonal & event-driven microservices
- Perf, scalability & resiliency tactics
- REST, schema-first, async logging, caching & more
Check it out 👉 github.com/ionutbalosin...
#Java #Architecture #Microservices #OpenSource
🧱 Examples of:
- Hexagonal & event-driven microservices
- Perf, scalability & resiliency tactics
- REST, schema-first, async logging, caching & more
Check it out 👉 github.com/ionutbalosin...
#Java #Architecture #Microservices #OpenSource

There were 4 Docker Captains present, one coming all the way from Karlsruhe to attend. 🐳
To learn more, check my blog post:
dev.to/docker/run-g...


There were 4 Docker Captains present, one coming all the way from Karlsruhe to attend. 🐳
To learn more, check my blog post:
dev.to/docker/run-g...
epoch.ai/data/ai-benc... (You may need to tweak the graph a bit to see Gemini 2.5 Pro)

epoch.ai/data/ai-benc... (You may need to tweak the graph a bit to see Gemini 2.5 Pro)
🔗: mcgill-nlp.github.io/thoughtology/
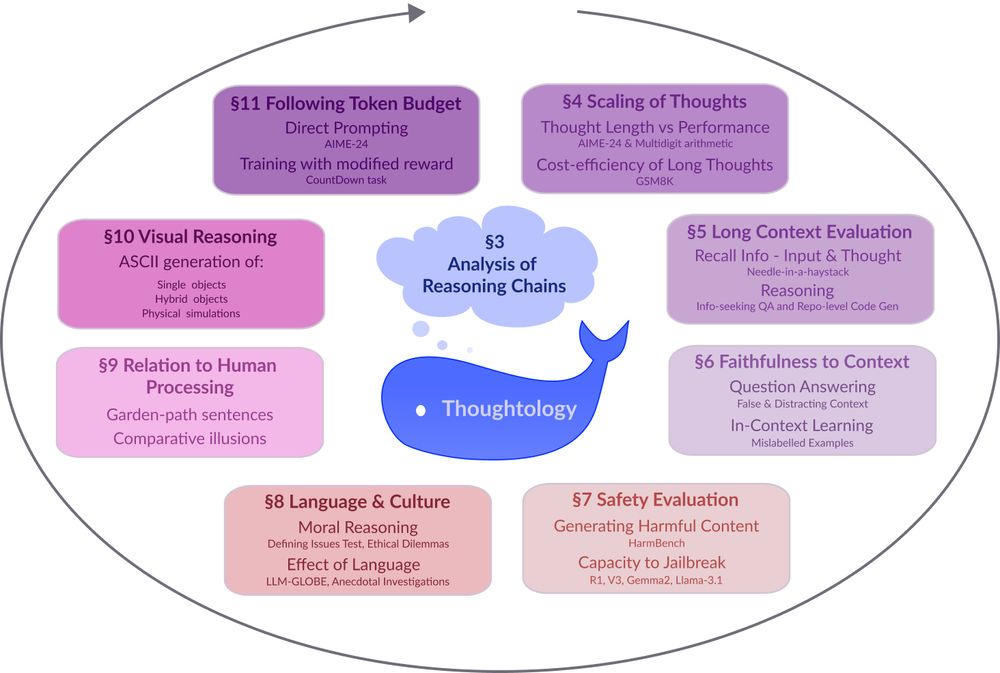
🔗: mcgill-nlp.github.io/thoughtology/
"NoProp: Training Neural Networks without Back-propagation or Forward-propagation"

"NoProp: Training Neural Networks without Back-propagation or Forward-propagation"
github.com/DockYard/ope...
This release is a full re-write from the ground up by Andrew Dryga, moving from HTTPoison to Finch, a smattering of bug fixes, and a full docs overhaul

github.com/DockYard/ope...
This release is a full re-write from the ground up by Andrew Dryga, moving from HTTPoison to Finch, a smattering of bug fixes, and a full docs overhaul
gdg.community.dev/events/detai...

gdg.community.dev/events/detai...
1️⃣ Run dbt pipelines on Cloud Run with CloudRunExecuteJobOperator
2️⃣ Use Cosmos Library to mirror dbt models in Airflow
Links in comments👇🏻
#GoogleCloud #dbt #ApacheAirflow

1️⃣ Run dbt pipelines on Cloud Run with CloudRunExecuteJobOperator
2️⃣ Use Cosmos Library to mirror dbt models in Airflow
Links in comments👇🏻
#GoogleCloud #dbt #ApacheAirflow
Apply until March 15, 2025! We are looking forward to your application!
2025.semanticwebschool.org

Apply until March 15, 2025! We are looking forward to your application!
2025.semanticwebschool.org
apichangelog.substack.com/p/three-mean...

apichangelog.substack.com/p/three-mean...


https://hackerone.com/reports/3022041

https://hackerone.com/reports/3022041
A 1, 2 and 3 bedroom apartment all accessed from the same core (no corridors).
The larger apartments face east-west and have balconies each side, allowing for cross ventilation.


A 1, 2 and 3 bedroom apartment all accessed from the same core (no corridors).
The larger apartments face east-west and have balconies each side, allowing for cross ventilation.
HTTPS everywhere is less controversial today I think.
https://daniel.haxx.se/blog/2015/03/06/tls-in-http2/

HTTPS everywhere is less controversial today I think.
https://daniel.haxx.se/blog/2015/03/06/tls-in-http2/


