
Hello @grapheneos.org
security.googleblog.com/2025/05/adva...

security.googleblog.com/2025/05/adva...
In the United States, we have him the nuclear codes.
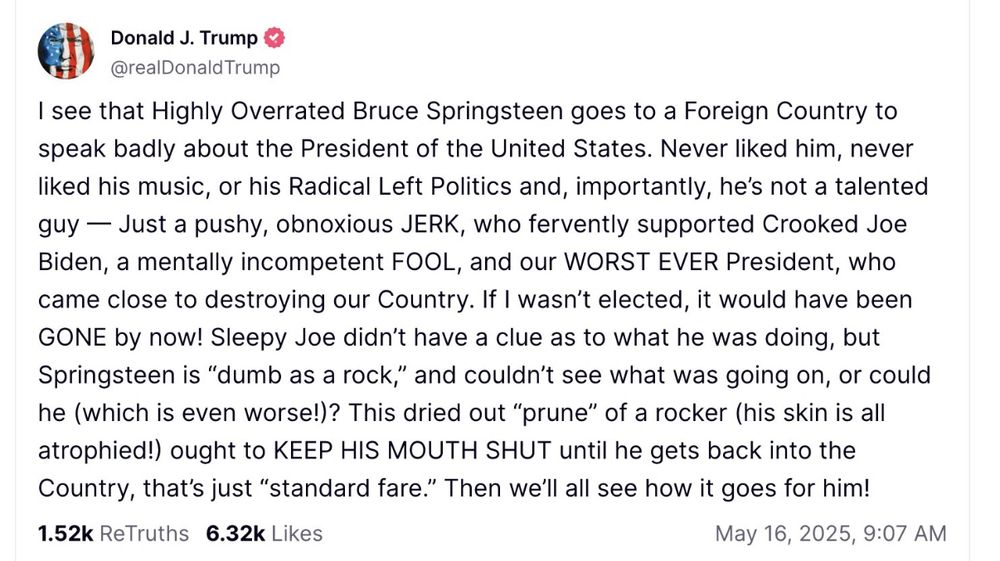
In the United States, we have him the nuclear codes.
Interested? I'll share it soon.
Interested? I'll share it soon.
It isn't normal to have frequent crashes for the OS if that's what you're referring to. The OS itself should be quite stable.
It isn't normal to have frequent crashes for the OS if that's what you're referring to. The OS itself should be quite stable.
- The OS is not as polished as iOS, but I expected that, of course. There is a lot of work to be done, but I believe AI will significantly increase development on that side, for Android, Graphene, and the wider app developer community.
- The OS is not as polished as iOS, but I expected that, of course. There is a lot of work to be done, but I believe AI will significantly increase development on that side, for Android, Graphene, and the wider app developer community.
We plan to focus more on Linux kernel security going forward.
We plan to focus more on Linux kernel security going forward.
For ARMv9 devices, we greatly improved our hardware memory tagging implementation in hardened_malloc, deployed it for the Linux kernel allocators and greatly expanded the use of PAC and BTI across the OS.
For ARMv9 devices, we greatly improved our hardware memory tagging implementation in hardened_malloc, deployed it for the Linux kernel allocators and greatly expanded the use of PAC and BTI across the OS.
This means it's probably related to their usage of requestAnimationFrame to draw something on the screen.
Would be cool though to see a company use end-user devices to do large scale AI compute (w/permission).
This means it's probably related to their usage of requestAnimationFrame to draw something on the screen.
Would be cool though to see a company use end-user devices to do large scale AI compute (w/permission).
This eliminates the possibility of a bug in Chrome, IMO.
Need someone to reverse engineer their JS. /cc @pwnsdx.bsky.social @teambi0s @x0rz.bsky.social #infosec

This eliminates the possibility of a bug in Chrome, IMO.
Need someone to reverse engineer their JS. /cc @pwnsdx.bsky.social @teambi0s @x0rz.bsky.social #infosec




